Application Security , Risk Management , Technology
Dropbox 'Hacks' Macs, Researcher Warns Dropbox Defends SQL Trick, Saying Desktop App Needs Broad Permissions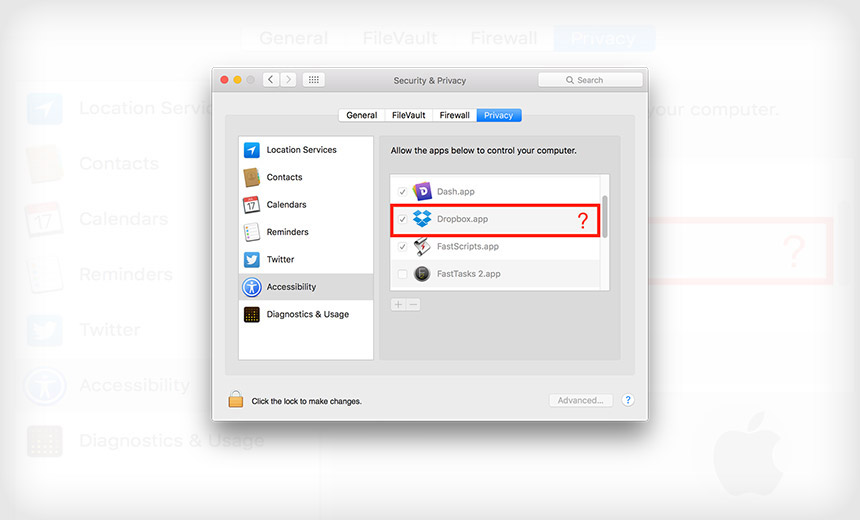 Mystery: Why doesn't Dropbox want to leave Apple's accessibility menu?
Mystery: Why doesn't Dropbox want to leave Apple's accessibility menu?A researcher's discovery of a sneaky trick used by Dropbox to gain wide-ranging access to Apple Mac OS X computers has infuriated some users, who allege the popular application is acting in a manner that's similar to malware. Dropbox officials have downplayed the finding, saying its Mac desktop app requires the modification to function correctly. But that hasn't stopped some users from vowing to never to use the file-sharing application again.
See Also: Disrupt Attack Campaigns with Network Traffic Security Analytics
The warning over the apparent liberties taken by Dropbox's software comes via Phil Stokes, a developer and freelance writer who authors the Applehelpwriter blog. Stokes, who digs deep into the workings of OS X, said he couldn't figure out why it seemed to be impossible to eliminate Dropbox from Apple's accessibility menu, which falls under the operating system's security and privacy options.
Although Dropbox asks for permission to be added to the accessibility menu, it arguably isn't honest about the its exact motivations. And once the program is in accessibility, it can't be easily removed - or at least, if it gets removed, it keeps reappearing, Stokes said. Of course, that's the kind of behavior that makes advanced users very, very nervous.
Beyond Accessibility
Here's the concern: An application inside the accessibility menu has total power over a computer. Apple introduced accessibility to allow people with disabilities, such as the blind, to still be able to use applications. Accessibility allows approved applications to perform actions on a user's behalf, such as clicking on menus and buttons and deleting files. Approved applications also get access to sensitive information, such as contacts and calendars.
 The app doesn't ask a user for permission to access the Mac OS X Accessibility menu. (Source: Paul Stokes)
The app doesn't ask a user for permission to access the Mac OS X Accessibility menu. (Source: Paul Stokes)Stokes couldn't figure why Dropbox kept appearing after he revoked its accessibility privileges, and he said the security implications of his inability to remove the application are serious.
"If Dropbox itself has a bug in it, it's possible that an attacker could take control of your computer by hijacking flaws in Dropbox's code," Stokes writes. "Of course, that is entirely theoretical, but all security risks are - until someone exploits them."
Permission Confusion
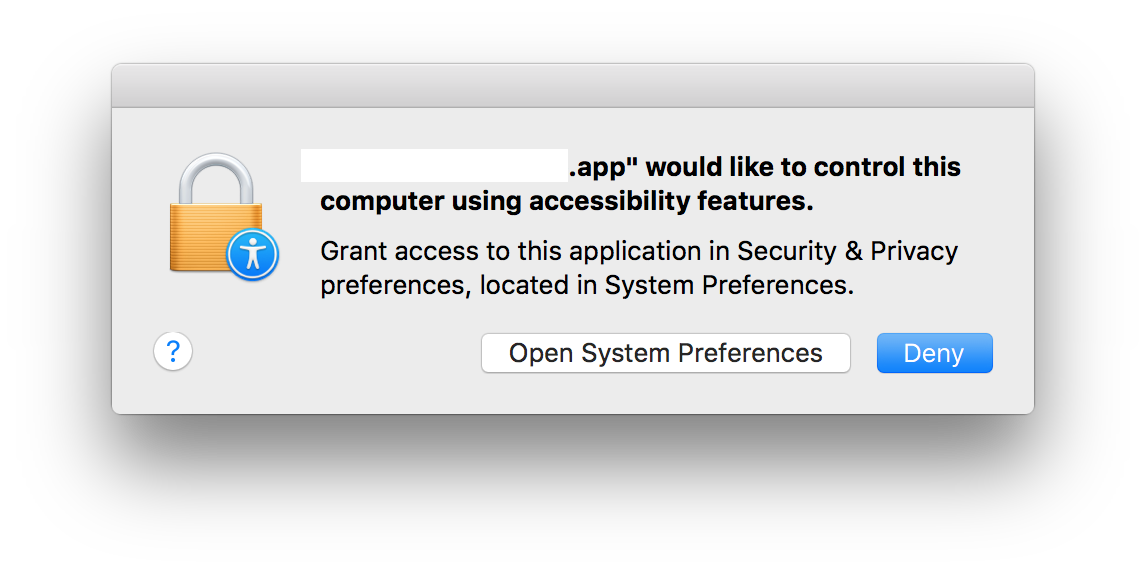
How Dropbox gets into accessibility isn't straightforward. Apple has a standard dialog box that appears when an application wants to get added to the system preferences menu. It advises that an app "would like to control this computer using accessibility features" and that access can be granted through the "security & privacy preferences."
Instead, Dropbox displays a custom-worded dialog box that asks for a user's system password. It advises that the system password is necessary "for Dropbox to work properly." But the mystery wasn't completely solved. Stokes said in his blog post that gaining access to the system password still shouldn't be enough to allow Dropbox to place itself in accessibility.
By late August, however, Stokes had found the answer. Dropbox uses the system password to then drop three binary files onto the computer. One of those binaries tampers with a SQL database called TCC, which is built into Mac OS X to track which applications are in accessibility.
"We finally hit gold, and the exact proof I was looking for that Dropbox was using a SQL attack on the TCC database to circumvent Apple's authorization policy," Stokes wrote in a second blog post.
Dropbox's slight modification to the database means that even if a user removes the Dropbox app from the accessibility menu, it will keep reappearing - a magic trick that many people would consider to be a hack.
Phil Stokes demonstrates how Dropbox overrides OS X user preferences in the security & privacy accessibility pane.Cue Backlash
After Stokes' findings reached Hacker News, Dropbox faced an immediate and strong backlash, particularly from users who are naturally prone to be suspicious over what permissions applications want.
"The only way to regain my trust at this point is providing an official explanation of what's going on with technical details," wrote a user who goes by the nickname Bicubic. "Now that I got the impression that Dropbox is doing something outside of that envelope, even if that impression is wrong, my money is going to go elsewhere, probably to a competitor."
Dropbox's Ben Newhouse, who lists his position at the company as "minister of magic," and works on the company's desktop client team, quickly weighed in on Hacker News.
The intention, he writes, has been to ensure that Dropbox functions properly across operating system updates. Apple's controls for granting permissions "aren't as granular as we would like," he writes. He also maintains that the company doesn't store a computer's system password.
But Stokes has noted that Dropbox really, really wants a user's system password, and it will pester users every time the Dropbox desktop app is launched - or the computer is restarted - until a user parts with it.
In response, Stokes noted that Dropbox appeared to work perfectly well, even if he declined to share his system password, thus calling into question Dropbox's contention that it must know a user's system password.
Dropbox declined to make Newhouse available to me for an interview.
But the company has issued a formal press statement attempting to further downplay the controversy.
Dropbox to Users: No Spoofing
"Reports of Dropbox spoofing interfaces, or capturing system passwords, are absolutely false," it says. "We realize we can do a better job communicating how these permissions are used, and we're working on improving this."
The explanation fell flat with some users, however, who say they've uninstalled Dropbox.
"I understand the desire to make your features 'just work,' but circumventing the user's privacy controls to do that is never acceptable," wrote a Hacker News commentator who goes by the name Brentdax. "Especially accessibility, which is basically a general warrant to snoop on everything the user does. You wouldn't be on my system anymore if my work didn't require Dropbox. You're going to lose a lot of trust over this, and it won't even be half of what you deserve."
The Dropbox hack's days, however, appear to be numbered. Stokes says he notified Apple last year about the issue but never heard back from the company. But he's noticed that the upcoming 10.12 version of OS X, code-named Sierra and due for release Sept. 20, blocks the trick.

