Cybersecurity , Network & Perimeter , Technology
While NSA Hacks, US-CERT Frets "Sophisticated Hackers and Advanced Threat Actors" Target Networking Gear Photo: Jon 'ShakataGaNai' Davis (Creative Commons)
Photo: Jon 'ShakataGaNai' Davis (Creative Commons)In the wake of the leak of firewall attack tools from the Equation Group, by a group calling itself the Shadow Brokers, the U.S. Computer Emergency Readiness Team has issued a warning to all organizations, telling them that they must do more to lock down their networking equipment.
See Also: From Authentication to Advanced Attack Vectors: Top Trends in Cybercrime in Q1 2016
"For several years now, vulnerable network devices have been the attack-vector of choice and one of the most effective techniques for sophisticated hackers and advanced threat actors," it reads.
But many security experts have tied the Equation Group exploits to the National Security Agency's in-house hacking squad.
Security expert Bruce Schneier, CTO of IBM's Resilient, says in a blog post that the leaked attack tools show that "the agency is hoarding information about security vulnerabilities in the products you use, because it wants to use it to hack others' computers." He adds that "those vulnerabilities aren't being reported, and aren't getting fixed, making your computers and networks unsafe."
In other words, the "sophisticated attacker" alert from US-CERT, which is part of the Department of Homeland Security, was triggered by attack capabilities that apparently trace to the same government's signals intelligence agency, some of which include custom-built exploits for networking equipment developed and sold by U.S. manufacturers.
Does this feel like a family affair, or what?
We'll Always Have Puns
The Shadow Brokers dump includes Equation Group attacks sporting names such as PIXPOCKET, which exploits vulnerabilities in Cisco PIX devices, and which Cisco stopped supporting a few years ago. Other attacks include EGREGIOUSBLUNDER, targeting Fortinet devices; ESCALATEPLOWMAN, targeting WatchGuard devices; and ELIGIBLEBOMBSHELL, targeting Topsec devices.
Meanwhile, an attack called EXTRABACON can be used to hack into any Cisco ASA device unless it's been recently patched using Cisco's related updates.
Exploits Leaked by Shadow Brokers
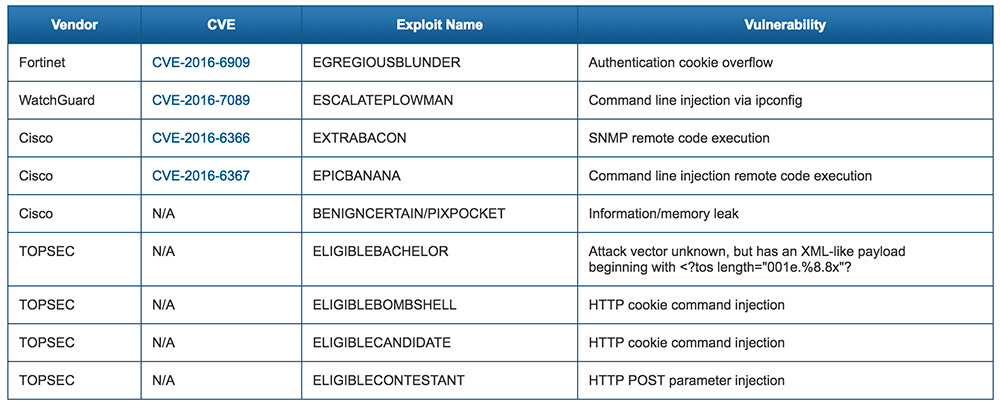 Source: US-CERT6 Network Admin Essentials
Source: US-CERT6 Network Admin Essentials
Whatever the identity of the Equation Group, security experts have long told me that any nation-state that can muster a hacking team will do so. China, France, Israel, Russia and the United Kingdom often feature on hacking experts' lists of "the best of the best."
Thus US-CERT's recommendations, while released in the shadow of the Equation Group tool dump, count as a "must do" for any organization that manages its own networking equipment.
Here's a brief overview:
Segregate networks and functions: Network segregation can "contain malicious occurrences" and block attackers from gaining access to other parts of the network. Limit unnecessary lateral communications: Restricting and filtering communications, including using vLANs with access control lists, helps battle backdoors. Harden network devices: Use secure configurations, restrict physical access to devices, employ strong passwords and encryption, disable all unnecessary services and never allow unencrypted remote access to admin protocols, for starters. Secure access to infrastructure devices: Use multifactor authentication, maintain privileged access controls and keep admin credentials locked down. Perform out-of-band management: Separate user traffic from network management traffic, locking down all admin-level access to devices. Validate integrity of hardware and software: Know your supply chain, validate all equipment and firmware and keep a close eye on network configurations for unauthorized changes.Still Falling For SYNful Knock
What US-CERT is recommending, however, is what organizations should already have been doing. But it's clear that many haven't been paying sufficient attention to the security of their networking equipment.
In the same alert, for example, US-CERT calls out an attack known as SYNful Knock - so named by U.S. cybersecurity firm FireEye - that came to light in September 2015, which can be used to change a router's operating system to give attackers persistent access to the device. "The initial infection vector does not leverage a zero-day vulnerability," US-CERT says. "Attackers either use the default credentials to log into the device or obtain weak credentials from other insecure devices or communications."
Who needs potentially sophisticated, NSA-built exploits to hack, if network administrators have rolled out equipment with default passwords or otherwise failed to secure other parts of the network?

