Breach Response , Data Breach , Encryption
Ransomware Gang Allegedly Dumps Rival's Crypto Keys Leak of 3,500 Chimera Crypto Keys Claimed by Petya Ransomware Developers
Honor among thieves? At least in the ransomware space, don't bet on it.
See Also: From Authentication to Advanced Attack Vectors: Top Trends in Cybercrime in Q1 2016
Witness the Petya ransomware gang this week claiming to have released 3,500 crypto keys stolen from developers behind the rival Chimera ransomware project.
"It should not be difficult for anti-virus companies to build a decrypter with this informations (sic)," the Petya developers said in a post to Pastebin that includes a dump of the alleged keys, in hex format.
The dump was first announced July 26 via a tweet from @JanusSecretary, which appears to be the handle of the Petya developers.
Security firms have yet to validate whether the alleged RSA private keys are legitimate. But multiple security experts that I've contacted tell me they're aware of the dump and currently reviewing it.
Most ransomware works by forcibly encrypting - or "locking" - important files on a PC, deleting the original copy, then delivering a ransom note offering to exchange a decryption key for bitcoins. Well-prepared victims can wipe their system and restore from an offline backup. Others, however, are often left with the choice between paying the ransom - and funding attackers - or else kissing their data goodbye. But a new public-private effort - a portal called "No More Ransom" - aims to give victims a third option, by providing ransomware decryptors whenever possible. With luck, these keys can be used to decrypt any system that was infected with Chimera, and a related tool made available via the portal.
"Checking if the keys are authentic and writing a decryptor will take some time - but if you are a victim of Chimera, please don't delete your encrypted files, because there is a hope that soon you can get your data back," security researchers at Malwarebytes say in a blog post.
Developers Claims to Have Hacked Rival
The Petya Pastebin post also sheds light on how the alleged encryption keys were obtained. "Like the analysts already detected, Mischa uses parts of the Chimera source [code]," the post reads. "We are NOT connected to the people behind Chimera. Earlier this year we got access to big parts of their deveolpment (sic) system, and included parts of Chimera in our project."
On a related note, Chimera appears to now be defunct, according to the Bleeping Computer anti-ransomware forum.
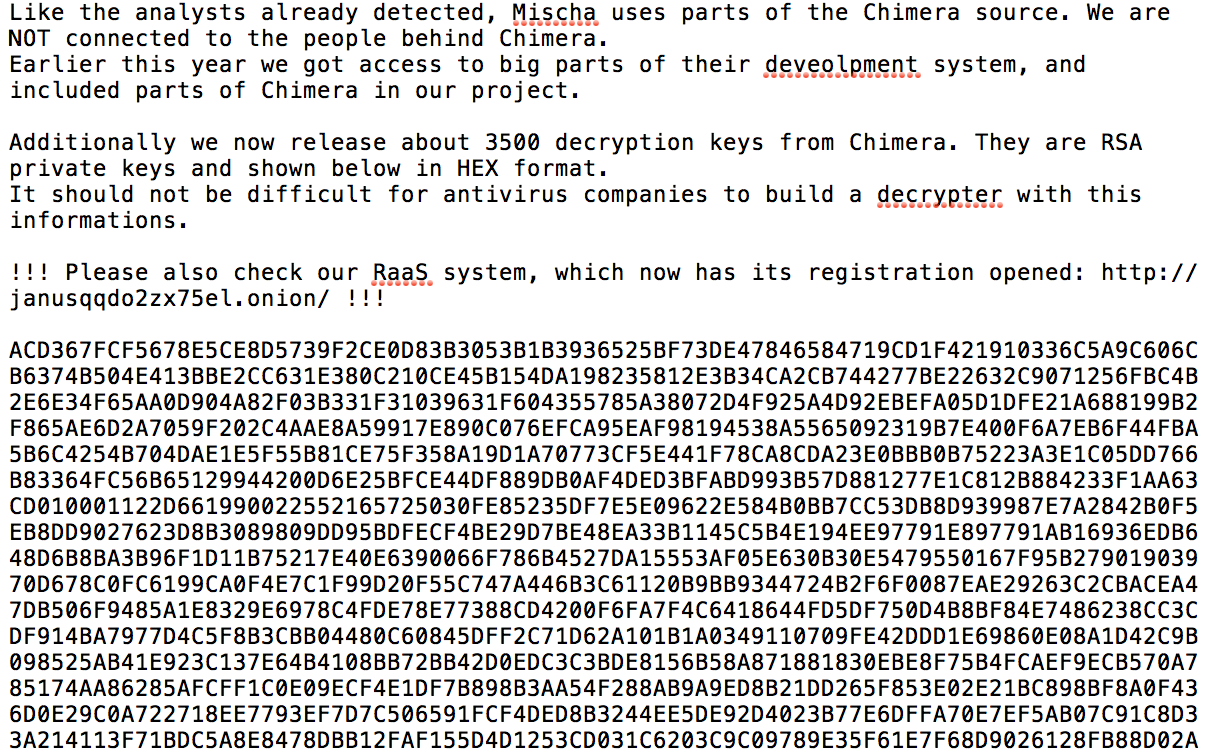 The Petya ransomware gang claims to have leaked 3,500 Chimera keys. (Source: Pastebin)
The Petya ransomware gang claims to have leaked 3,500 Chimera keys. (Source: Pastebin)
Petya's 'GoldenEye' Play
The Petya gang is using the new Chimera crypto key dump to advertise its RaaS - ransomware as a service - offering. Under such programs, developers typically take a cut of all profits generated by subscribers.
It's also notable that Petya claims to have leaked a rival's keys, since the group appeared to have fumbled its own crypto earlier this year. The gang was spreading Petya - a.k.a. Petr - ransomware, in part by spamming German-speaking HR managers with fake resumes for job candidates, according to Fedor Sinitsyn, a malware analyst at security firm Kaspersky Lab.
In April, however, security researchers were able to release a tool that could decrypt files that had been encrypted by Petya, due to a weakness in developers' encryption implementation. Of course, ransomware developers will typically fix their mistakes as quickly as possible to try to maximize their ransom haul.
As expected, the Petya gang quickly returned with an updated version of Petya, as well as another malicious payload, called Mischa. Both of those pieces of ransomware are named after satellites featured in the James Bond movie "GoldenEye."
In recent months, the gang has begun using a malware dropper that attempts to run an executable on a victim's PC, which on systems that have User Account Control enabled will generate a pop-up asking if a user wants to allow a program to make changes to their computer, Malwarebytes analyst "hasherezade" says in a blog post. If the user clicks "yes," then the dropper will have bypassed UAC, obtained administrator-level access rights, and can install the latest version of Petya, which infects the master boot record. If the dropper can't bypass UAC, it attempts to instead install Mischa.
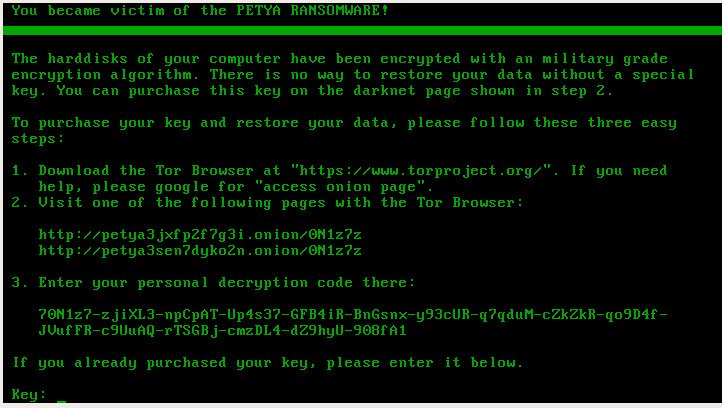 Pictured: Petya ransom demand. (Source: Malwarebytes)
Pictured: Petya ransom demand. (Source: Malwarebytes)
Ransomware Defense: UAC
One moral to the Petya ransomware infection story is that enterprises need to enable UAC to help block infections by any form of malware. "If the user launches the malicious executable file Petya, Windows will show the standard UAC request for privilege escalation," Sinitsyn of Kaspersky Lab says in a blog post. "If the system has been properly configured by the system administrators - i.e. UAC is enabled, and the user is not working from an administrator account - the Trojan won't be able to run any further."
Otherwise, users might give ransomware carte blanche access to crypto-lock their files or even lock down their entire operating system. "Unfortunately, a user who has the privileges to agree to a UAC request often underestimates the potential risks associated with launching unknown software with elevated rights," Sinitsyn says.

