Anti-Malware , Data Loss , Encryption
Jigsaw Ransomware Adds Insult to Injury "Saw"-Themed Malware Deletes Encrypted Files While Users Watch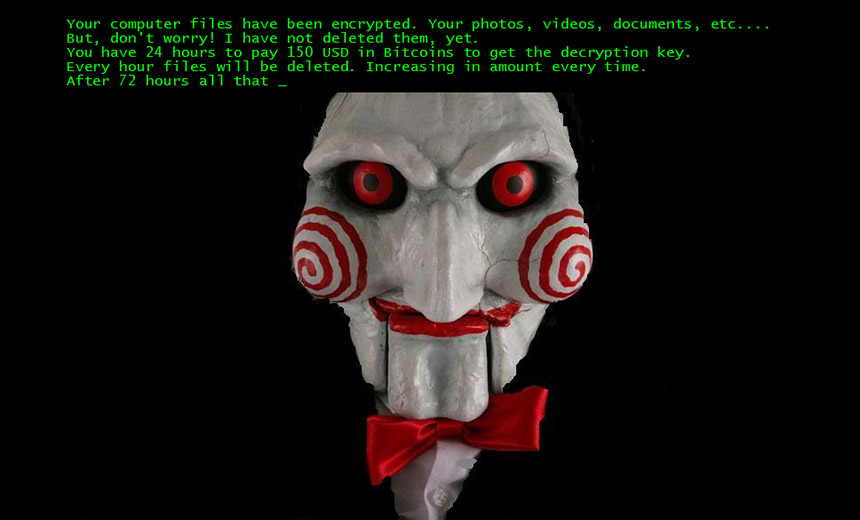 Jigsaw's ransom note. (Source: Trend Micro.)
Jigsaw's ransom note. (Source: Trend Micro.)What could be worse than a ransomware infection? How about getting infected by crypto-ransomware that taunts you by slowly deleting your encrypted files while increasing the ransom demand until you pay for the decryption key? And don't reboot your PC, or else the ransomware will delete 1,000 files at once as a reprisal.
See Also: How to Measure & Communicate Return on Cybersecurity Investments
That's the premise behind Jigsaw, a new strain of ransomware that not only tries to increase the pressure on victims to pay, but which also references the "torture porn" horror film series "Saw." In particular, the film's fictional serial killer, John Kramer, is nicknamed the Jigsaw Killer, and communicates with victims using a puppet called "Billy," which the Jigsaw ransomware author - or authors - also employ in their ransom note.
The ransomware also apes the red clock used in the movie to count down to deadlines imposed by the killer, to show victims how much time is left before more files get deleted, and the ransom demand increases. And after 72 hours, the ransomware deletes every encrypted file on the PC (see Ransomware: Is It Ever OK to Pay?).
This latest twist in ransomware appears to have been coded on March 23 and to have been used in live attacks by the end of the month, says Andy Settle, head of special investigations at Raytheon's cybersecurity business Forcepoint - formerly known as Websense - in a blog post. "This malicious program starts encrypting your files while adding, with no irony, the '.FUN' file extension," he says. "Using horror movie images and references to cause distress in the victim is a new low."
Other variants of the ransomware, meanwhile, copy and encrypt files using .KKK, .BTC, and .GWS extensions, before deleting the originals, Jasen Sumalapao, a malware analyst at Trend Micro, says in a blog post. He adds that the ransom note exists in both English-language and Portuguese-language versions, and that the lowest possible amount that victims can pay - before the demand starts increasing - ranges from $20 to $150 in bitcoins.
Jigsaw's Real-Time Shakedown
How the ransomware attack unfolds, as seen on an infected PC. (Source: Forcepoint.)No Free Lunch
Trend Micro says Jigsaw appears to be distributed via adware and "grayware" - a.k.a. "potentially unwanted applications" such as "free toolbars" - as well as via sites that host adult content. Many attacks likely begin with a "malware dropper" infection, which then downloads and installs a copy of Jigsaw being hosted on the free cloud storage service 1fichier.com. "This service has previously hosted other malware like the information stealer Fareit, as well as Coinstealer, which gathers bitcoins," Sumalapao says. "We already notified 1ficher about this incident and they already removed the said malicious URLs." Other versions of Jigsaw have also been seen at the waldorftrust.com website, he adds, noting that the ransomware has likely been bundled with applications that claim to be "cryptominer" software for using PCs to generate cryptocurrency. (Hint: they're often fake.)
Forcepoint says the Jigsaw variant that it studied was written in .NET code, which the developer attempted to obfuscate - "to prevent analysis" - and failed. As a result, security researchers have been able to recover the encryption key hardcoded into the malware, as well as 100 different bitcoin addresses to which ransoms can be paid. Settle says those addresses have now been shared with authorities (see Tougher to Use Bitcoin for Crime?).
Since the Jigsaw encryption key has been recovered, security researchers have also been able to publish instructions for removing Jigsaw infections. Of course, it's a sure bet that Jigsaw's developers will soon correct their coding errors in a new version, which is precisely what happened after the developers behind TeslaCrypt fumbled their crypto last year.
"Torture Ransomware" - Commodity Twist
Jigsaw continues the age-old practice of criminals - including online attackers - employing "psychological levers" in an attempt to trick or compel victims into parting with their money.
But functionally speaking, as with banking Trojans, point-of-sale malware and now ransomware, there's often scant difference between different malicious code families. To up the ante, attackers have in some cases begun targeting not just individual PCs, but entire enterprises, including hospitals, looking for bigger one-off ransom payments.
Taking a page from the consumer-goods industry, meanwhile, some attackers are instead focusing on branding. "These days, the name of the crypto-ransomware game is to add 'unique' features or 'creative' ways to instill fear and put more pressure to users to pay up, despite the fact that, when it comes to their technical routines, there's not much difference among these malware," Trend Micro's Sumalapao says.
Enter "torture ransomware." And the fact that we've gotten to the point where ransomware developers are coding horror-movie variations demonstrates not just the relative ease of creating this type of malware, but the incredible profit potential.
Beat the Odds
As always, security experts' anti-ransomware advice remains the same, with or without attackers employing ransom notes featuring sadistic puppets named Billy:
Maintain up-to-date backups. Ensure backups are stored offline, so ransomware can't reach it via connected, network-based or cloud-based drives. Regularly test backups. Run anti-malware software to block known strains of ransomware. Keep all applications and operating systems up to date. Don't fear the ransomware.For more extensive advice, see security expert Bart Blaze's list of top-notch ransomware defenses for both individuals and organizations. In horror-movie terms: Prepare, so you don't have to pay.

