Audit , Governance , Risk Assessments
Watchdog Urges Four Agencies to Improve Implementation of Access Controls GAO's Greg Wilshusen calls on U.S. agencies to toughen access controls.
GAO's Greg Wilshusen calls on U.S. agencies to toughen access controls.A government watchdog warned four federal agencies that they must be more diligent in implementing their cybersecurity programs. Otherwise, some of the government's most sensitive information is at risk of being disclosed to unauthorized individuals.
See Also: 2016 State of Threat Intelligence Study
Although NASA, the Nuclear Regulatory Commission, the Office of Personnel Management and the Department of Veterans Affairs developed risk assessments for their high-risk systems, they have all been inconsistent in their implementation of access controls, according to report released June 21 by the Government Accountability Office, the investigative arm of Congress.
GAO also says the four agencies have weaknesses in patching software vulnerabilities and planning for contingencies because they didn't fully implement key parts of their information security programs.
Gregory Wilshusen discusses the findings of the GAO audit of four federal agencies."Until the selected agencies address weaknesses in access and other controls, including fully implementing elements of their information security programs, the sensitive data maintained on selected systems will be at increased risk of unauthorized access, modification and disclosure, and the systems at risk of disruption," Gregory Wilshusen, GAO director of information security issues, says in the report.
Audit Sought by Congressional Overseers
GAO surveyed 18 federal agencies that store and process high-impact information, which the National Institute of Standards and Technology defines as having a severe or catastrophic adverse effect on operations, assets and individuals if compromised.
The leaders of the Senate Homeland Security and Government Affairs Committee, which provides government IT security oversight, requested GAO study how federal agencies protect high-impact data. The request came after the breach of Office of Personnel Management computers that exposed the personal information of at least 21.5 million individuals, many of them holding security clearances (see Nominee Explains OPM's Recovery from Massive Breach).
During the fiscal year that ended Sept. 30, 2014, 11 of the 18 agencies GAO surveyed reported 2,267 incidents affecting their high-impact systems, with nearly 500 of the incidents involving the installation of malware. Of the federal government's 9,714 information systems in the 24 agencies covered by the Chief Financial Officers Act, 912 of them - or 9 percent - are deemed high impact.
The audit also revealed that the attacks delivered through email were deemed the most serious and frequent.
Most Serious, Frequently Identified Cyber Threat Vectors
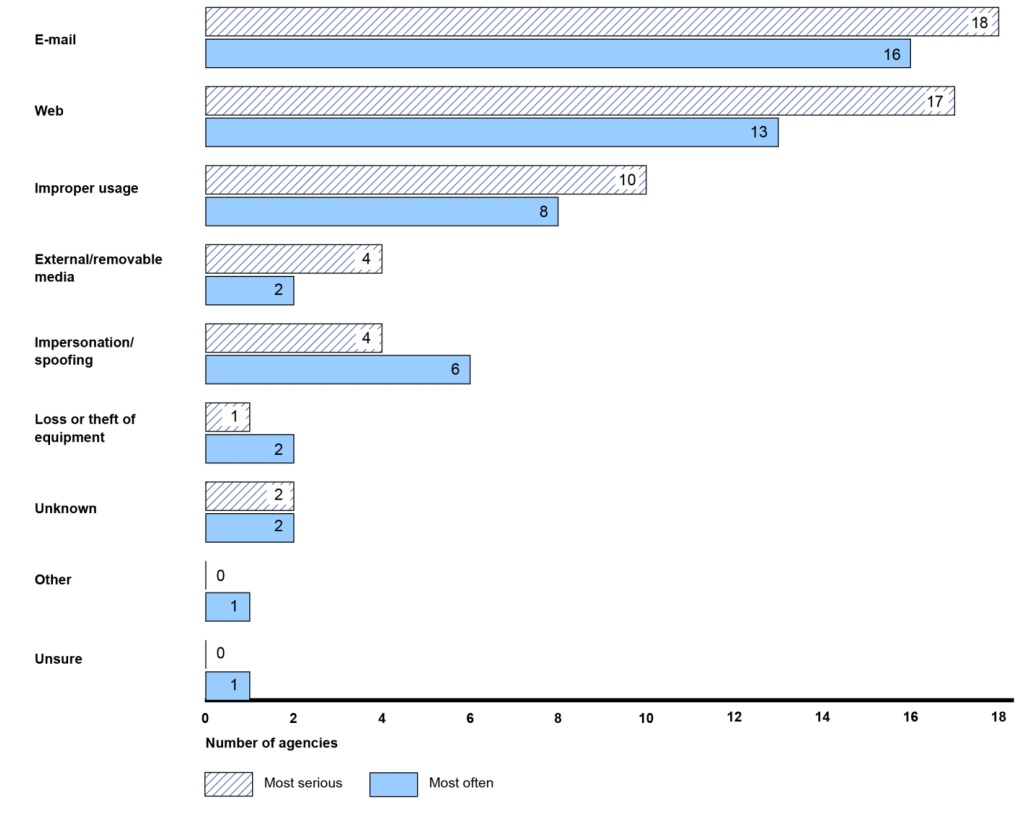 Source: GAO
Source: GAOGAO also recommended that the Office of Management and Budget, the White House organization that oversees federal agencies IT security, complete its plans and practices for securing federal systems, known as the Cybersecurity Implementation Plan (see Federal Cybersecurity Strategy Revised).
The auditors called on NASA, NRC, OPM and VA to fully implement key elements of their information security programs. The agencies generally concurred with GAO's recommendations, with the exception of OPM.
Pushback from OPM
OPM did not concur with the recommendation regarding evaluating security control assessments. David Vargas, OPM's associate CIO, says GAO failed to provide enough information to fully respond to the recommendation. But GAO contends it briefed OPM staff on its technical findings nearly two months before OPM was required to respond to a draft of the audit.
GAO also recommended that OPM provide and track specialized training for all individuals, including contractors, who have significant security responsibilities. Vargas says OPM concurs with the intent of that recommendation, but disagrees on the approach GAO suggests. He says the OPM system audited by GAO was owned and operated by a contractor, which he considers a crucial point.
"It is more appropriate and efficient for OPM to monitor IT training requirements for contractors without access to OPM's network through contractor audits and oversight, as opposed to directly providing and tracking those individuals' training," Vargas says in his response to the GAO recommendation. "OPM's IT security office currently conducts annual site visits on a sample of contractors each year and is working to improve the site assessment process to better align it to verify compliance with all the standard IT contract clauses, including those regarding contractor employee training."
The GAO study reveals how cyber threats affects the 18 agencies with high-impact systems. It shows that threats from nations and malicious insiders were the most serious. Threats posed by nations, unknown malicious outsiders and hackers/hacktivists occurred most often, as indicated, for example, by alerts or notifications.
Most Serious, Frequently Identified Adversarial Cyber Threat Sources
 Source: GAO
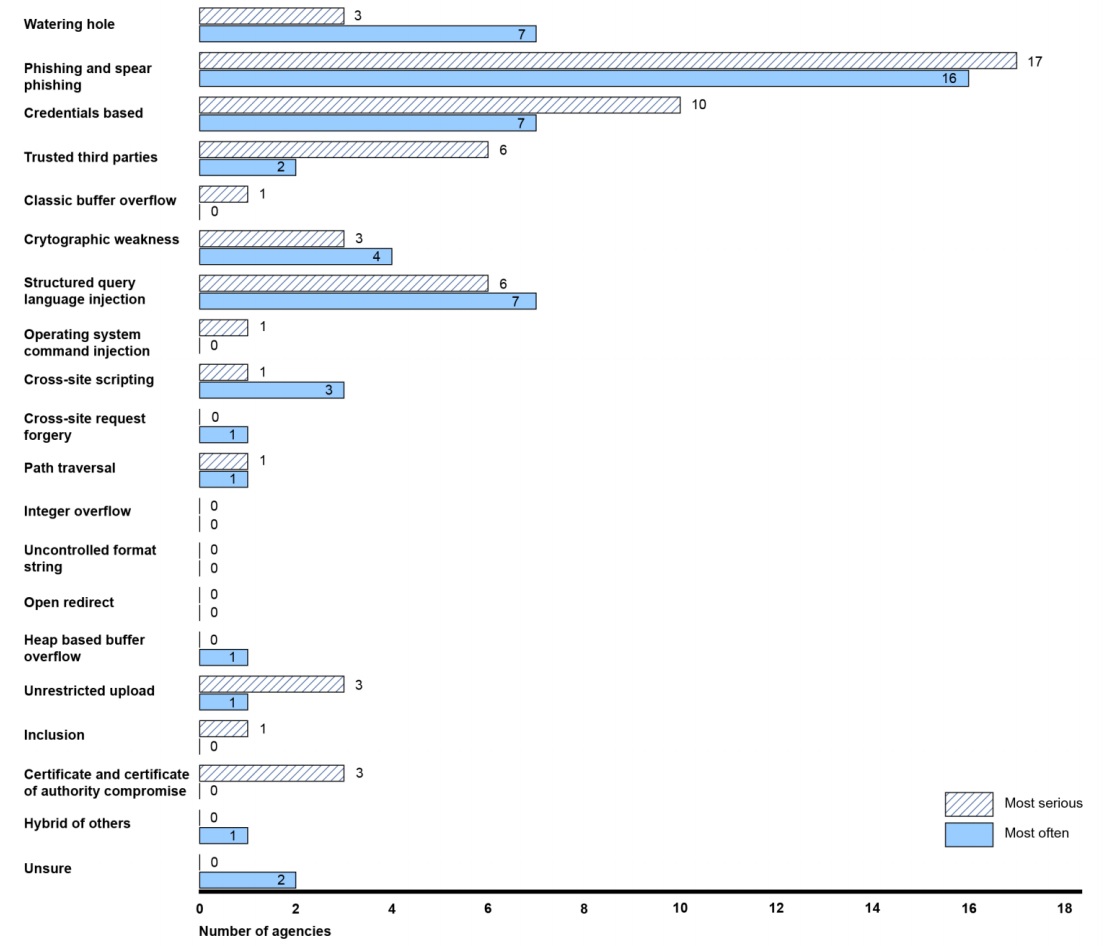
Source: GAOThe agencies also reported that phishing and spear phishing proved to be the most serious and most frequently identified method of waging cyberattacks.
Most Serious, Frequently Identified Cyberattack Methods
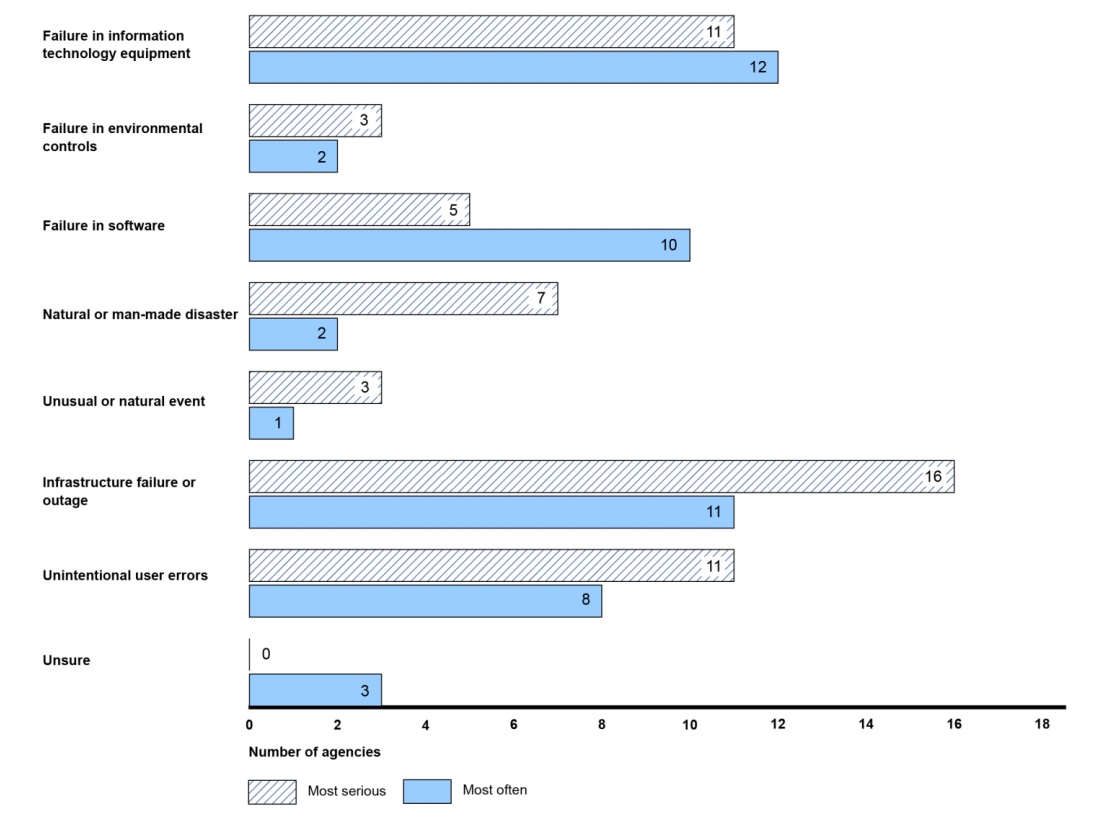
 Source: GAO
Source: GAOThe 18 agencies with high-impact systems reported that they considered infrastructure failure or outage, failure in IT equipment and unintentional user errors to be the most serious non-adversarial threat sources that affect their high-impact systems.

