Anti-Malware , Risk Management , Technology
Why It's Time to Remove QuickTime for Windows Apple Won't Patch, So Delete Software, US-CERT Advises
Apple's QuickTime media player and web browser plug-in should be immediately expunged from all Windows systems, security experts warn, in a reminder of the dangers of using outdated software - especially web browser plug-ins.
See Also: How to Mitigate Credential Theft by Securing Active Directory
Security vendor Trend Micro recently issued an "urgent security alert," warning that "everyone should follow Apple's guidance and uninstall QuickTime for Windows as soon as possible." The alert comes after the security firm found two zero-day flaws in QuickTime for Windows, which it says Apple won't patch.
Apple didn't immediately respond to a request for comment on that warning, or whether it plans to alert users directly.
The two flaws - designated ZDI-16-241 and ZDI-16-242 - could be abused by attackers to remotely execute code on vulnerable systems. Both were reported to Trend Micro's Zero Day Initiative by Steven Seeley at security firm Source Incite, based in Mexico City. Trend Micro alerted Apple on Nov. 11, 2015. So far, Trend Micro says, it hasn't seen any related attacks in the wild.
The alert follows security vendor Flexera Software warning that for the whole of 2015 - meaning before these two new flaws came to light - the riskiest application installed on U.S.-based Windows PCs was QuickTime. That's because the software has a high installation base, and more than half of all users are running an unpatched version that contains exploitable vulnerabilities.
The World's Riskiest Software
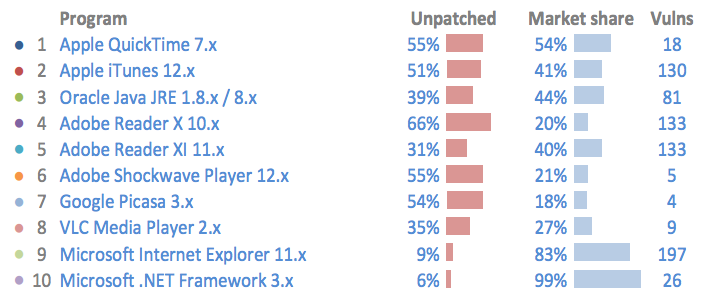 Software ranked by the severity and quantity of new vulnerabilities (vulns) discovered as well as the software's prevalence (market share), all in 2015. (Source: Flexera Software.)
Software ranked by the severity and quantity of new vulnerabilities (vulns) discovered as well as the software's prevalence (market share), all in 2015. (Source: Flexera Software.)Yet Apple's guidance still isn't to uninstall QuickTime. Instead it's more circumspect, offering removal instructions "if you no longer need QuickTime 7."
But the U.S. Computer Emergency Response Team doesn't mince words, warning that because Apple has ceased supporting QuickTime for Windows, the software is "vulnerable to exploitation," and that the only way to protect against that is to remove the software now. "Computer systems running unsupported software are exposed to elevated cybersecurity dangers, such as increased risks of malicious attacks or electronic data loss," US-CERT says. "Exploitation of QuickTime for Windows vulnerabilities could allow remote attackers to take control of affected systems."
That warning is a reminder that all nonessential software should be expunged from systems whenever possible. That's especially true for any web browser plug-ins, including outdated versions of Adobe Flash, Microsoft Silverlight and Oracle Java, which attackers often favor for compromising PCs and installing malware (see Cybercriminals Mourn Java Plug-In Death).
Too often, "outdated" seems to refer to any version of the plug-in software before it was updated yesterday. But that's the tradeoff users must make when using browser plug-ins. Indeed, security firm Kaspersky Lab says that in 2015, 62 percent of all online attacks targeted browsers, including plug-in flaws.
Removing Plug-In
One major security impetus for uninstalling QuickTime on Windows is that it will also remove the QuickTime browser plug-in, which is a potential attack target. "Uninstalling QuickTime 7 also removes the legacy QuickTime 7 web plug-in, if present," Apple says. "Websites increasingly use the HTML5 web standard for a better video-playback experience across a wide range of browsers and devices, without additional software or plug-ins."
Despite the US-CERT alert, however, Apple is still offering the latest QuickTime for Windows - version 7.7.9 - as a download. The download page, which was last updated March 9, carries no security-related warnings or deprecation alert.
Regardless, vulnerability remediation expert Wolfgang Kandek, CTO at the security firm Qualys, advocates removing all software as soon as it loses support. But if that's not possible, then he recommends trying to reduce or eliminate network access for devices that continue to run the outdated software, in particular by blocking the ability to browse websites or check email. He also recommends installing Microsoft's Enhanced Mitigation Experience Toolkit, which is designed to prevent software vulnerabilities in Windows from being exploited (see 5 Secrets to Security Success).
What Windows XP Use Tells Us
Unfortunately, too many users fail to heed the "if it's outdated, delete it" advice.
According to market researcher Net Applications, for example, Windows XP still accounts for 11 percent of all operating systems in use, despite Microsoft dropping related support two years ago. Similarly, Flexera Sofware reported that at the end of 2015, the outdated - and frequently targeted - Adobe Flash Player version 19 continued to be present on 73 percent of all U.S. systems (see 2016 Resolution: Ditch Flash).

