Endpoint Security , Network & Perimeter , Technology
Security Experts See Surge in Malware Using JavaScript to Evade Defenses
After channeling horror films and holding control of smart TVs for ransom, the latest ransomware innovation du jour involves attackers crypto-locking files using nothing more than JavaScript code (see Malware, Ransomware Thrive Despite Criminal Prosecutions).
See Also: Unite & Disrupt: Mitigate Attacks by Uniting Security Operations
The JavaScript ransomware, which its developers named RAA, was discovered by two security researchers. One is known as JAMESWT_MHT, who's a member of a group that calls itself the Malware Hunter Team, while the other is benkow. The researchers flagged the malicious code via Twitter, noting that it appears to be "100 percent" written in JavaScript.
Because JavaScript doesn't include any strong cryptographic capabilities, the malware uses the CryptoJS library to forcibly encrypt a number of types of files using AES-256 encryption, then deletes the originals, the researchers tells technology blog BleepingComputer. The malware also searches for all external and network-attached drives to which the PC has access and can encrypt those too, the researchers say.
RAA also includes a version of the Pony malware embedded inside of it, which RAA also installs on an infected PC, according to an analysis of the malware published by ReaQta, a cybersecurity firm that was formed in 2014 by former employees of the Milan, Italy-based nation-state spyware shop Hacking Team.
While Pony can be used to download additional pieces of malware, for the RAA infection, it's also configured to steal passwords. "This malware can collect browser passwords and other user information from an infected machine and is usually used by hackers to gather critical information on infected systems," researchers from security firm Trend Micro say in a blog post. While Pony often uses behavior associated with banking Trojans, such as stealing access credentials for online accounts, at least to date, RAA's version of Pony doesn't appear to have been doing this.
After the ransomware encrypts files and reboots, Pony then gets executed, while end users see a ransom note written in Russian, according to ReaQta (see Please Don't Pay Ransoms, FBI Urges). "The ransomware asks for 0.39 bitcoins [$300] and due to the language of the refund information file, it's clear that the targeted country is Russia," ReaQta says.
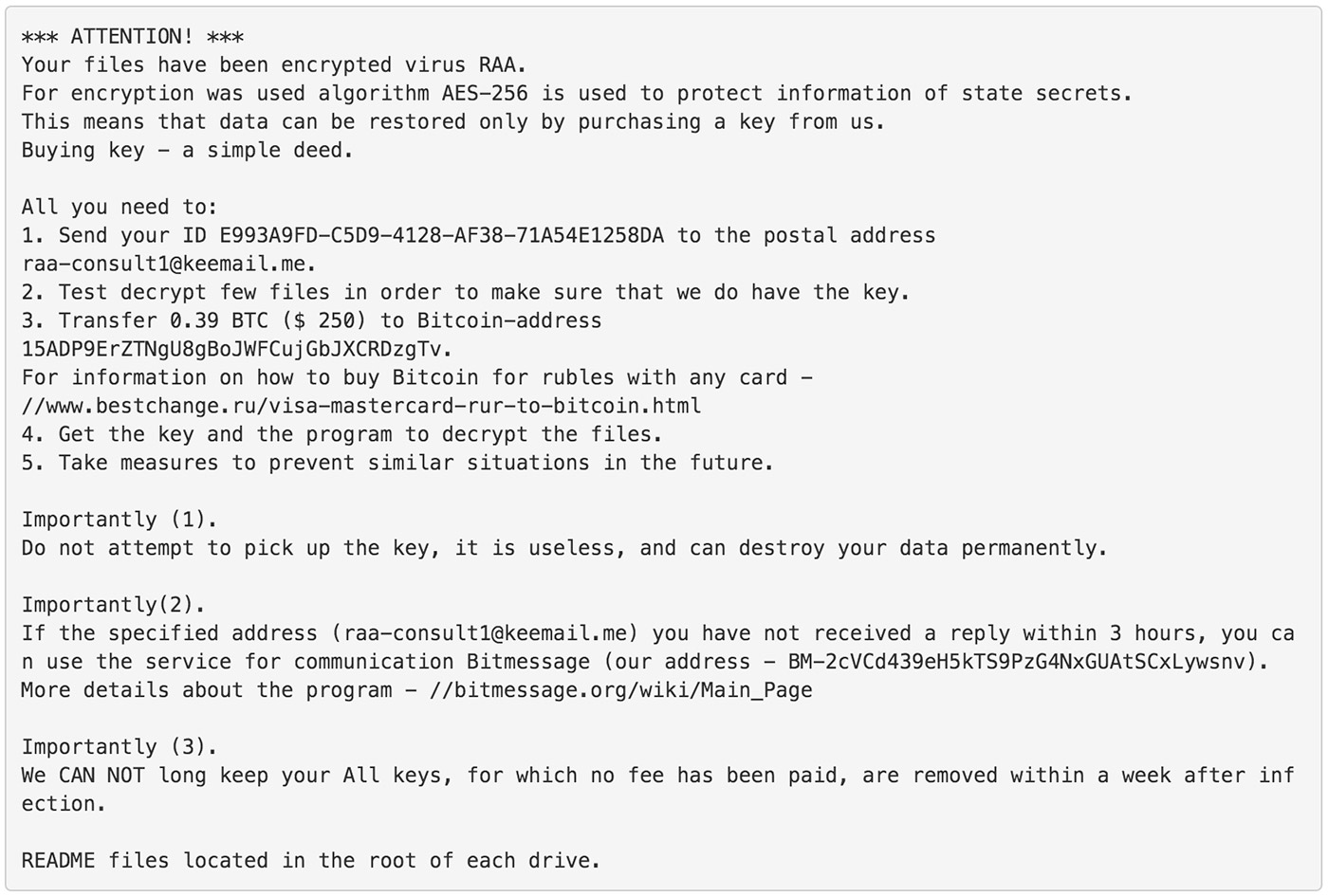 Ransom demand issued by RAA, which is 100% built from JavaScript. Ransom note translation (from Russian) source: BleepingComputer.
Ransom demand issued by RAA, which is 100% built from JavaScript. Ransom note translation (from Russian) source: BleepingComputer.
But as Trend Micro notes: "It's only a matter of time until it's distributed more widely and localized for other languages."
SANS Sounds Warning
The arrival of the JavaScript ransomware comes as the SANS Institute warns that it's seen an overall uptick in exploit kits using JavaScript to infect systems with malware.
"If the JavaScript arrives in an inbound email, and one of your Windows-based users clicks it, it doesn't execute in the browser; it executes inside of the Windows shell," says Rob VandenBrink, who's an Internet Storm Center handler for SANS, as well as a senior consulting engineer at drug and diagnostic discovery company Compugen. To entice users to click on these files, he says many attackers will name files attached to spam messages using double extensions - such as "corporate layoffs.doc.js" - to make the file appear to be an Office document or PDF file.
 Spot the malicious JavaScript attachments. (Hint: All.) Source: SANS Institute.
Spot the malicious JavaScript attachments. (Hint: All.) Source: SANS Institute.
Blocking JavaScript Malware
Security experts say enterprise administrators can apply some relatively easy defenses against malware - including ransomware - that's been written in JavaScript. VandenBrink suggests these three steps:
Block JavaScript attachments: "Out of the gate we should strip out attachments of type .JS in emails at the spam gateway - there's no good reason to be emailing JavaScript files in and out of the organization, in almost all cases," he says. Re-associate JavaScript files: In Windows, associate JavaScript files on all systems with an application that won't execute the file, such as Notepad. This protects against any business partners "who might be whitelisted in the spam filter" or insiders - because "internal mail doesn't typically go through the spam filter" - who might unwittingly receive or transmit malicious JavaScript files. Use Group Policy: IT administrators can also force-block JavaScript from executing in the Windows shell on every PC inside an organization using Windows Group Policy, VandenBrink adds.While forcibly blocking some types of technology, such as scripts, can have unintended effects, VandenBrink says that in most cases, no user needs to be running JavaScript at the Windows shell level.

