Anti-Malware , Data Loss , Encryption
Ransomware Variant Deletes Everything 'Ranscam' Malware Pretends Bitcoin Ransom Will Recover Nuked Files
How low will ransomware go?
See Also: Creating a User-Centric Authentication and Identity Platform for the Healthcare Industry
Security researchers say there's been a flood of new malware variants reaching the market. Cybercriminals are eager to cash in on the profit potential afforded by ransomware - many targets are easy pickings. And the developers who create the malware are eager to turn a profit by selling their attack code to more would-be users.
Greater competition inevitably leads to "innovation," and in this case it almost always comes at the expense of victims' data.
You might think that encrypting a victim's files en masse, deleting the originals and then demanding bitcoins for the decryption key is bad enough. But don't forget cybercriminals targeting not just individuals but also organizations providing critical services, including healthcare facilities and the police. Another wrinkle, of course, is that even the most profit-oriented developer-cum-criminal may fumble their crypto, thus leaving files unrecoverable.
More recently, some ransomware developers have opted for shock value, such as a variant named Jigsaw that takes its inspiration from horror movie "Saw" and begins deleting a user's files while they watch.
What most ransomware victims would find truly evil, however, is malware that simply deleted all of their data, then pretended it was encrypted until victims paid the ransom.
Scam Ransomware Debuts
Enter Ranscam, which represents perhaps the most lazy - and crass - type of ransomware built to date, in that it seeks to cash in on ransomware fears while delivering nothing but scorched-earth tactics, according to Edmund Brumaghin and Warren Mercer of Cisco's Talos Security Intelligence and Research Group.
"It lacks complexity and also tries to use various scare tactics to entice the user to paying," such as informing users that their files have been moved to a "hidden, encrypted partition," and then displaying a ransom message that persists even after reboots, the researchers say in a blog post. The message also says that every time they click the payment link on the ransom note but don't pay, some of their files will get deleted, the post notes.
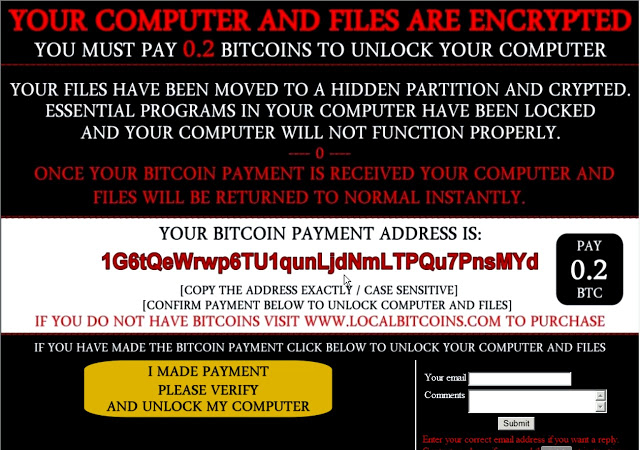 Ranscam promises to decrypt a locked PC in exchange for 0.2 bitcoins (about $135), but the supposedly encrypted files have already been deleted. (Source: Cisco Talos)
Ranscam promises to decrypt a locked PC in exchange for 0.2 bitcoins (about $135), but the supposedly encrypted files have already been deleted. (Source: Cisco Talos)
But that's a lie - the files are already gone, the researchers say, noting that the ransomware doesn't include any encryption or decryption capabilities. Instead, they say, the .NET executable malware is designed to use the Windows Command Processor to run a batch file that deletes the contents of designated folders - largely focused on user-generated content - as well as core Windows files that get used for restoring the system, shadow copies of files and registry keys associated with booting into safe code, among other files.
After that, the malware displays the ransom note, but by then it's too late. "The author is simply relying on 'smoke and mirrors' in an attempt to convince victims that their files can be recovered in hopes that they will choose to pay the ransom," the Talos researchers say. "The lack of any encryption - and decryption - within this malware suggests this adversary is looking to 'make a quick buck' - it is not sophisticated in any way."
It's not clear how widespread Ranscam might be, or how attackers have been sneaking it onto victim's computers. Also, it's not the first virus to outright delete data. But in recent years, such attacks have been relatively rare, aside from a handful of wiper malware attacks that targeted organizations in the Middle East or South Korea, plus the attack launched against Sony Pictures Entertainment in 2014.
7 Enterprise Ransomware Defenses
The takeaway from threats such as Ranscam - or any other malware that can wipe a hard drive - is simple: Preparation is everything (see No-Brainer Ransomware Defenses).
On that front, the U.S. Computer Emergency Response Team, which is part of the Department of Homeland Security, this week updated its recommendations for battling ransomware. In particular, US-CERT recommends:
Backups: Whitelisting applications: Updated operating systems and software: Anti-virus: Least privilege: Killing email-borne macros: Don't click:Simply keeping good backups would take a big bite out of ransomware attackers' profits. "Not only does having a good backup strategy in place help ensure that systems can be restored, it also ensures that attackers are no longer able to collect revenue that they can then reinvest into the future development of their criminal enterprise," the Cisco Talos researchers note (see Please Don't Pay Ransoms, FBI Urges).

