Anti-Malware , Risk Management , Technology
Ransomware Gets Pokémon Go Treatment Crypto-Locking Ransomware Victims: Gotta Catch 'Em All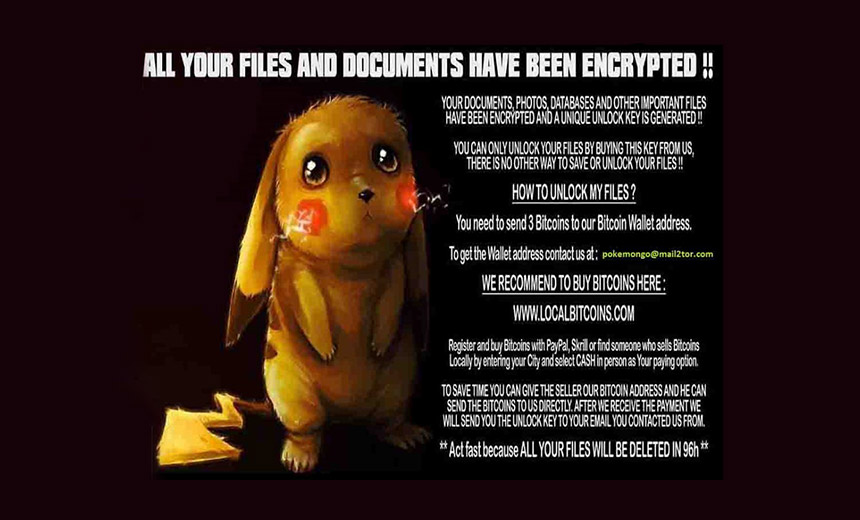 DetoxCrypto PokemonGo variant's ransomware lock screen. Source: MalwareHunterTeam
DetoxCrypto PokemonGo variant's ransomware lock screen. Source: MalwareHunterTeamIn their attempts to compel victims to pay ransoms, cybercriminals have tested crypto-locking ransomware with themes ranging from horror movies to Hitler to cats.
See Also: Managing Identity, Security and Device Compliance in an IT World
Thus it's inevitable that recently spotted ransomware has opted to channel the hot new location-based augmented reality game Pokémon Go (see Pokémon Go Mayhem: Privacy, Muggings, Malware).
Two new versions of Pokémon Go ransomware have been discovered. One is a variant of DetoxCrypto, discovered by the MalwareHunterTeam group. Another variant of DetoxCrypto, meanwhile, looks like generic ransomware - there's no Pokémon theme - and was discovered by Marc Rivero López, a security researcher at Intel Security.
@malwrhunterteam @bleepincomputer @techhelplistcom @jameswt_mht @antelox @demonslay335 @nyxbone ransom note related pic.twitter.com/MV6moXZOve
The Calipso variant sends a screenshot of a user's system to the ransomware controller - potentially for blackmail purposes - and threatens to delete all encrypted files unless a user pays within 72 hours, according to anti-ransomware site Bleeping Computer.
Payload Security, an automated malware analysis service, reports that a related sample of the ransomware obtained by researchers is a 3.7 MB Windows executable file named "88547-pokemongo.exe."
Both ransomware variants' lock screens play music. In the case of the PokemonGo version, it plays an audio file, "pok.wav," containing music from the Pokémon Gameboy game. The ransomware appears to be demanding 2 to 3 bitcoins ($1,160 to $1,700).
@BleepinComputer @demonslay335 @Seifreed @nyxbone @PolarToffee Targeted extensions and excluded folders: pic.twitter.com/lAPLk6DfOI
Hidden Tear: Pokémon Version
A separate piece of ransomware that sports a Pokémon Go theme was discovered by MalwareHunterTeam member Michael Gillespie, as Bleeping Computer first reported.
Independent malware analyst MlwrHpstr says in a blog post on the site of security firm Malwarebytes that the ransomware appears to be based on open source, proof-of-concept ransomware called Hidden Tear, which was published to code-sharing site GitHub by Turkish programmer Utku Sen in August 2015. Sen said his intentions were educational, and ever since then, attackers have been using it to school victims.
The ransomware includes some interesting tricks, including the ability to create an admin-level account named "Hack3r," as well as to locate removable drives and drop an autorun.inf file onto the devices, although this feature does not yet appear to be fully developed, MlwrHpstr says. But the attack technique could be used to spread the ransomware via USB drives or CDs and to have it automatically execute when they were connected to a new system.
"The purpose of dropping the autorun file is so the malware can be executed by the AutoRun and AutoPlay components of Microsoft Windows, which in turn means that the malware can be launched from a USB or CD upon being inserted into a new target system," MlwrHpstr says.
But that is just one of several features that don't appear to have been completed. "The current PokemonGo ransomware is not as sophisticated as Cerber, Petya, Mischa or Locky ransomware but appears to be under development," MlwrHpstr writes. "That being said ... PokemonGo could possibly be used in future social engineering attacks referencing Pokemon Go to entice new victims.
Ransomware Victims: Tough Choices
When it comes to being a ransomware victim, security researchers - working anonymously - recently found that in many cases, they were able to negotiate with attackers to lower their ransom demands (see Ransomware Gangs Take 'Customer Service' Approach). Of course, the prevailing recommendation is for PC users to always run anti-virus software; keep current, offline backups, so that infected systems can be wiped and restored; and if they do get infected, to avail themselves of free decryption tools, when available.
Authorities continue to urge individuals and organizations to never pay ransoms, because the funds directly support criminals' ongoing ransomware research and development.
This story has been updated to reflect that there are two separate and recently discovered types of ransomware with a Pokémon Go theme.

