Breach Notification , Breach Response , Data Breach
'Sophisticated Attack' Siphoned Card Data for 6 Months, Retailer Warns
Eddie Bauer, an outdoor apparel retailer based in Bellevue, Wash., is warning customers that point-of-sale malware infected its retail store systems for "various dates" over a six-month period before the malware was discovered and eradicated.
See Also: 2016 Annual Worldwide Infrastructure Security Update
Eddie Bauer is owned by San Francisco-based private equity firm Golden Gate Capital and counts about 360 stores in the United States and Canada that were affected by the breach, and about 40 stores in Germany, Japan, and Southeast Asia that were not.
The company's breach notification suggests that every one of its North American stores may have been affected by what it claimed to be a "sophisticated attack." But the breach notification does not detail how many customers may have had their payment card compromised via the data breach, although the retailer says it is reaching out directly to customers who might have been affected, "by mail, a press release, and a website."
"We determined that customers' payment card information used at our retail stores on various dates between January 2, 2016 and July 17, 2016 may have been accessed," says Eddie Bauer CEO Mike Egeck in an Aug. 18 letter to customers. "Not all cardholder transactions during this period were affected. Payment card information used online at eddiebauer.com was not affected."
Eddie Bauer said attackers obtained cardholder names, payment card numbers, security codes and expiration dates for customers who bought or returned products. The retailer did not immediately respond to a request for comment about how it discovered the breach or what type of POS malware was used against it. But on July 5, the retailer told security blogger Brian Krebs, who heard reports of potential fraud at the retailer from several U.S. financial institutions, that it was not aware of any breach.
Egeck said that in the wake of the retailer learning it had been breached, it "immediately initiated a full investigation with third-party digital forensic experts to identify and contain the attack as quickly as possible" and also alerted the FBI. The retailer says the breach has now been contained.
"Out of an abundance of caution, we are offering identity protection services to all customers who made purchases or returns in our stores between January 2, 2016 and July 17, 2016," Egeck says, via Kroll.
@Crackerjen Protecting customer payment info is our top priority. We're directly notifying affected customers: https://t.co/A5sC2paBGi
Yet Another POS Malware Campaign
The retailer said that during the course of its investigation, it found that the same malware had been used to infect other organizations that use POS devices. "We learned that the malware found on our systems was part of a sophisticated attack directed at multiple restaurants, hotels, and retailers, including Eddie Bauer," Egeck says. "We are conducting a comprehensive review of our IT systems to incorporate recommended security measures in order to strengthen them and prevent this from happening again."
Security experts say that while different cybercrime gangs may employ different types of POS malware, most of it is functionally identical, unsophisticated and could be better blocked if retailers changed default passwords on their POS devices and used segmentation to better isolate POS systems (see Why POS Malware Still Works).
Eddie Bauer didn't immediately respond to a request for comment about whether its POS devices sported default passwords, and whether it employs network segmentation (see Solve Old Security Problems First).
Breach Alert: HEI Hotels & Resorts
In other POS malware news, HEI Hotels & Resorts last week began warning that anyone who used a payment card at one of 20 affected U.S. hotels that it runs - including several Hyatt and Marriott locations - may have had their card details compromised by point-of-sale malware. It's not clear if the breach is related to the Eddie Bauer attack, or to the recent warning from POS systems and services provider Oracle MICROS that revealed a breach impacting its legacy POS systems. In response, Visa issued an alert warning merchants to be on the lookout for malware attacks linked to MICROS (see Recent POS Attacks: Are They Linked?).
HEI's breach notification warns that customers at 20 hotels - ranging from the Boca Raton and Dallas Marriott to Le Meridien San Francisco and the Westin Washington D.C. may have had their payment card data exposed if they used a payment card in any of the affected hotels. According to a list of hacked hotels, the breaches began at some hotels on March 1, 2015, and lasted at some properties until June 21, 2016. HEI says all affected hotels' POS systems - including in restaurants, gift shops and spas - were potentially compromised by malware that intercepted payment card data as cards were being swiped.
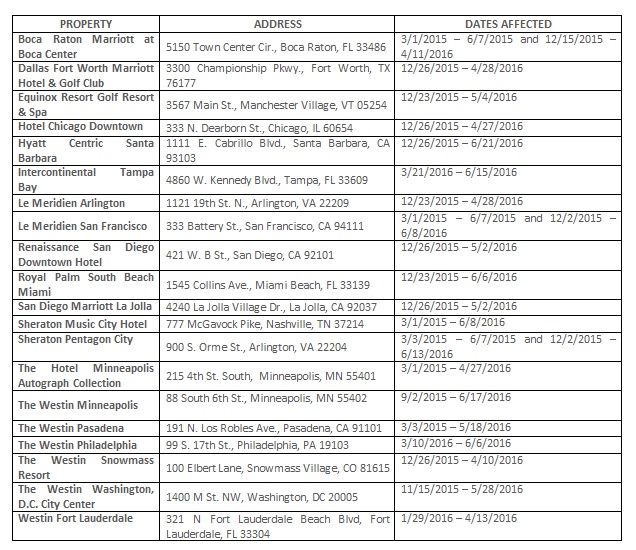 The HEI Hotels & Resorts hack attack resulted in payment card data being potentially stolen at the the listed properties, during specified dates.
The HEI Hotels & Resorts hack attack resulted in payment card data being potentially stolen at the the listed properties, during specified dates.
Based on the hotel chain's related digital forensic investigation, which it launched in June, hackers potentially compromised cardholders' names, account numbers, card expiration dates and verification codes. "We are sorry for any concern or frustration that this incident may cause," HEI says, adding that it doesn't store credit card data, and that none of its POS systems allow for PIN entry, so no PIN numbers associated with debit cards were compromised.
The hotel chain doesn't know exactly how many customers might have been affected, because they may have used their payment cards at properties multiple times, HEI spokesman Chris Daly tells NBC. But he notes that during the POS malware infection period, about 8,000 transactions occurred during the affected period at the Hyatt Centric Santa Barbara hotel in California, and about 12,800 were made at the IHG Intercontinental in Tampa, Florida.
HEI says the breach has been contained and that it's continuing to work with law enforcement. "As part of the investigation, we removed the malware and are in the process of reconfiguring various components of our network and payment systems to further secure our payment card processing systems," HEI adds. Despite that work still being in progress, the hotel claims that "individuals can safely use payment cards at our properties."
POS Malware Epidemic
HEI is just the latest in a long line of hospitality organizations warning that their systems were infected by POS malware. Other breached organizations in the sector have included Hilton, Hyatt, Omni Hotels & Resorts, and Starwood Hotels and Resorts, as well as Trump Hotels, which potentially fell victim to two separate breaches.

