
Two new malware reports - one from security researchers at technology giant Cisco, another from cybersecurity firm FireEye - demonstrate how developers continue to refine their malicious code to maximize its information-stealing and extortion potential.
See Also: Healthcare Breaches - The Next Digital Epidemic
Malware that's tailored to steal money has usually been designed for maximum stealth, and FireEye has just detailed a malware family called "Nemesis," which is programmed to run when a PC starts up, before the operating system gets loaded. That makes the malware especially difficult to either detect or eliminate, and the longer the malware stays undetected, the greater the amount of sensitive data attackers can potentially exfiltrate.
Increasingly, however, attackers seeking maximum profits use a one-two punch: First they infect systems with malware designed to steal financial and online account data, typically by using an automated exploit toolkit such as Angler, Neutrino or Nuclear Pack. After a suitable period of time for ransacking infected systems, many attackers then deploy ransomware to forcibly encrypt all user data, after which they demand a one-time payment - often payable in bitcoins potentially worth hundreds of dollars or more - to provide the decryption key.
Security experts and law enforcement officials recommend never paying ransoms, as well as maintaining offsite, disconnected backups so that any ransomware-infected systems can be easily restored.
Inside CryptoWall 4
One of the most notorious types of ransomware is CryptoWall, which is used by multiple criminal groups, and which its developer continues to refine. The new version of CryptoWall - version 4 - was first spotted Nov. 2, attached to malicious spam (see Refined Ransomware Streamlines Extortion). By the end of November, however, security researchers were warning that multiple exploit kits that had been installing CryptoWall version 3 on victims' computers had upgraded to CryptoWall 4.
Researchers from the Cisco Talos security intelligence and research group say in a Dec. 10 blog post that CryptoWall 4 includes several major changes:
Streamlined crypto: New algorithms are used to encrypt the user data that gets held for ransom, although the malware continues to exclude specific directories and file types to ensure operating system stability so "the compromised user can still use their machine to pay the ransom," the researchers note. Disabling backups: The ransomware disables and deletes all automatic backup mechanisms built into Windows, "making it almost impossible to recover encrypted files without having an external backup," they say. Language check: The malware determines the language settings of the compromised system, using undocumented API calls.According to the malware samples analyzed by Cisco Talos, the language check is conducted to see if the system is using an "unsupported language," which currently includes Russian, as well as Armenian, Azeri, Belarusian, Georgian, Kazakh, Kyrgyz, Ukrainian and Uzbek. "This clearly shows the adversaries want to exclude certain regions from infection," the researchers say.
Needs to Phone Home
If no unsupported language is detected, the malware will install itself and then attempt to contact a command-and-control server to retrieve a public RSA key that it uses to encrypt user data, researchers say. Until it reaches the C&C server to download the key, however, the researchers note that the malware won't "harm" the system. "Here is a weak point of CryptoWall 4: If a strong firewall or IPS [intrusion prevention system] is able to intercept and block the CryptoWall 4 packets, the infection will not continue."
But if the malware should successfully encrypt the user's PC, "there is no known way to recover the private key and decrypt it without paying the ransom as the RSA private key is never managed by the victim's workstation," instead only residing on the attackers' infrastructure, the researchers say. The malware is also designed to reinstall itself upon reboot and encrypt any new files the user may have created since the last round of forced encryption.
Once ransomware such as CryptoWall successfully encrypts user data, the malware is no longer shy about advertising its presence, with some variants flashing a message onscreen that reads: "Congratulations!!! You have become a part of large community CryptoWall." Of course, the malware is psychologically designed to compel victims to do what attackers want.
CryptoWall's Welcome Message
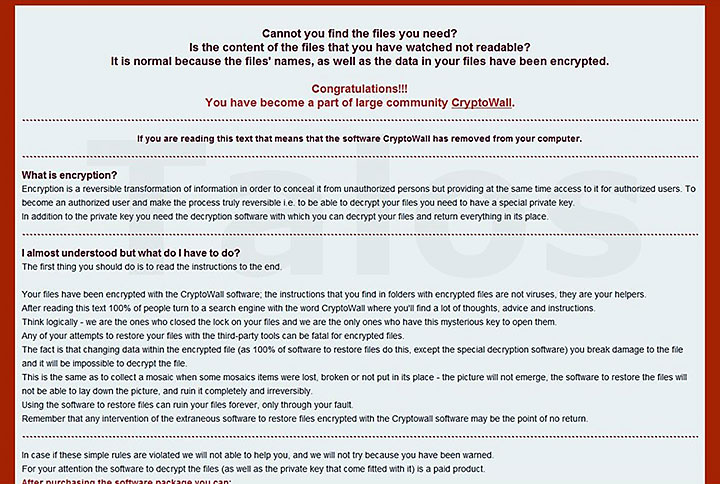 Once CryptoWall has encrypted all user data on an infected system, it no longer hides. (Source: Cisco Talos.)
Once CryptoWall has encrypted all user data on an infected system, it no longer hides. (Source: Cisco Talos.)Nemesis Targets Financial Information
Many other types of malware, however, are designed to evade detection, thus giving attackers a greater chance to steal sensitive data or press the endpoint into service as a spam relay or node in distributed denial-of-service attacks. For example, cybersecurity firm FireEye says that it has discovered a bootkit utility being used by a criminal group that's been tied to attacks against financial organizations. Variants of the malware are designed to run on all 32-bit and 64-bit versions of Windows including XP and newer.
Bootkits infect a device's master boot record, allowing them to load before the operating system gets loaded. That makes bootkits relatively difficult to either detect or eradicate. Some bootkits can even present a fake Master Boot Record when anti-virus programs attempt to scan it, according to security firm Kaspersky Lab. Such malware can persist even after reinstalling an operating system on the device.
A group dubbed "FIN1" by FireEye has been tied to a "malware ecosystem" of various tools and files that the attackers refer to as Nemesis, which have been designed to infect systems and steal financial information, including payment card data, to commit fraud. The group "is known for stealing data that is easily monetized from financial services organizations such as banks, credit unions, ATM operations, and financial transaction processing and financial business services companies," FireEye says. The group's custom tools appear to have Russian language settings, it adds, thus suggesting that the attackers "may be located in Russia or a Russian-speaking country."
FireEye says it first discovered the malware in September while conducting an investigation at an organization in the financial industry. While FireEye did not disclose when the organization was first infected with Nemesis malware, it reports that attackers continued to push updates to the malware. In early 2015, meanwhile, the attackers pushed a variant that includes a utility that's designed to modify the legitimate Volume Boot Record - which gets stored on each hard drive partition and loaded by the MBR - thus allowing the utility, which it calls "Bootrash," to load before the operating system gets loaded.
"This is a really sneaky one," University of Surrey computer science professor Alan Woodward says about the malware, via Twitter.
The VBR, in turn, begins loading Nemesis components, including C&C functionality, as well as code that can be used to do everything from log keystrokes and capture screenshots to transfer files and inject new processes into Windows. The bootkit also includes the ability to restore the original boot sector, "in the event that the threat actors wish to remove the hijacking process," FireEye says, although it still leaves signs of infection, including the custom, virtual file system and backup VBR that Bootrash creates.
This isn't the first time that malware that includes bootkit functionality has been detected, as FireEye notes. Previously seen financial bootkits include Rovnix and TDL4, a.k.a. Olmarik. In 2012, cybersecurity firm Mandiant - bought by FireEye in 2013 - observed an advanced persistent threat group, believed to be operating from China, using an MBR bootkit called "Rockboot" to infect organizations. Related attacks, it says, did not target organizations in the financial services industry, but instead were designed "to steal intellectual property from the victim organization."
Advice: Physically Wipe Affected Systems
Given the danger posed by bootkits, FireEye recommends that organizations actively look for them whenever responding to suspected breaches and then completely wipe any bootkit-infected systems.
"Incident responders will need tools that can access and search raw disks at scale for evidence of bootkits," it says. "Similarly, reinstalling the operating system after a compromise is no longer sufficient. System administrators should perform a complete physical wipe of any systems compromised with a bootkit and then reload the operating system."

