Cybersecurity , Risk Management , Technology
Hack My Ride Electric Cars Join the Internet of Unsecured Things
To the list of vulnerable, Internet-connected devices, now add the world's most popular electric car: the Nissan LEAF, of which 200,000 have now been sold (see The Internet of Dangerous Toys?).
See Also: Stop Fraud, Not Customers: Focus On Good User Experience
Australian information security expert Troy Hunt announced in a Feb. 24 blog post that a month prior, after teaching a development-focused "Hack Yourself First" course in Norway, one of the seminar participants decided to take a close look at the Nissan LEAF, including a smartphone app that owners can use to remotely control aspects of their car, such as turning the heater on in the morning before they get in - no doubt a popular feature in Scandinavia.
What he and British security researcher Scott Helme found won't shock anyone who's been following information security for any length of time: He could control many features - including adjusting the climate controls and accessing trip details - in any LEAF, anywhere in the world, simply by knowing or guessing any LEAF vehicle's VIN number.
Security researchers Troy Hunt and Scott Helme demonstrate remotely hacking Nissan LEAF car features.All VIN numbers in the world have 17 digits, but the first 12 digits are the same for all LEAF vehicles, leaving just five digits - and thus 100,000 potential combinations - for would-be car hackers to brute-force guess.
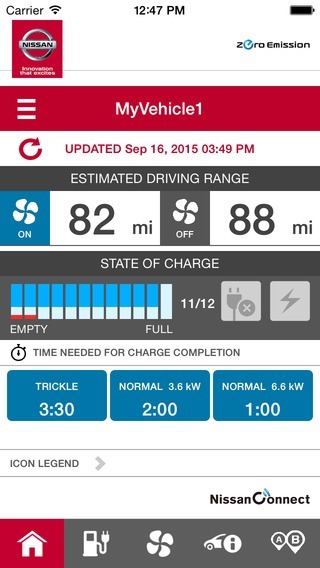 Nissan's app enables remote access to car environmental controls, trip data.
Nissan's app enables remote access to car environmental controls, trip data.Hunt says he reported the vulnerabilities directly - and privately - to Nissan on Jan. 23. But he decided to make the research public because it was being discussed on a public forum by legions of irate French Canadians, and the details were easily available to any non-native speakers via Google Translate.
"Nissan needs to fix this," Hunt says in his blog post. "It's a different class of vulnerability to the Charlie Miller and Chris Valasek Jeep hacking shenanigans of last year, but in both good and bad ways" (see Car Hacking Spurs Automakers to Share Threat Information).
Hunt says the good news is that the car's driving controls can't be hacked. But the bad news is "that the ease of gaining access to vehicle controls in this fashion .... [is] profoundly trivial," and portends long-term problems for the Internet of Cars.
"As car manufacturers rush toward joining in on the 'Internet of Things' craze, security cannot be an afterthought nor something we're told they take seriously after realizing that they didn't take it seriously enough in the first place," he says. "Imagine getting it as wrong as Nissan has for something like Volvo's 'digital key' initiative where you unlock your car with your phone."
Nissan Disables Related APIs - Mostly
In response to Hunt's post, Nissan on Feb 25 temporarily blocked APIs connected to the online app, telling the BBC that "the NissanConnect EV app - formerly called CarWings - is currently unavailable." But it denies the information security vulnerabilities pose a safety issue.
I've received a public response from Nissan: pic.twitter.com/rn6975oQw6
But Hunt notes that the approach Nissan appears to have taken - disabling access to the vulnerable APIs used by its app - doesn't appear to have disabled the functions in all countries. In comments to his blog post, some LEAF owners in Canada on Feb. 25 reported that they were still able to hack their vehicles.

