Anti-Malware , Forensics , Technology
Attackers Can Hack Non-Jailbroken iOS Devices, Security Experts Warn
A complex - but practical - attack is being used to install malware on non-jailbroken Apple iOS devices, security experts warn.
See Also: Secure, Agile Mobile Banking: Keeping Pace with Last Best User Experience
Palo Alto Networks discovered the attack in the wild. It's being enabled by a Windows application called Aisi Helper, which tricks iOS devices into installing malware called AceDeceiver. Aisi Helper subverts a digital rights management feature called FairPlay that's built into iOS devices, while the malware itself is designed to upload infected devices' Apple ID and passwords to a command-and-control server.
Security researchers at Palo Alto Networks say Aisi Helper is marketed as a tool for installing pirated apps, and to date works only in China. But the technique used by Aisi Helper to bypass Apple's app review process and "walled garden" security model could be used by any malicious application running on a desktop to potentially install iOS apps "without the user's knowledge," Palo Alto researcher Claud Xiao contends in a blog post.
More Such Attacks to Come?
"If you are responsible for security in your organization, I suggest you familiarize yourself with this new form of Trojan as it is only a matter of time before further malware makes use of the same attack vector," Alan Woodward, a University of Surrey computer science professor, says in a blog.
Previously, attackers who wanted to exploit a non-jailbroken iOS device had to rely on digital certificates issued by an enterprise, which are used, for example, to allow mobile device management software to manage approved iOS devices that are allowed to connect to an enterprise's corporate network.
"What makes AceDeceiver different from previous iOS malware is that instead of abusing enterprise certificates - as some iOS malware has over the past two years - AceDeceiver manages to install itself without any enterprise certificate at all," Xiao says. "It does so by exploiting design flaws in Apple's DRM mechanism, and even [though] Apple has removed [apps containing] AceDeceiver from the App Store, it may still spread thanks to a novel attack vector."
The FairPlay Man-In-The-Middle Attack
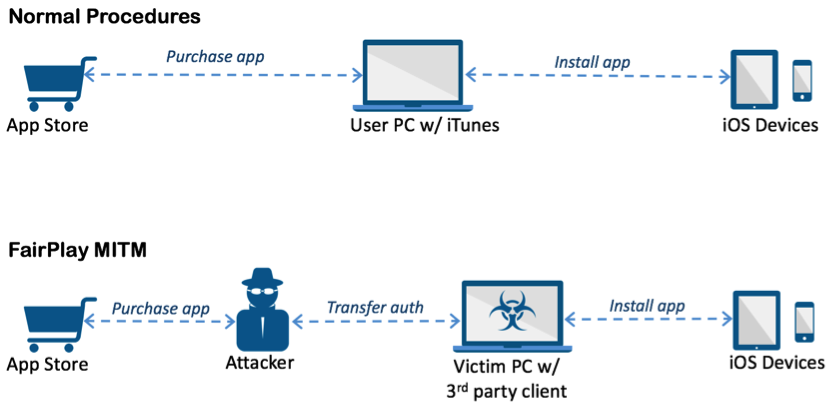 Source: Palo Alto Networks
Source: Palo Alto Networks
This attack vector centers on Apple's FairPlay DRM protection mechanism, which can be abused to trick any iOS into installing software, even if it hasn't been purchased from the App Store or signed using an enterprise digital certificate.
The FairPlay flaw isn't new. Indeed, man-in-the-middle attacks that targeted FairPlay - to spread pirated apps - were first seen in the wild in January 2013.
In August 2014, a team of Georgia Institute of Technology researchers described how the attacks worked and warned that the Apple DRM flaws could potentially be used to launch large-scale attacks against iOS devices. But so far, no such attacks apparently have occurred.
AceDeceiver Appeared in July 2015
The first AceDeceiver-infected app appeared on the Apple App Store in July 2015, Xiao says, although he declined to name the app. Subsequently, the AceDeceiver-infected "AS Wallpaper"- an app that gives users additional options for changing the background on their device - appeared on Apple's U.S. App Store in November 2015. A third infected app, called "i4picture," debuted on Apple's U.S. and U.K. App Stores on January 30, he adds.
Palo Alto says it discovered the malicious apps and warned Apple on February 24. It says Apple removed them from the App Store the next day.
Apple says it uses a code-review process, which it has never described in full, to look for signs of malicious code before it approves any app and allows it to be distributed via its official App Store. But whoever designed AceDeceiver and snuck three related apps onto the App Store obviously bypassed these checks.
"AceDeceiver's software got through Apple's review process by lying dormant inside what looked like a legitimate app," says digital forensic scientist Jonathan Ździarski, author of "iPhone Forensics," in a blog post. "It called home to a C2 [command-and-control] server to see if it should activate itself. After the app review process completed, it was signed by Apple, and could be turned on to do damage. At this point, it didn't matter that Apple removed it from the store - it was signed by Apple, and Apple can't revoke their own certificate."
Fortunately, at least for now, the risk from AceDeceiver is low, says threat-intelligence firm iSight Partners, because current versions of Aisi Helper are designed to only deploy the malware on iOS devices located inside mainland China. In the future, any "targeted individuals [would have to] have a Windows PC with the Apple App Store installed - which the malicious actor must compromise first - before infecting any attached iOS devices," it says. Even so, however, "due to the value of iOS security-defeating methods, we can expect the FairPlay Man-in-the-Middle technique to be reused in other malicious campaigns that may target victims outside China."
Apple declined to comment on these developments.

