Anti-Malware , Encryption , Technology
Kansas Heart Hospital Pays Ransom, Gets Told to Pay Again
Kansas Heart Hospital, based in Wichita, fell victim to a ransomware attack on May 18 and chose to pay the ransom attackers were demanding. But then the hospital was told that to regain full access to files, it would have to fork over an even bigger ransom.
See Also: Unite & Disrupt: Mitigate Attacks by Uniting Security Operations
So reported CBS-affiliated television station KWCH, noting that the hospital - which had a pre-prepared ransomware response plan in place - opted to not pay any further ransoms.
Kansas Heart Hospital "felt [that this was] no longer ... a wise maneuver or strategy," Dr. Greg Duick, the hospital's president, told KWCH.
The hospital couldn't immediately be reached for further comment on the circumstances surrounding the ransomware outbreak or how much the hospital did pay to attackers. "I'm not at liberty, because it's an ongoing investigation, to say the actual exact amount," Duick told KWCH. "A small amount was made."
Duick added that the hospital's pre-prepared backup plan meant that affected systems could be - and were in the process of being - restored by the hospital's IT staff. "That plan went into immediate action. I think it helped in minimizing the amount of damage the encrypted agent could do," he said. "The patient information never was jeopardized, and we took measures to make sure it wouldn't be."
The Kansas Heart Hospital outbreak follows a surge in ransomware attacks against organizations of all sizes, as well as individuals.
Security experts say many ransomware attacks are random. "Since the average ransom demanded from an individual user is relatively low - typically a few hundred dollars, if that - threat actors distributing ransomware typically follow the 'spray and pray' tactic of sending out as many lures as possible - emails with malicious attachments or links to malicious websites, for example - to maximize their potential gains," researchers at threat intelligence firm FireEye say in a recent blog post. The researchers note that while ransomware attacks have been steadily increasing, beginning in March they saw a massive spike in related infections.
But some ransomware-using gangs have been launching more targeted attacks, often demanding relatively higher ransoms. In February, for example, Hollywood Presbyterian Medical Center acknowledged paying a $17,000 ransom to regain access to data that attackers had forcibly encrypted.
"The targeting of hospitals is no surprise," the FireEye researchers say. "Budget dollars often go toward surgery wards, emergency care centers and supplies for a large number of patients - not security. This makes for a tricky issue, since hospitals cannot operate without the necessary patient data stored in their systems."
Preparation Helps
Security experts say the best way to mitigate the impact of a ransomware attack is to prepare in advance, in part by running up-to-date anti-virus engines and signatures on all systems and ensuring that all critical data gets backed up to servers that aren't connected to the same network, so that a ransomware outbreak can't successfully encrypt them as well.
But even well-prepared organizations will typically face some type of disruption following a ransomware outbreak. In February, for example, Lukas Hospital, based in Neuss, Germany, reported that it had been hit with TeslaCrypt 2.0 ransomware, and that it had complete backups of all systems in place. But the hospital estimated that after its systems were infected, it might take 48 hours in total before its IT environment was back to normal, after it took all systems offline as a preventative measure, before wiping and restoring them. As a result, the institution said that it had rescheduled about 20 percent of its surgeries and temporarily shifted less critical care to other hospitals.
Security experts say that it's up to every individual ransomware victim whether to pay a ransom. And at least in the United States and Western Europe, there are no laws that prohibit doing so (see Ransomware: Is It Ever OK to Pay?). As the Kansas Heart Hospital episode demonstrates, however, paying a ransom doesn't guarantee that victims will actually regain access to their encrypted files.
TeslaCrypt Shuts Down
In the case of new TeslaCrypt victims, however, there is now a way to decrypt files without paying the ransom, thanks to TeslaCrypt's developers having published their encryption key, together with an apology to victims (see Master Key to TeslaCrypt Released by Ransomware Gang). More recently, the gang has even linked directly to a related decryption tool subsequently created by security researchers.
Possible explanations for this surprise turn of events - beyond contrition - include the developers having built a new type of ransomware, or perhaps even having been hacked by a rival gang, "who spilled the master key to ruin their rivals' business," says researcher Paul Ducklin at security firm Sophos, in a blog post.
But the release of the decryption key follows TeslaCrypt's developers apparently having wrapped up their related operations recently, with many ransomware distributors having switched to using CryptXXX ransomware instead, according to the Bleeping Computer forum.
CryptXXX Takes Off
CryptXXX, meanwhile, has been receiving a number of updates recently, including one that arrived following the TeslaCrypt key release, according to a blog post from researchers at security firm Trend Micro.
To date, CryptXXX has been distributed in the wild primarily via legitimate but compromised websites, as well as via malicious advertisements tied to Angler exploit kit, the researchers say. In both cases, Bedep ad-fraud malware is used to also drop a copy of CryptXXX, which is designed to encrypt files while also blocking access to the PC, via a lock screen.
"What makes CryptXXX difficult to stop is that it runs alongside a watchdog program," the researchers say. "CryptXXX runs two simultaneous routines; one that encrypts, and the other to detect abnormal system behavior. When the watchdog detects abnormal system behavior that halts the encryption process, it restarts the encryption routine. This results in a cycle of stopping the malware, and the watchdog restarting the malware."
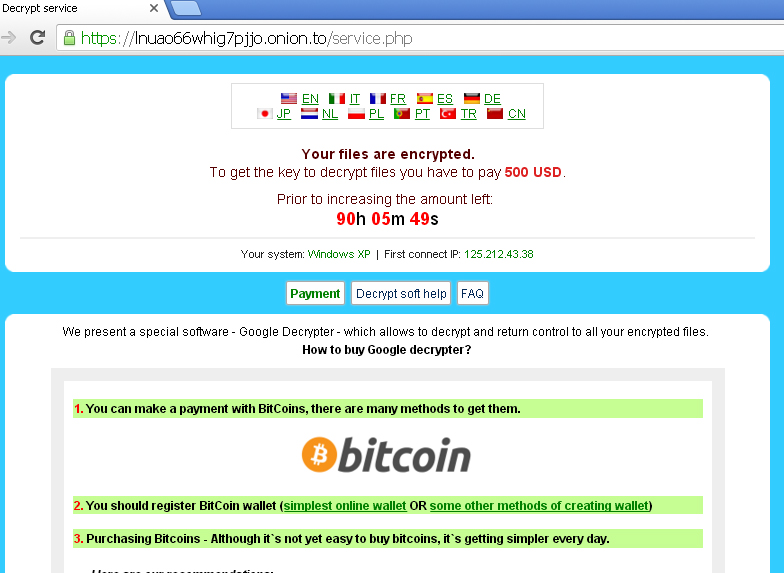 The CryptXXX ransom demand gives victims 90 hours to pay, before doubling the amount. (Source: Trend Micro)
The CryptXXX ransom demand gives victims 90 hours to pay, before doubling the amount. (Source: Trend Micro)
Many types of ransomware double their ransom demand every 24 hours until users pay, although there are some variations on that routine, such as deleting a swath of files every hour until victims pay (see Jigsaw Ransomware Adds Insult to Injury). But CryptXXX, for whatever reason, gives users 90 hours or more to pay the ransom, the Trend Micro researchers note, before then demanding double the amount. As that demonstrates, no matter the explosive growth of ransomware, different gangs will employ different strategies when it comes to trying to compel victims to pay.

