Anti-Malware , Fraud , Phishing
Attackers Increasingly Favor Ransomware Over Banking Trojans, FireEye Says
Cybercriminals wielding Locky crypto-locking ransomware are continuing to ramp up their assaults, especially in the healthcare sector, with attackers distributing less banking malware and more ransomware, according to new research.
See Also: API vs. Proxy: Understanding How to Get the Best Protection from Your CASB
So far this month, several "massive" new phishing campaigns have been launched, targeting victims in multiple industries with Locky ransomware, security researcher Chong Rong Hwa from cybersecurity firm FireEye says in a blog post (see Report: Most Phishing Emails Pack Ransomware).
As in recent months, healthcare remains the sector most frequently targeted by Locky ransomware. So far in August, other oft-targeted industries include telecommunications, manufacturing, aerospace/defense, financial services and government agencies, according to FireEye. Organizations in the United States were most targeted, followed by Japan, South Korea, Thailand, Singapore and Germany.
Attackers often focus on healthcare organizations and other firms that have "time-sensitive records," according to Mark Rasch, security evangelist at Verizon Enterprise Solutions. That's because even if those organizations are well-prepared to detect, block or recover from a ransomware infection, they may not have the time to do so, and thus may have greater incentives to pay a ransom in exchange for decryption keys (see Ransomware: Is It Ever OK to Pay?).
The Rise of Locky
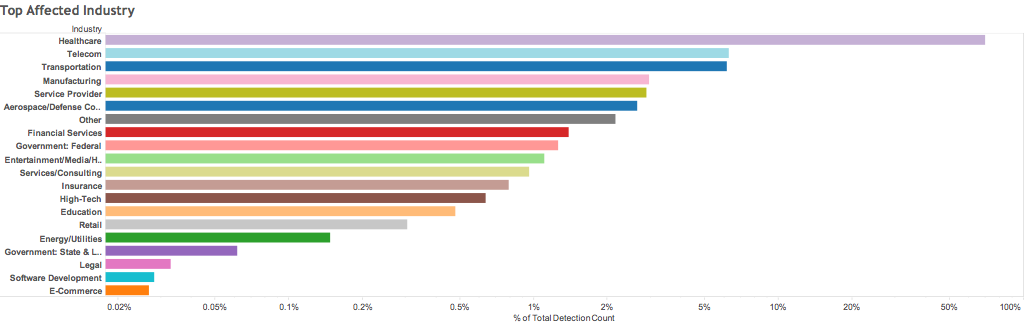 Industries most targeted by Locky ransomware in August 2016. Source: FireEye
Industries most targeted by Locky ransomware in August 2016. Source: FireEye
Locky, which first appeared early this year, has become one of the most prevalent types of ransomware. Its name derives from it adding a .locky extension to encrypted files. Once the ransomware encrypts data on a PC, it typically demands a ransom of between 0.5 and 1 bitcoins ($288 to $577), according to Paul Ducklin, a senior security adviser at security firm Sophos. He says spam emails with Locky attachments often urge recipients to enable macros, so the ransomware can run. "Don't do it," he stresses.
It's not clear who created Locky, although some security experts suspect it's the work of whoever created the Dridex banking Trojan and that the culprits are most likely Russian. Security firm Symantec says that Locky and Dridex have in some cases been distributed by the same spam affiliate group.
JavaScript Out, DCOM Files In
In August, FireEye's Chong says, many Locky-wielding attackers appear to have shifted away from using a JavaScript-based downloader contained in a compressed ZIP file to infect endpoints with Locky. Instead, they're using XML-based .docm files attached to phishing emails. Microsoft Word .docm files are like .docx Word files, except they can also be used to execute macros.
Many cybercrime groups employ automated cybercrime exploit kits to distribute not just banking malware but also ransomware, as was seen in a recent campaign that used the Necurs exploit kit to distribute Dridex banking malware as well as Locky (see Cisco Eyes Ties Between Angler and Lurk Malware).
But at least recently, attackers are distributing less banking malware and more ransomware, Chong says. "We have observed that the delivery of Dridex via this distribution channel seems to have stopped, or nearly so, which could explain why we are seeing the Locky uptick."
Other security firms confirm that in recent weeks, Locky attacks have surged. "These attacks were among the largest campaigns we have ever observed, peaking at hundreds of millions of messages a day," according to a report released last month by the cybersecurity firm Proofpoint. Between April and June, it adds, 69 percent of all malicious email attachments seen in the wild were some form of Locky.
Brazilian Locky Taps Windows Script Files
Whoever is distributing - or helping to distribute - Locky recently began using Windows Script Files to download the ransomware onto victims' PCs, researchers at security firm Trend Micro say in a blog post. The new variant, first seen in the wild on July 15, is being sold on underground Brazilian cybercrime sites, the researchers say.
"WSF is a file that allows the combination of multiple scripting languages within a single file," they say, noting that the WSF files arrive via inside .zip files attached to spam emails that sport email subject lines such as "annual report," "bank account record" and "company database."
The gang behind Cerber ransomware also has used WSF files since May, the Trend Micro researchers say (see Cerber 2 Ransomware: Free Decryption Tool Released). "It would seem that the attackers behind Locky followed Cerber in using WSF files after seeing how such a tactic was successful in bypassing security measures like sandbox and blacklisting technologies ... since it has no static file type," the researchers say. "In addition, using blended scripting languages could result to the samples being encoded, making these arduous to analyze."
Opening Unknown Attachments: Think Twice
Locky is designed to encrypt not just the hard drive of the PC it infects, but also any attached drives and network shares, potentially including any other PC or server that it can access via a local area network. Like many other types of ransomware, Locky also deletes Volume Snapshot Service files, a.k.a. shadow copies, that could otherwise be used to help restore forcibly encrypted files.
Locky often spreads via email attachments. "These latest campaigns are a reminder that users must be cautious when it comes to opening attachments in emails or they run the risk of becoming infected and possibly disrupting business operations," Chong says.
Ducklin at Sophos says one related defense is to download Microsoft Office viewers - applications that "let you see what documents look like without opening them in Word or Excel itself." The viewers do not support macros, thus automatically preventing macro-based malware from executing.
To help block Locky attacks, Trend Micro also recommends stripping all WSF files from incoming emails.

