Anti-Malware , Electronic Healthcare Records , Endpoint Security
$3.6 Million in Bitcoins Demanded from Hollywood Hospital
A string of hospitals around the world - from Hollywood to Germany - have been hit recently by ransomware attacks, in a reminder that no organization is immune to outbreaks of malware that's designed to forcibly encrypt all data stored on PCs and servers (see Ransomware: Are We in Denial?).
See Also: Former NSA Technical Director on Threat Intelligence
One of the most severe cases involves Hollywood Presbyterian Medical Center, based in Los Angeles, which declared an "internal emergency" after staff noticed an apparent ransomware outbreak begin on Feb. 5, reports NBC. The attackers have demanded 9,000 bitcoins, currently worth about $3.6 million, reports Fox News.
The hospital couldn't immediately be reached for comment. But as of Feb. 12, multiple patients had been transferred to other hospitals as a result of the attack, electronic patient records remained inaccessible, and all hospital departments - lacking email access - were attempting to communicate via "jammed fax lines," NBC reports.
In the wake of the attack, the hospital is reportedly working with digital forensic investigators, while the Los Angeles Police Department and FBI are investigating (see FBI Alert: $18 Million in Ransomware Losses).
Hospitals Hit in Germany, Texas
Another recent ransomware victim was Lukas Hospital, based in Neuss, Germany, which reported suffering an infection on Feb. 11, after the malware arrived attached to an email, reports German public news site WDR. The hospital said that it had complete backups, meaning that it could wipe and restore affected systems, and noted that all patient data was already encrypted, which forestalled any potential data loss. But as a precautionary measure, the hospital reportedly took all of its systems offline until they were fully restored, rescheduled 20 percent of its surgeries and shifted less-severe emergency care to neighboring hospitals.
In January, meanwhile, the Titus Regional Medical Center, based in Mount Pleasant, Texas, reported that ransomware had encrypted files on multiple database servers. "We couldn't get to our data," TRMC spokeswoman Shannon Norfleet told local newspaper The Daily Tribune. "When the computers went down and the network administrators accessed the network, there was the ransomware code."
TRMC said it brought in incident-response firm Kroll to conduct a digital forensic investigation and help restore systems following the ransomware infection. "The virus primarily impacted the ability for electronic medical records entry and retrieval, as well as the integration and coordination of interdepartmental orders (laboratory, pharmacy, imaging, etc.)," Norfleet told the newspaper. As a result, TRMC reverted to paper-based systems - and people running records back and forth - as if it was the 1970s, she added.
The medical center couldn't immediately be reached for comment about whether it has resolved the infection.
Well-Known Ransomware Tactics
The recent spate of hospital ransomware infections are notable in part because there have been so few reports to date about such attacks hitting healthcare institutions.
Otherwise, however, the attacks differ little from what's previously been seen in the wild. Indeed, the mechanics of ransomware attacks are well-known, starting with attackers' malware-distribution tactics (see Refined Ransomware Streamlines Extortion). As endpoint security vendor Bromium notes in a recently released report, "all the crypto-ransomware we encountered in 2015 was distributed either by drive-by-download attacks or by macro malware in spam emails."
There now appear to be about 10 different types of ransomware on the market that cybercriminals can purchase, with Cryptowall and TeslaCrypt being most popular, Bromium says. After buying the malware, many attackers handle infecting PCs and harvesting payments. But there are other distribution options as well: TOX and Crypto Locker Service (CLS). TOX is free to use - its developers keep up to 30 percent of ransom earnings - while licensing CLS costs $50, after which developers keep 90 percent of the profits, Bromium reports. Most would-be buyers, however, don't appear to have bought into these alternative approaches. "The share of TOX or CLS in the ransomware attacks observed by Bromium is minimal," it says.
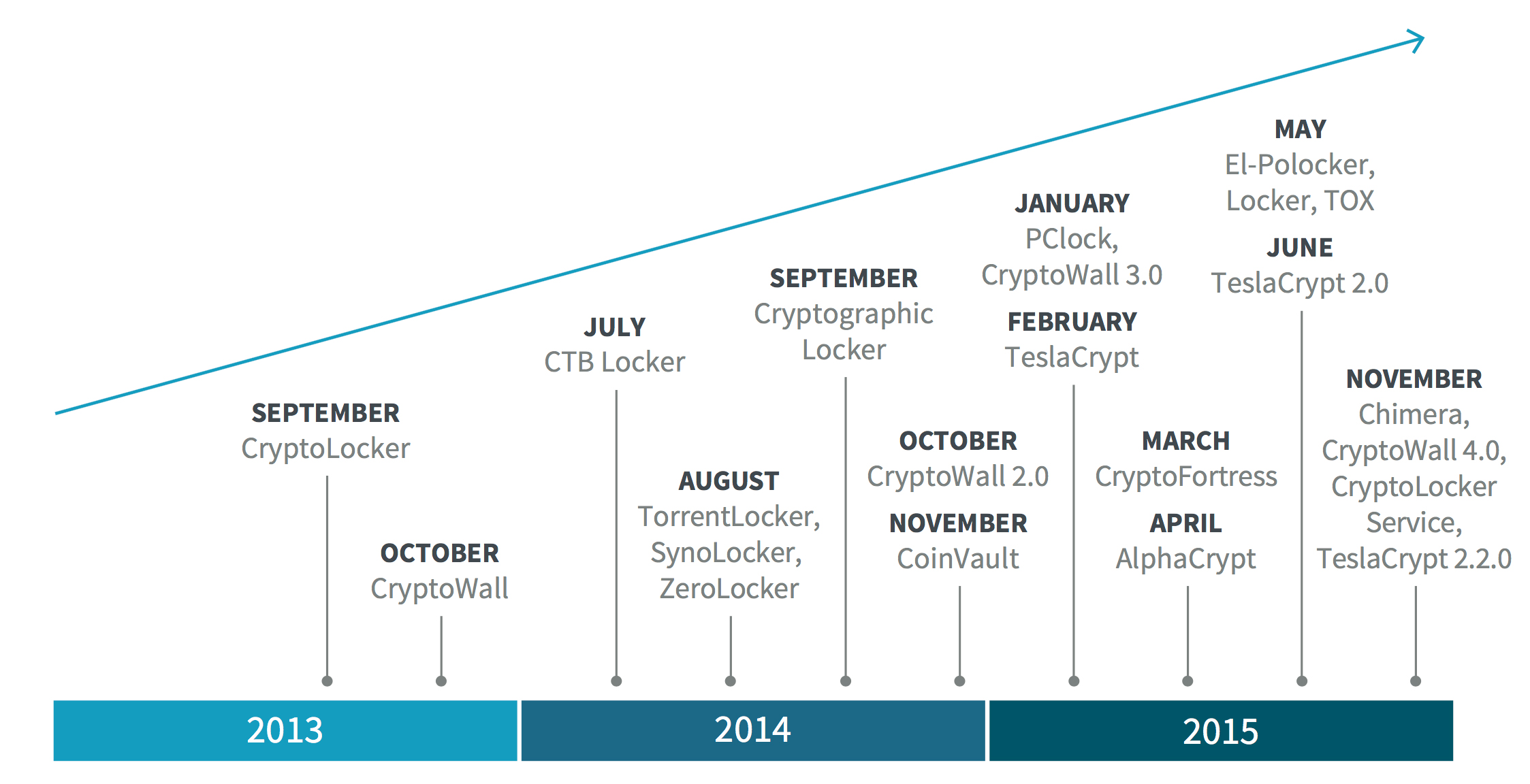 Growth of ransomware families, 2013-2015 (Source: Bromium)
Growth of ransomware families, 2013-2015 (Source: Bromium)
Regardless of the type of malware used, many attackers demand ransom payments in bitcoins - to sites that can only be accessed via the anonymizing Tor network - and use an automated infrastructure that will share decryption keys directly with ransomware victims (see CryptoWall Ransomware Gang Extorts $330,000).
Expert Advice: Prepare, Don't Pay
Police and information security experts recommend that victims never pay, since attackers might not keep up their side of the bargain, and also because it encourages copycat attacks. Instead, experts urge organizations to maintain regular, offline backups, so that they can wipe and restore any ransomware-infected systems in the event of an attack (see Ransomware: 7 Defensive Strategies).
Also continue to educate users about the ransomware threat, and employ Web filtering technology and email-attachment filtering - at the message transfer agent level - recommends information security consultant Claus Cramon Houmann of ImproveIT Consulting, in a blog post.
Falling victim to a ransomware attack can be evidence of poor planning on the part of organizations or their IT service providers. Yet many organizations - especially small and medium-size businesses - as well as government agencies, including police departments, not only continue to fall victim, but to also pay ransoms (see Town Faces Ransomware Infection, Blinks).
No One is Immune
No type of organization is immune to ransomware. For example, attorney Thomas Brown, who heads a law firm in Jacksonville, Fla., said that after his firm's systems had been infected by ransomware for more than a week in December 2015, he gave attackers $2,500 worth of bitcoins and did receive the promised decryption key he needed, the Jacksonville Daily Record reports.
Brown's office manager and legal assistant, Patty Pearson, tells the newspaper that her firm's IT provider told them they could pay the ransom "or lose everything we had." Missing in that analysis, of course, was the option to have better prepared in advance.
That's the choice now facing not just law firms, police departments and government agencies, but also hospitals and every other type of organization that uses PCs or servers.

