Anti-Fraud , Anti-Malware , Fraud
$25 Million in Losses Tied to 'Lurk' Malware-Using Cybercriminals Russia's Federal Security Service (FSB)
Russia's Federal Security Service (FSB)Russian authorities have arrested about 50 people in connection with an ongoing investigation into a hacker group that's suspected of unleashing malware-enabled hack attacks against customers of major Russian financial institutions.
See Also: 2016 Enterprise Security Study - the Results
The gang allegedly stole 1.7 billion rubles ($25.5 million) from accounts at multiple Russian financial services firms over a five-year period, Russia's federal security service, known as the FSB, says in a June 1 statement. It adds that Sberbank - the largest bank in Russia and Eastern Europe - assisted with its investigation, but didn't name any of the other victim banks.
The gang had attempted to steal a further 2.3 billion rubles ($34 million) by issuing false payment instructions, which were blocked, Russia's Interior Ministry tells Reuters.
The FSB, which is the successor to the Soviet KGB, says it made related arrests - supported by Interior Ministry and National Guard troops - in 15 regions across Russia.
"As a result of [house] searches a large quantity of computer equipment was confiscated along with communications gear, bank cards in false names and also financial documents and significant amounts of cash confirming the illegal nature of their activity," the FSB says.
All of the suspects have been charged with activities related to developing, distributing and using malware. After the raids, 18 primary suspects were denied bail, while three were placed under house arrest, according to the FSB.
Security experts say the malware used by attackers, called Lurk, was previously used primarily for click fraud, which refers to the practice of generating fake clicks on advertisements to illegally generate profits for website operators. But Moscow-based security firm Kaspersky Lab, which shared related intelligence with Russian banks and law enforcement agencies, says that 18 months ago, Lurk began to be deployed to assist in attacks against Russian banks, with attackers attempting to disguise their identity by using compromised VPN services.
"We realized early on that Lurk was a group of Russian hackers," says Ruslan Stoyanov, head of computer incidents investigation at Kaspersky Lab, in a statement. "Our company's experts analyzed the malicious software and identified the hacker's network of computers and servers. Armed with that knowledge, the Russian police could identify suspects and gather evidence of the crimes that had been committed."
Hackers Pummel Russian Banks
An unnamed source with knowledge of the investigation tells Russian news agency TASS that in March and April alone, six Russian banks - including Metallinvestbank, Metropol, Regnum and Russian International Bank - fell victim to related cyber attacks, and that Metallinvestbank alone lost 680 million rubles ($10.2 million).
As this week's arrests demonstrate, Russian authorities do target Russian residents who attack domestic targets (see Russian Cybercrime Rule No. 1: Don't Hack Russians). But in the past, gaining convictions has been difficult because under Russian law, investigators must prove that any cybercrime was accompanied by monetary theft from Russian organizations or individuals, according to Sergey Nikitin, deputy head of the computer forensics laboratory and malicious code analysis team at Moscow-based cybersecurity firm Group-IB (see Russia: 7-Year Sentence for Blackhole Mastermind).
The Malware
The Lurk malware used in the alleged cybercrime spree is primarily designed to infect systems and then download further malware, in part by using digital steganography, which refers in this case to hiding malware inside image files, according to Dell SecureWorks.
But that isn't the only type of malware being used to target Russian banks. This week, security firm Zscaler published a report on Android malware that's disguised as the official Sherbank mobile banking app. A Kaspersky Lab spokeswoman tells Information Security Media Group that the app isn't connected to the Lurk gang.
Regardless, the app demonstrates one way that hackers have been tricking banking customers into revealing their access credentials, thus allowing attackers to drain their accounts.
Zscaler doesn't detail how the Trojan app has been distributed, and notes that the Sherbank app currently available from Google Play is legitimate. But if a user installs the Trojan version on their device, the malware requests administrator privileges which "can cause devastating effects to the victim's device" if allowed, Shivang Desai, a security researcher at Zscaler, says in a blog post. Those abilities include intercepting SMS messages - which could be used to grab the one-time codes banks send to authorize transactions, especially for attacker-initiated money transfers - as well as the ability to call any number, which attackers could use to generate illegal profits by calling expensive toll numbers that they also control.
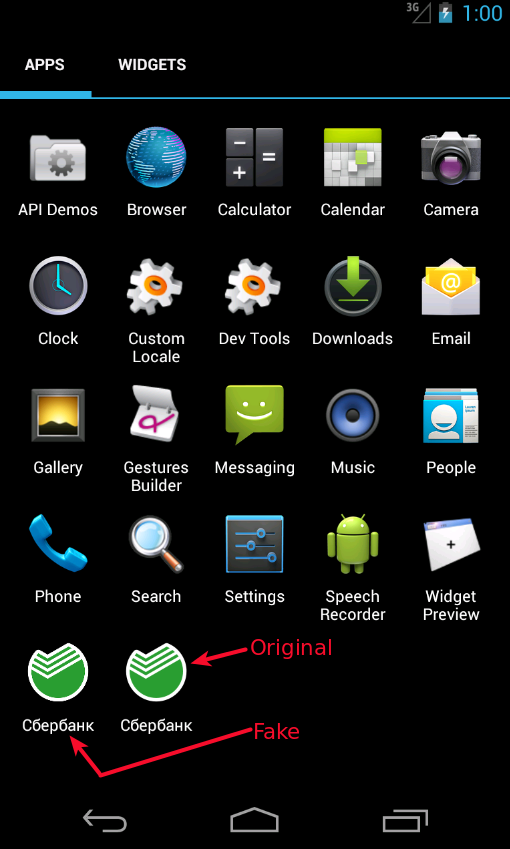 Attackers disguised their malware to look like Sberbank's Android app. (Source: zScaler)
Attackers disguised their malware to look like Sberbank's Android app. (Source: zScaler)Desai says the malware is also designed to present a fake log-in screen and steal credentials whenever users start up the Whatsapp app, Google Play Store, or the VTB 24 app, which provides access to accounts at Russian banking giant VTB. After the malicious app gets installed, it also suppresses all access to the legitimate apps.
"Even if the victim tries to access the original app, the malware will forcefully present its own fake login screen to the victim," he says, and after anyone provides their log-in credentials, they get sent to the attackers' command-and-control server.
Deleting the app can be difficult, short of wiping a device and reinstalling core software. "The malware has a very clever approach to remain persistent," Desai says. "It registers a broadcast receiver that triggers whenever the victim tries to remove administrator rights of the malware app, locking the Android device for a few seconds. As a result, it is not possible to uninstall this malicious app by revoking admin rights."

