Breach Notification , Breach Preparedness , Breach Response
2013 Breach Appears Separate from Another Breach Involving 500 Million Users Yahoo's corporate headquarters in Sunnyvale, Calif.
Yahoo's corporate headquarters in Sunnyvale, Calif.Yahoo has the dubious distinction of having not just one but two record-shattering historical data breaches come to light in the same year.
See Also: 2016 IAM Research: Where Financial Institutions' PAM Programs Are Falling Short
Yahoo on Dec. 14 warned that it's found a breach that appears to date from 2013, which put the data of 1 billion users at risk.
"We believe an unauthorized third party, in August 2013, stole data associated with more than one billion user accounts," Yahoo CISO Bob Lord says in a security alert to customers. "We have not been able to identify the intrusion associated with this theft."
Information that was potentially stolen includes names, email addresses, telephone numbers, dates of birth, passwords hashed using the outdated MD5 algorithm as well as encrypted or unencrypted security questions and answers. Yahoo says no payment card data or banking information was stored in the affected system, and thus it does not believe any such data was compromised.
Yahoo is notifying all potentially affected customers and says that it's invalidated all security questions.
The search giant believes the breach is separate from the incident that it confirmed on Sept. 22, which involved the theft of more than 500 million accounts in late 2014 (see Massive Yahoo Data Breach Shatters Records). In a recent Securities and Exchange Commission filing, Yahoo said that it detected that an attacker was inside its network in 2014, but failed to spot the data exfiltration.
The White House says the FBI is now investigating both Yahoo breaches.
In September, Lord said Yahoo believed that 2014 attack was perpetrated by "a state-sponsored actor." But security firm InfoArmor has suggested that a cybercrime gang without nation-state ties might have been behind the attack (see: Yahoo Breach Conspiracy Theories: Don't Believe the Hype).
In the latest breach alert, Yahoo says that it first learned of the 2013 intrusion from U.S. law enforcement, which shared information that an unnamed third party claimed involved Yahoo data.
"We analyzed this data with the assistance of outside forensic experts and found that it appears to be Yahoo user data," Lord says.
Yahoo declined to specify which law enforcement agency shared the set of stolen data. "We're not sharing detail with regards to methods and sources associated with our investigation," a spokesman tells ISMG. "We continue to work closely with law enforcement."
Cookie-Forging Attacks
Yahoo says that it's continued to investigate attacks involving forged cookies, referring to small pieces of code placed by websites on a user's device to track users and often also free them from having to log into a site every time they return.
But attackers appear to have reverse-engineered Yahoo's cookies, enabling them "to access users' accounts without a password," Lord says. "The outside forensic experts have identified user accounts for which they believe forged cookies were taken or used. We are notifying the affected account holders and have invalidated the forged cookies. We have connected some of this activity to the same state-sponsored actor believed to be responsible for the data theft the company disclosed on Sept. 22, 2016."
Yahoo declined to comment on the number of accounts that may have been compromised by attackers wielding compromised cookies.
In September, shortly after Yahoo announced the 2014 breach, InfoArmor claimed in a blog post that it likely knew of a specific group that was behind the hack.
InfoArmor said at the time that it had obtained a sample of the stolen Yahoo data from its sources, according to a blog post. In a Dec. 14 email to ISMG, InfoArmor's chief intelligence officer Andrew Komarov says that Yahoo's description of the type of data leaked in 2013 matches its sample.
The limited set of InfoArmor data that was provided to Yahoo - via Bloomberg - could overlap with the information shared with Yahoo by the law enforcement agency, a source familiar with Yahoo's investigation tells ISMG.
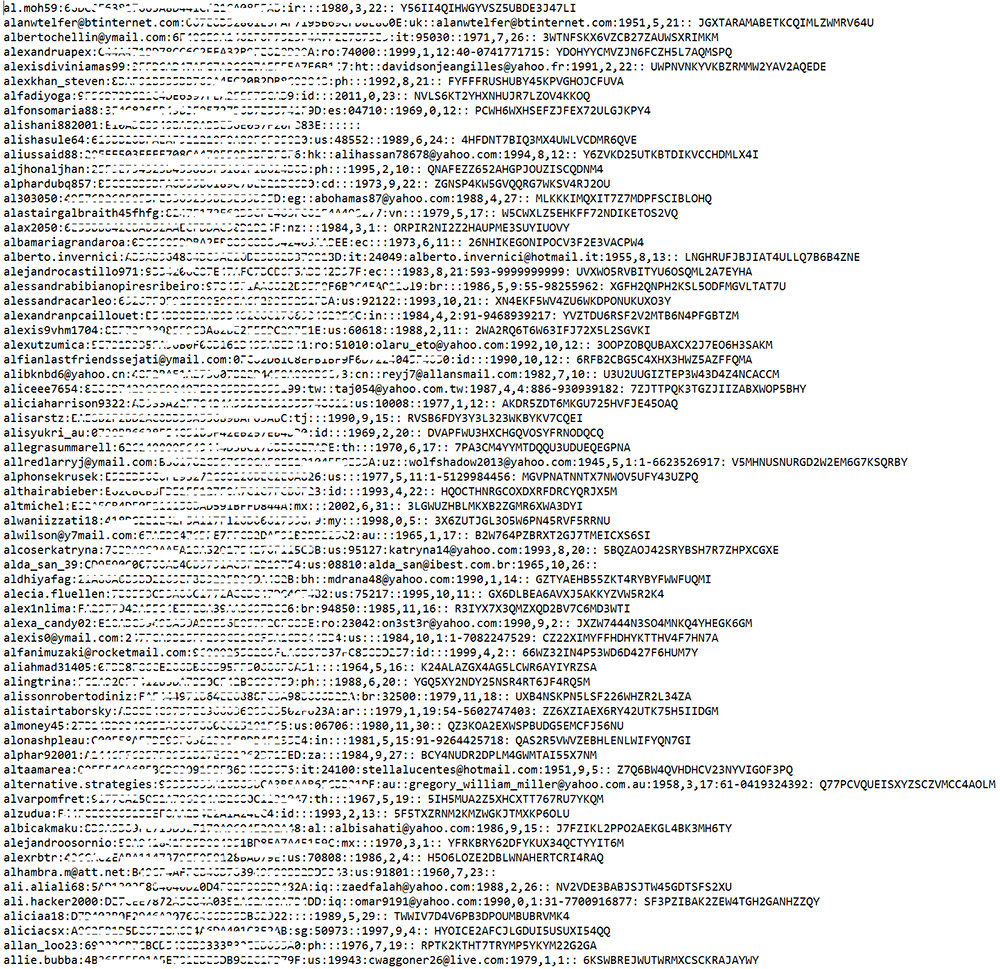 A sample of the stolen Yahoo data obtained by InfoArmor.
A sample of the stolen Yahoo data obtained by InfoArmor.In its blog post, InfoArmor said it believed that the attackers who stole the information that it later obtained were "a group of professional blackhats from Eastern Europe," which InfoArmor calls Group E.
Group E had a relationship with someone who offered batches of stolen data on underground markets from companies including LinkedIn, InfoArmor claims. The person went by the nickname "Tessa88." Tessa88 was also connected with another persona who sold underground data, "peace_of_mind" or Peace.
Both Tessa88 and Peace had advertised batches of stolen data, including the LinkedIn and MySpace breaches. But other leaks the two advertised turned out to be mislabeled and actually aggregations of data from other breaches.
Wrinkle for Yahoo
The latest breach admission comes at a tricky time for Yahoo, which has been seeing a decline in revenue. Plus, CEO Marissa Mayer has faced criticism that the company failed to devote sufficient resources to bolstering its information security program.
"What's most troubling is that this occurred so long ago, in August 2013, and no one saw any indication of a breach occurring until law enforcement came forward," Jay Kaplan, CEO of security firm Synack, tells The Wall Street Journal. "Yahoo has a long way to go to catch up to these threats."
The breach also highlights the ongoing challenges that breached organizations face when it comes to discovering that they've been breached. "This billion-person data theft illustrates two critical points: first, there is currently no single technology or blend of technology controls that currently exists to either keep a persistent and well-trained adversary from breaking into any company, and second, that technology that moves at machine speed to let a company know data is flowing out the back door is not mature enough to provide real-time alerting," Christopher Pierson, CSO of B2B payment provider Viewpost, tells ISMG.
Will Breach Impact Verizon Deal?
In late July, Verizon agreed to buy Yahoo's operating businesses for $4.8 billion. Many market watchers say the deal comes at a critical time for Yahoo, which has been seeing declining revenues. By acquiring Yahoo, furthermore, Verizon could combine it with AOL, which it acquired in 2014 for $4.4 billion, thus battling Google and Facebook for a bigger share of the world's online advertising revenue.
Following the first breach revelation, in response to questions about whether Verizon might seek to alter the terms of the deal or walk away, it said in October that it was waiting to see the full results of Yahoo's investigation (see Verizon's Yahoo Breach Question: What's 'Material'?).
On Dec. 14, Verizon now said it's awaiting the full results of both breach investigations. "As we've said all along, we will evaluate the situation as Yahoo continues its investigation," says Verizon spokesman Bob Varettoni. "We will review the impact of this new development before reaching any final conclusions."
Historical Mega-Breach Discoveries Continue
Yahoo isn't the only company to have revealed this year that it discovered a massive, historical breach that put users and their data at risk for years before it was discovered or fully understood. Other organizations that have found themselves in a similar situation this year have included Dropbox, LinkedIn, MySpace and Tumblr, among others. In some cases, organizations discovered that breaches that they had spotted were much worse than they believed. LinkedIn, in particular, found that a 2012 breach hadn't resulted in the theft of 6.5 million uses' accounts details, but rather involved 165 million accounts.
"We truly are under major siege and we're unprepared for it. It really is a national emergency," Avivah Litan, vice president at Gartner Research, tells USA Today. "We need a national response plan for this."
Managing Editor Jeremy Kirk also contributed to this story.

