Anti-Malware , Endpoint Security , Technology
Now Ransomware Locks Smart TVs Android Malware Demands iTunes Gift Cards as Ransom Payment
First the hackers came for our credit cards. Now they're taking control of our TVs.
See Also: Unlocking Software Innovation with Secure Data as a Service
Security researchers have spotted an updated strain of ransomware that's designed to infect and lock Android devices, including mobile phones, tablets as well as smart TVs (see Why 'Smart' Devices May Not Be Secure).
The malware is known as FLocker - short for "frantic locker" - and first appeared in May 2015, Trend Micro security researcher Echo Duan says in a blog post. "The latest variant of FLocker is a police Trojan that pretends to be 'U.S. Cyber Police' or another law enforcement agency, and it accuses potential victims of crimes they didn't commit. It then demands $200 worth of iTunes gift cards."
In other words, attackers are robbing from Android to pay for Apple, or at least the ability to launder stolen funds by selling the iTunes gift cards, for example via eBay.
To be clear, end users have to be tricked into downloading and executing the ransomware, as well as allowing it to have admin-level rights. But as previous malware infections have demonstrated, disguising attack code - for example by running spam campaigns with data pulled from LinkedIn profiles that include attached malware, to claiming that software attached to a phishing message is a TV firmware update - will trick at least some recipients (see Malware, Ransomware Thrive Despite Criminal Prosecutions).
Once installed, the malware doesn't unleash havoc indiscriminately. "When launched for the first time, FLocker checks whether the device is located in the following Eastern European counties: Kazakhstan, Azerbaijan, Bulgaria, Georgia, Hungary, Ukraine, Russia, Armenia and Belarus," Duan says. "If the device detects that it is located in any of these locations, it deactivates itself."
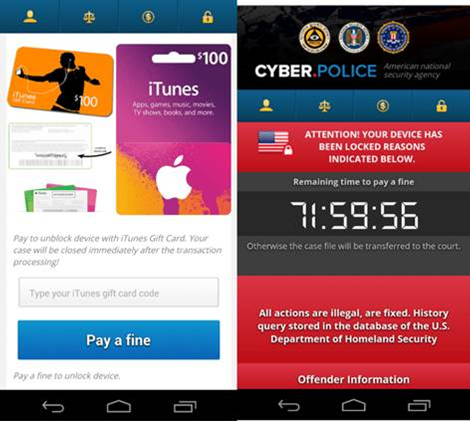 FLocker - Android malware's ransom page. (Source: Trend Micro)
FLocker - Android malware's ransom page. (Source: Trend Micro)
From Russia, With Love?
The malware's block zone offers a big clue, of course, to the origins of its developer (see Russian Cybercrime Rule No. 1: Don't Hack Russians).
Thankfully, variants of the malware seen to date cannot automatically execute, Trend Micro says. "If FLocker reaches a compatible target, it runs its routine 30 minutes after infecting the unit. After 30 minutes, it starts the background service which requests device admin privileges immediately," Duan says, in what appears to be an attempt to bypass any security tools that may be installed on the device.
Security experts have long recommended wiping and restoring - from a recent, known-good backup - any Android mobile device that suffers a malware or ransomware infection.
Where televisions are concerned, however, such an approach isn't feasible. Should an Android TV become infected with FLocker, "we suggest [users] contact the device vendor for solution at first," Duan says. Another option, detailed in full on Trend Micro's blog, is to put the device into debugging mode and launch an ADB shell to run a command that will kill the ransomware process, and then deactivate the lock screen, revoke the app's admin-level privileges and delete the application. Obviously, less advanced users might have difficulty executing that maneuver.
I Spy Internet-Connected Microphones
This ransomware attack isn't the first time that our televisions have potentially been turned against us. Earlier this year, for example, the privacy policy for Samsung's Smart TVs came to light, revealing that it allows anything said within range of the television's microphone to be transmitted to unnamed third parties (see Slouching Toward 1984). Samsung quickly attempted damage control by claiming that the information would never be used for marketing purposes, and noting that a microphone icon appears on screen whenever it's activated.
Of course, as everyone who puts a Band-Aid over their webcam knows, hackers can remotely activate such features to capture live audio or video while disabling any visual notifications that they've been remotely activated.
My webcam band-aid made it to the Sydney Morning Herald: http://t.co/ysWwzaihJp
Attack of the NSA-Pwned TVs
TVs aren't the only digital devices likely to be so targeted. Richard Ledgett, the U.S. National Security Agency's deputy director, last week said at a conference on military technology that his agency is looking into both medical devices and Internet of Things devices as potential signals intelligence targets, meaning sources that can be monitored to generate useful data.
Medical devices could be "a niche kind of thing ... a tool in the toolbox," Ledgett said, adding that there were easier ways to keep track of suspected terrorists or foreign intelligence agents, the Intercept reports.
And in response to a question about whether the Internet of Things is "a security nightmare or a signals intelligence bonanza," he said that it's "both."
"As my job is to penetrate other people's networks, complexity is my friend," Ledgett said. "The first time you update the software, you introduce vulnerabilities, or variables rather. It's a good place to be, [from] a penetration point of view."

