After recent reports that Dropbox and Last.fm suffered historical mega-breaches that have only now come to light, now news of yet another such data breach arrives.
See Also: Hide & Sneak: Defeat Threat Actors Lurking within Your SSL Traffic
Russian web portal Rambler - likened by some to being a Russian version of Yahoo - was reportedly hacked in February 2012, resulting in the theft of data relating to nearly 100 million users.
Moscow-based Rambler offers various online services, including email and search, and also sells online advertising. It's a subsidiary of Prof-Media Management, which is the largest diversified media holding company in Russia. Rambler disputes some aspects of LeakedSource's data breach report.
The allegedly four-year-old breach was flagged Sept. 6, when paid breach-notification service LeakedSource announced that it had obtained stolen information relating to 98.2 million Rambler users, including their email address - containing their username - as well as their password and ICQ chat number (see LeakedSource: 'Assume Every Website Has Been Hacked').
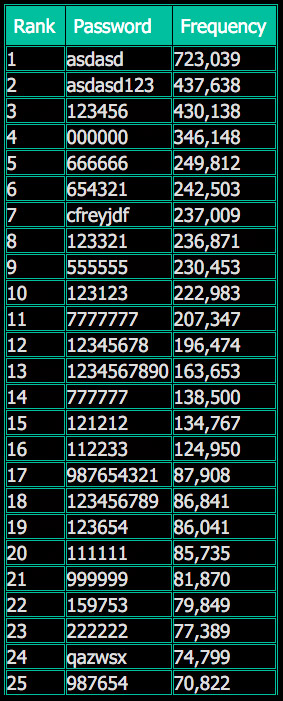 Top top 25 password choices of Rambler users. Source: LeakedSource
Top top 25 password choices of Rambler users. Source: LeakedSourceLeakedSource claims that the website was storing passwords without any encryption or hashing.
If true, that would constitute a very basic security failure, because it meant that anyone - insider or outsider - who was able to gain access to the password repository would have been able to immediately steal and use any user's credentials without having to first try and crack them.
Based on a list of top Rambler passwords published by LeakedSource, the site also appears to not have been requiring users to pick long and strong passwords (see We're So Stupid About Passwords: Ashley Madison Edition).
LeakedSource said that it verified three of the email addresses and passwords contained in the dump with the help of Russian journalist Maria Nefedova, who writes for Russian hacker magazine Xakep.ru. She reportedly reached out to the email address owners, provided the first half of their password, and asked them to supply the final four to six digits.
But Rambler disputes some aspects of LeakedSource's account. "We know about that database. It was leaked March 2014 and contained about 4 million accounts," Rambler spokeswoman Sofya Ivanova tells me. "Right after the accident we forced our users to change their passwords. Some passwords still might be matched because lots of them [are] as simple as 123456."
Ivanova adds: "Nowadays [a] situation like that [would be] impossible. We do not store passwords in plain text, all data is encrypted, we have added a mobile phone verification option and constantly remind our users about the necessity of changing passwords. We also have forbidden [them] to use the previously used passwords for the same account."
Can't Stop the Old Mega-Breaches
The Rambler breach alert follows LeakedSource on Sept. 1 announcing that it obtained user credentials that were stolen from music service Last.fm four years ago. LeakedSource claims that the service was hacked in March 2012 and that information on 43.6 million users - including usernames, email addresses and passwords - was stolen. LeakedSource said it had been able to crack 96 percent of the passwords contained in the dump, which were hashed using MD5.
LeakedSource says it obtained the Rambler data via "This email address is being protected from spambots. You need JavaScript enabled to view it.," noting that this was also the source of the Last.fm breach information.
The Last.fm breach warning followed reports on Aug. 27 that a mid-2012 Dropbox breach was much worse than originally believed (see Dropbox's Big, Bad, Belated Breach Notification).
Other historical mega-breaches that have only come to light this year have involved the likes of dating site Fling, hacked in 2011; has-been social network MySpace, hacked at an unknown time; microblogging site Tumblr, which was hacked in 2013; and LinkedIn, breached in 2012.
LinkedIn knew that it had been breached after 6.5 million LinkedIn users' password hashes appeared on a password-cracking forum in 2012. But the social network didn't force all users to reset their passwords. Fast-forward to May 2016, and it's apparent that LinkedIn failed to exercise proper caution, after a cache of 167 million accounts appeared for sale on a dark web forum.
LeakedSource said it was given copies of the dumped data from Rambler and LinkedIn for free.
This story has been updated to clarify that LeakedSource received the leaked LinkedIn and Rambler data for free.

