Anti-Malware , Risk Management , Technology
Exploit Kits Are Targeting Zero-Day Flaw in Flash
Security experts are once again warning all Adobe Flash users to either update or uninstall the browser plug-in software to protect themselves against active exploits. The attack campaigns, which began March 31, have been exploiting a zero-day flaw in the Windows version of the software to install ransomware. Recent versions of Flash for Mac OS X, Linux and Google ChromeOS are also at risk.
See Also: Security Shouldn't be Boxed: The Cloudified Edge & End of an Era for Hardware Box Providers
Adobe has released updated versions of Flash that fix the targeted flaw, which has been designated as CVE-2016-1019. "Adobe is aware of reports that CVE-2016-1019 is being actively exploited on systems running Windows 10 and earlier with Flash Player version 20.0.0.306 and earlier," Adobe says in a security alert.
The flaw is a "type confusion" vulnerability in ActionScript, which is an object-oriented programming language designed for Flash. Type confusion refers to code failing to verify what type of object - meaning a series of coding statements - gets passed to it, which attackers can sometimes exploit to run their own arbitrary code and take control of a system.
But Adobe's latest Flash update includes fixes for 24 flaws in total, many of which are "critical vulnerabilities" that "could potentially allow an attacker to take control of the affected system," it says. The latest - fully patched - version of the Flash Player Desktop Runtime is now 21.0.0.213. Adobe recommends all users upgrade immediately.
Magnitude Exploit Kit Targets Flaw
Adobe says the in-the-wild attacks against CVE-2016-1019 were first spotted by researchers at cloud security firm Proofpoint. In a blog post for Proofpoint, the malware researcher known as Kafeine reports that the firm on April 2 found that the "Magnitude exploit kit was successfully exploiting Adobe Flash version 20.0.0.306" via drive-by attacks. With Flash version 21 now being current, the researchers suspected that the exploit kit was targeting some older Flash flaw. But after sharing the findings with other security researchers, FireEye discovered that the flaw was in fact new, after which the researchers alerted Adobe, Kafeine says.
Magnitude Exploit Kit Traffic
 A global view of Magnitude traffic, from March 31 to April 6. Source: Trend Micro.
A global view of Magnitude traffic, from March 31 to April 6. Source: Trend Micro.
Magnitude may not have the name-brand recognition of some of the most prevalent ransomware kits, such as TeslaCrypt and CryptoWall, but it's still a threat. Formerly known as Popads, Magnitude is crimeware that "in recent months ... seems to be used by only one actor," Kafeine says. He adds that the attacker had been using Magnitude to distribute CryptoWall until mid-March, then switched to distributing Teslacrypt, and since the end of March has instead been distributing Cerber, which security firm Malwarebytes describes as new but relatively advanced ransomware that's sold in part via underground Russian forums (see Why Russian Cybercrime Markets Are Thriving). As is typical with ransomware, Cerber will forcibly encrypt most files on a system, then demand bitcoins in exchange for a decryption key.
Cerber Ransom Demand
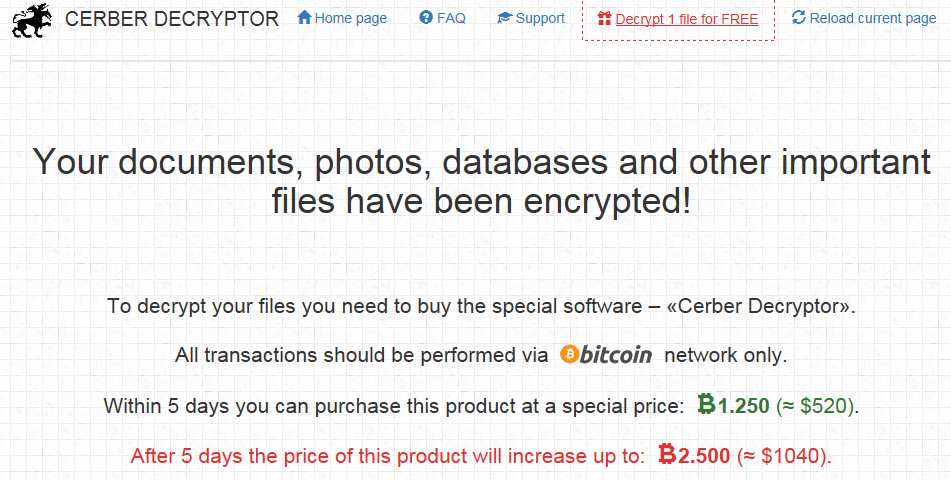 The ransom note displayed by a system that's been infected with Cerber ransomware. Source: Malwarebytes.
The ransom note displayed by a system that's been infected with Cerber ransomware. Source: Malwarebytes.
Kafeine says attackers also attempted to exploit the type-confusion vulnerabilities in Flash version 21, but failed due to a coding error. While ransomware that targeted the flaw can still cause newer - unpatched - versions of Flash to crash, it won't result in arbitrary code execution.
Nuclear Packs Related Exploit
Magnitude isn't the only exploit kit that's been attacking the Flash flaw. Researchers at FireEye and anti-malware firm ESET also discovered that on March 31, an updated version of the Nuclear Pack exploit kit began targeting the flaw and attempting to infect systems with Locky ransomware. That ransomware uses macros, hidden in document files, to disguise related malware. It has been tied to a large number of recent incidents, especially in the healthcare sector, including Methodist Hospital in Kentucky (see Hospital Ransomware Attacks Surge; So Now What?).
Malwarebytes security researcher Jérôme Segura says in a blog post that Flash remains attackers' top choice for launching drive-by attacks, because it can be used to automatically infect large numbers of PCs - and with no user interaction required. Drive-by attacks occur via "compromised sites" as well as via malvertising, he says.
Recommended Action
One option for defending against Flash attacks is to delete the plug-in, and some security experts recommend taking that approach whenever possible.
For anyone who still uses Flash, meanwhile, the prevailing wisdom is to let it auto-update whenever possible. Flash Player 11.2.x or later for Windows, as well as Flash Player 11.3.x or later for OS X, can be set to "allow Adobe to install updates," which will result in automatic updates. All Google Chrome users already see automatic updates across all platforms, as do Microsoft Edge and Internet Explorer for Windows 10 users, as well as Windows 8.1 users running Internet Explorer 11.
For anyone who sticks with Flash, researcher Paul Duckin at security firm Sophos also recommends setting the plug-in to not be allowed to execute whenever it chooses. "If you do need to keep it, make sure you keep it up to date, and use your browser's click-to-play feature (also known as ask to activate) so that Flash content doesn't run without you realizing, especially on sites you've never visited before," he says in a blog post.

