Anti-Malware , Payments , Risk Management
Now a Second Gang - Not Bangladesh Bank's Attackers - Is Gunning for Banks
A malware-wielding gang has been targeting financial firms' SWIFT software to inject fraudulent money-moving messages since at least January in "discreet campaigns" not tied to the Bangladesh Bank hack, security firm Symantec warns.
See Also: Avoid Theft of Your Privileged Credentials
The emergence of the targeted attacks, which rely on malware called Odinaff, is bad news for banks that rely on the SWIFT network to send money-moving messages. Symantec reports that the malware includes the ability to alter client-side logs used by SWIFT software. It says the attackers appear to be seeking high-value targets and attempting to avoid discovery, rather than pursuing mass-infection campaigns.
The Society for Worldwide Interbank Financial Telecommunication, as SWIFT is formally known, is a cooperative owned by 3,000 banks that bills itself as "the world's leading provider of secure financial messaging services." It's now used by more than 11,000 banks globally to process 25 million communications daily that collectively account for billions of dollars' worth of transfers.
The payoff for attackers who can inject fraudulent money-moving messages into SWIFT's network by hacking into PCs that interface with the network is clear: They can literally transfer themselves money.
A SWIFT spokesman tells Information Security Media Group that the organization is aware of the attacks and related modus operandi, as detailed by Symantec, and that its new customer security intelligence team has issued an alert to the organization's customers.
"We published related indicators of compromise and a practical example of the MO for our community earlier this summer," the spokesman says. "This work forms part of SWIFT's information sharing initiative, which has grown significantly since its launch, and which includes detailed intelligence and analysis on the modus operandi of attackers in customer fraud cases."
Life After the Bangladesh Bank Hack
Symantec's alert says at least two groups have been actively targeting SWIFT-using banks.
The first has been tied to the February hack attack against the central bank of Bangladesh that resulted in attackers stealing $81 million from Bangladesh Bank's account at the Federal Reserve Bank of New York via fraudulent SWIFT messages. That attack, and the discovery of similar, related attacks - before and after the Bangladesh Bank theft - sent shock waves through the financial services sphere, triggering concern from regulators and legislators around the world, and resulted in SWIFT taking a more active role in securing customers' use of its messaging network and related software.
Systems at Bangladesh Bank were infected by "Banswift" malware that allowed attackers to inject fraudulent money-moving messages into the SWIFT network. Attackers also employed trojanized PDF reader software that prevented details of the transactions from being printed out on the bank's printer, thus delaying the bank's discovery of the fraud.
Security experts have traced those attacks to the Lazarus Group, as first detailed in a February report into Operation Blockbuster that was coordinated by anti-fraud and analytics firm Novetta.
Inside Odinaff
The newly identified Odinaff attacks, however, work in a slightly different way and use entirely unrelated malware. For starters, Odinaff serves as a "dropper," meaning it allows attackers to download selected, additional attack tools onto victims' systems, Symantec's Security Response team says in a blog post. One such tool is a backdoor called Batle, Symantec says, which "is capable of running payloads solely in memory, meaning the malware can maintain a stealthy presence on infected computers.
"Symantec has found evidence that the Odinaff group has mounted attacks on SWIFT users, using malware to hide customers' own records of SWIFT messages relating to fraudulent transactions," the security firm says. "The tools used are designed to monitor customers' local message logs for keywords relating to certain transactions. They will then move these logs out of customers' local SWIFT software environment. We have no indication that [the] SWIFT network was itself compromised."
Symantec says this "suppressor" malware watches for "specific text strings," including dates and specific International Bank Account Numbers, or IBANs. It adds that another attack file that's been installed on infected systems can overwrite the first 512 bytes of a hard drive, which contains the Master Boot Record, or MBR, that the PC requires to boot. "We believe this tool is used to cover the attackers' tracks when they abandon the system and/or to thwart investigations," Symantec says.
The security firm hasn't revealed how many related infections it has seen, and it says it can't trace 60 percent of attacks to a specific industry. For those attacks that it has been able to trace, one-third have targeted financial services firms, Symantec says. Organizations in the United States have been most frequently targeted, followed by Hong Kong, Australia, the United Kingdom and Ukraine.
Multiple Malware Distribution Techniques
Odinaff is being distributed in multiple ways, including via spear-phishing documents that contain a malicious Microsoft Office macro. If the user has left macros disabled - as security experts recommend - then the lure document tries to trick them into turning macros on.
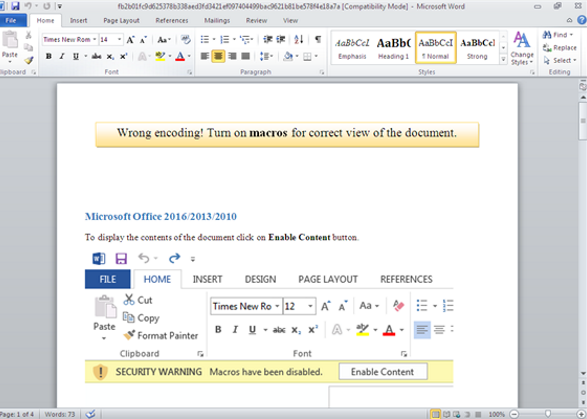 The Odinaff lure document tries to trick viewers into enabling macros in Microsoft Word (source: Symantec).
The Odinaff lure document tries to trick viewers into enabling macros in Microsoft Word (source: Symantec).Symantec says the malware is also being distributed via botnets as well as hidden inside "a Trojanized installer for AmmyyAdmin, a legitimate remote administration tool." The website that distributes AmmyyAdmin has been repeatedly hacked in recent months, with various types of malware hidden inside the software that users can download.
Potential Carbanak Tie
Three command-and-control IP addresses used to control infected Odinaff endpoints were previously used by C&C servers tied to Carbanak malware campaigns, Symantec says. The Carbanak gang was tied to at least $1 billion in fraud from 2012 to 2014, and it appears to have made a comeback starting in 2015 with a range of attacks tied to point-of-sale devices.
Of those three IP addresses, Symantec adds, one was previously used in the massive Oracle MICROS breach, which some security experts have attributed to the Carbanak gang. The reused IP addresses may only have been rented from a third-party cybercrime service provider, although Symantec said that "the infrastructure crossover is atypical, meaning it could also be a similar or cooperating group."
Another theory, however, is that the Carbanak gang has been diversifying from banking Trojan infections into targeting SWIFT-using banks and is now running a compartmentalized, highly targeted operation using Odinaff that can access and manipulate SWIFT logs and inject fraudulent money-moving messages into the SWIFT network.

