Breach Preparedness , Cybersecurity , Data Breach
Internet of Things: Hacker Eavesdropping Smorgasbord Sheer Network Scale Offers Hope for Solving Related Challenges Phil Reitinger of the Global Cyber Alliance
Phil Reitinger of the Global Cyber AllianceImagine the cybersecurity implications of a world in which hundreds of millions of people have a physical impairment that leaves them internet-connected.
See Also: How to Illuminate Data Risk to Avoid Financial Shocks
Thanks to the "internet of things," that scenario is fast becoming reality in the form of internet-connected hearing aids. But like so many aspects of the internet of things, such devices carry upsides as well as big, potential data breach downsides, according to Phil Reitinger, the chief executive of the Global Cyber Alliance. He formerly was the Department of Homeland Security's top cybersecurity official as well as CISO for Sony.
In an opening keynote presentation Aug. 2 at Information Security Media Group's Fraud & Breach Prevention Summit New York, Reitinger noted that unlike some internet of things devices - toasters come to mind - internet-connected hearing aids, which are still in their infancy, offer a lot of promise for improving users' quality of life. When a user is watching a television show, for example, their hearing aids could identify the audio and instead of amplifying it, begin downloading a live audio stream of the broadcast.
But what happens when internet-enabled hearing aids enter the workplace? As with smartphones, the devices would be a natural target for attackers, because they could be exploited and used to facilitate remote surveillance, allowing hackers to "hear" whatever the wearer hears. And that would create risks for any such device wearer who works for an organization with access to classified or sensitive information.
Without appropriate safeguards being put in place, Reitinger claimed we risk a future in which attackers could perpetrate targeted breaches with little risk of their attacks being spotted or traced.
In that sort of a future, "things like the DNC [Democratic National Committee] hack, those are small potatoes ... because a huge number of people are walking listening devices," Reitinger said. "Everything is connected, everything is tied together."
Security Essential: Think Big
Everything will only continue to become more connected, and more data generated; that's our inevitable internet of things future. But from a security standpoint, it's possible to avoid some doomsday-style scenarios, provided we make some related moves, chief among them building networks that are as big as possible, Reitinger said.
"Right now, I think the bad guys have almost all of the advantages," he said. "But ... it's much tougher on the good guys than the bad guys. The bad guys operate at scale much better than the good guys."
Defenders, however, can learn to operate at scale, too. "We have to have an ecosystem that takes advantage of the one thing that the good guys and girls have, and that's the size of the network," he said.
At first glance, network size might seem to be a disadvantage, because it makes systems more complex and thus more difficult to secure. But larger networks also give organizations the ability to create what many organizations and vendors have been pushing for in recent years - larger sensor platforms, in which each endpoint or node can be tied into a massive, distributed security monitoring system. Together with better analysis and automation tools, these sensor platforms could be built to better spot an emerging attack, "acting like a biodefense system" that shuts the attack down, Reitinger said.
Some attacks would still get through, but such a system would enable defenders to more quickly block them, and continue to block them.
Short Term: Getting Worse
Of course, this approach might take decades to put into place. "My opinion is that things are very bad right now ... [and] that things are going to get worse, for at least the next 10 years," Reitinger said.
Even so, it's important to start identifying solutions to small parts of the problem now, finding ways to solve them and then building on that success, he said. In a call to arms that applies not just to addressing the internet of things but any enterprise information security challenge, no matter how insurmountable it might seem, Reitinger proclaimed: "Don't admire the problem - try to find something to solve, and then solve it."



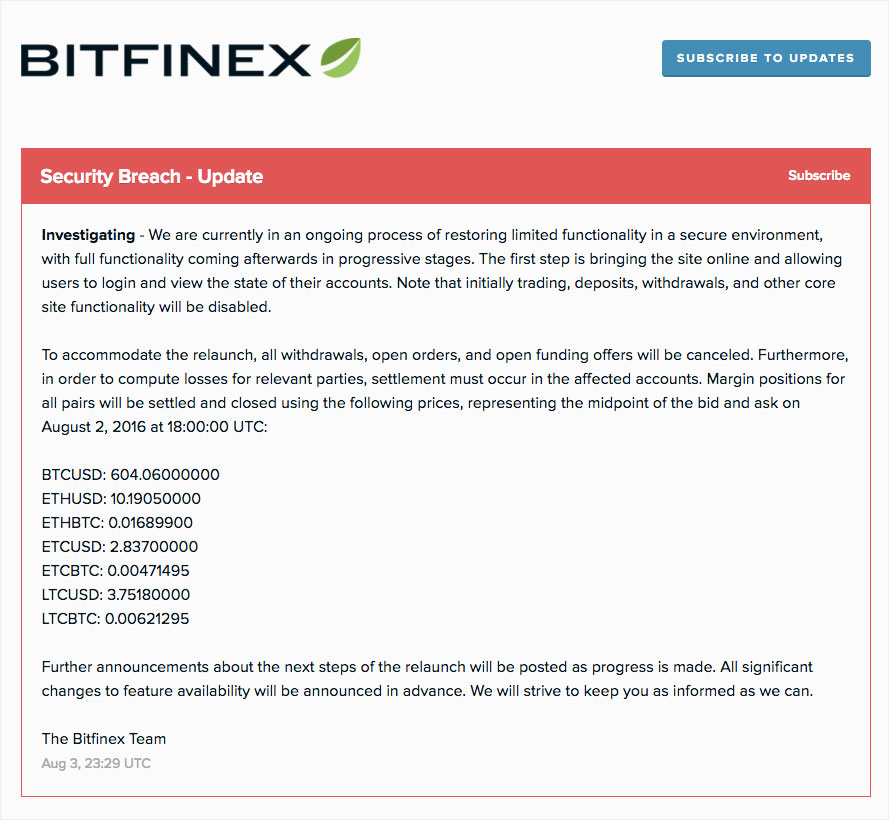 Notice from Bitfinex posted online
Notice from Bitfinex posted online
 Fraudsters are increasingly enhancing their schemes to make detection by traditional fraud models more difficult, and these shifting fraud patterns ultimately result in institutions continuously having to allocate additional resources. Furthermore, Fraud operations and investigations are faced with a constant flux in the volumes of caseloads and the types of investigations required. Organizations need a proactive strategy to effectively and efficiently identify and mitigate fraud risks, enhance client experience, reduce fraud losses and fraud cost, adhere to regulations and combat terrorist financing.
Advances in technology, authentication methods, and analytics over the past two years have led to the creation of a potential toolkit to combat this fraudulent trend, but it also present a new challenge to financial institutions. How do they select and incorporate those technologies as part of a rationalized prevention and detection approach? Leading institutions will utilize multiple authentication methods such as biometrics, device fingerprinting, soft tokens and other methods as part of a holistic real-time, risk-based, cross-channel/product approach, thus, reducing user interaction friction, increasing prevention and detection capabilities, and optimizing operation costs.
This session will highlight key elements to optimize fraud detection and prevention, including:
Increasing operational efficiency and enhancing client experience;
Building flexible and scalable operating models;
Enhancing authentication across channels and customers, while maintaining the customer experience;
Increasing effectiveness of fraud monitoring and analytics;
Moving toward a more holistic risk-based approach to managing fraud and financial crime.
You might also be interested in …
Fraudsters are increasingly enhancing their schemes to make detection by traditional fraud models more difficult, and these shifting fraud patterns ultimately result in institutions continuously having to allocate additional resources. Furthermore, Fraud operations and investigations are faced with a constant flux in the volumes of caseloads and the types of investigations required. Organizations need a proactive strategy to effectively and efficiently identify and mitigate fraud risks, enhance client experience, reduce fraud losses and fraud cost, adhere to regulations and combat terrorist financing.
Advances in technology, authentication methods, and analytics over the past two years have led to the creation of a potential toolkit to combat this fraudulent trend, but it also present a new challenge to financial institutions. How do they select and incorporate those technologies as part of a rationalized prevention and detection approach? Leading institutions will utilize multiple authentication methods such as biometrics, device fingerprinting, soft tokens and other methods as part of a holistic real-time, risk-based, cross-channel/product approach, thus, reducing user interaction friction, increasing prevention and detection capabilities, and optimizing operation costs.
This session will highlight key elements to optimize fraud detection and prevention, including:
Increasing operational efficiency and enhancing client experience;
Building flexible and scalable operating models;
Enhancing authentication across channels and customers, while maintaining the customer experience;
Increasing effectiveness of fraud monitoring and analytics;
Moving toward a more holistic risk-based approach to managing fraud and financial crime.
You might also be interested in …







 Mobile banking is the highest margin channel for your financial institution. It provides your organization with the profitability and customer engagement you have been seeking for decades. Your customers are eager to adopt this channel as 68% of them view it as the primary way they will bank within 2 years; however, customers overwhelming cite a lack of security as their biggest barrier to mobile channel adoption. Fortunately, with evident security measures in place, the vast majority of consumers report they would use mobile banking and payments. So, by taking steps to protect both your institution and your customers you also benefit from:
Increased customer confidence in mobile banking through a well communicated security program;
Higher market share through a secured and differentiated mobile banking service;
Higher adoption of mobile banking amongst your current customers;
Higher usage of high-margin mobile services like mobile bill pay, remote deposit capture, and mobile payments.
This session will highlight the prolific growth of mobile banking threats and the danger that these attacks pose to both your institution as well as your customers. The FFIEC recently issued guidance on how keep these treats, including malware, jailbreaking/rooting, insecure networks and unencrypted data, from exposing your customers, accounts and transactions to mobile banking fraud. The session will also examine the best practices, including the FFIEC recommendations, for securing mobile devices and applications so a financial institution is able to provide its customers with the convenience, security, and confidence they demand.
You might also be interested in …
Mobile banking is the highest margin channel for your financial institution. It provides your organization with the profitability and customer engagement you have been seeking for decades. Your customers are eager to adopt this channel as 68% of them view it as the primary way they will bank within 2 years; however, customers overwhelming cite a lack of security as their biggest barrier to mobile channel adoption. Fortunately, with evident security measures in place, the vast majority of consumers report they would use mobile banking and payments. So, by taking steps to protect both your institution and your customers you also benefit from:
Increased customer confidence in mobile banking through a well communicated security program;
Higher market share through a secured and differentiated mobile banking service;
Higher adoption of mobile banking amongst your current customers;
Higher usage of high-margin mobile services like mobile bill pay, remote deposit capture, and mobile payments.
This session will highlight the prolific growth of mobile banking threats and the danger that these attacks pose to both your institution as well as your customers. The FFIEC recently issued guidance on how keep these treats, including malware, jailbreaking/rooting, insecure networks and unencrypted data, from exposing your customers, accounts and transactions to mobile banking fraud. The session will also examine the best practices, including the FFIEC recommendations, for securing mobile devices and applications so a financial institution is able to provide its customers with the convenience, security, and confidence they demand.
You might also be interested in …





