Breach Preparedness
,
Critical Infrastructure Security
,
Cyberwarfare / Nation-state attacks
Readiness, Morale, Investigations and Recruitment at Risk as Standoff Persists(
jeremy_kirk) •
January 11, 2019

There's a stark message on the front page of the U.S. National Institute of Standards and Technology's website: "NOTICE: Due to a lapse in federal funding, most of this website is not available."
See Also: Live Webinar | Sunset of Windows Server 2008: Migrate with Docker
The warning points to the continuing standoff between President Donald Trump and Congress over the $5.7 billion he wants to fund a fortified border wall with Mexico.
Trump says he won't sign a spending bill for fiscal 2019 that would reopen the government that lacks the funding he wants for the wall. Building the wall was one of his key campaign promises that attracted voters worried about illegal immigration.
The government shutdown, which started on Dec. 21, 2018, is affecting as many as 800,000 federal workers, some of whom are continuing to work without pay. With the Democrats in control of the House of Representatives and neither party showing signs of budging, it's unclear how the standoff will be resolved.

Tom Kellermann
The shutdown is affecting agencies that have a key hand in the nation's cybersecurity readiness, such as the Department of Homeland Security. That is generating anxiety over whether it could impact the U.S.'s defenses and whether opportunistic adversaries may seize the moment.
"I am not sleeping well," says Tom Kellermann, chief cybersecurity officer for the vendor Carbon Black. "The U.S. is under siege by Chinese, Russian and North Korean cyber spies, and now we do not have sufficient watchers on the wall. We have never been this vulnerable to asymmetrical warfare."
Kellermann says that when the government returns to normal, the "first order of business will be to immediately conduct compromise assessments and suppress the adversaries who have infiltrated government systems."
NIST: We're Mostly Closed
Prior to the lapse in funding, the Commerce Department published a comprehensive document detailing how agencies would be pared down.
And while much has been cut back, vital cybersecurity functions - including defending networks and cooperating with the private sector to investigate intrusions - are continuing, says Michael Daniel, CEO of the Cyber Threat Alliance.

Michael Daniel
But the longer the shutdown continues, the more impact it will have, says Daniel, who served as White House cybersecurity coordinator between 2012 and 2017.
"Like so many areas across the government, over time a shutdown will steadily erode the federal government's cybersecurity readiness," he says.
One of the most affected agencies is NIST, the U.S. government's science laboratory that develops specification and standards for everything from cryptography to microbial systems to quantum electromagnetics. Much of its staff has been furloughed, and its website has been mostly shut down.
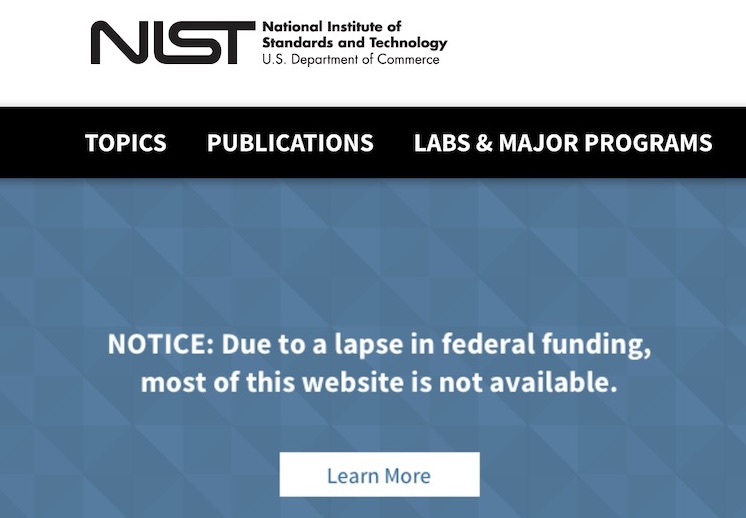
NIST's website is mostly disabled.
NIST's guidelines on computer security are used within the U.S. but the agency's advice is respected and followed worldwide. The shutdown means that work on that kind of guidance will be delayed.
"New policy work is essentially frozen, so needed changes or updates to existing policies will not occur, nor will the government develop policies to address new areas," Daniel says.
Chris Morales, head of security analytics at Vectra, says it's understandable much of NIST would be subject to closure because it's primarily a research and publication institute. Morales says it might be concerning that some individuals couldn't reach the organization's Cybersecurity Framework, but that document is still available via a direct link.
Still Running: NVD, US-CERT
A key part of NIST, the National Vulnerability Database, remains open. The NVD is the U.S. government's compilation of the latest software vulnerabilities, which is combined with analysis and mitigation information.
The NVD will continue to be staffed by a computer scientist and an IT specialist, according to a report in Decipher, a security news site sponsored by Duo Security, which was acquired by Cisco last year.
The Commerce Department has also said NIST's timing infrastructure, which is essential for synchronizing computer clocks, will remain running. Also, the U.S. Computer Emergency Readiness Team, which is part of the Department of Homeland Security, is continuing to publish alerts.
Fortunately, that means some of the most important work is continuing but likely at the cost of longer-term sacrifice, says John Bambenek, vice president of security research and intelligence at ThreatSTOP.
"That said, government workers are working in many cases without support staff, which does have some ancillary impacts," Bambenek says.
It might also pinch a new initiative. In November 2018, a new organization called the Cybersecurity and Infrastructure Security Agency, or CISA, was created after Trump signed the Cybersecurity and Infrastructure Security Agency Act of 2018.
"Thus, over time, personnel slots will go unfilled and contracts will expire, making it difficult to sustain the workforce or upgrade equipment."
—Michael Daniel, Cyber Threat Alliance
The agency is aimed at being a hub for threats affecting infrastructure and providing incident response and defensive capabilities for the government in cooperation with the private sector. But Decipher reports that 45 percent of its staff has been furloughed.
That may make it harder for the new agency to gain momentum when funding returns. Daniel says that shutdowns tend to affected support activities disproportionately, including hiring and letting of contracts.
"Thus, over time, personnel slots will go unfilled and contracts will expire, making it difficult to sustain the workforce or upgrade equipment," Daniel says.
Shutdown Hurts FBI Investigations
The shutdown is also affecting activities that could have a long-term cybersecurity impact in other ways. The FBI, for example, reports that the shutdown is compromising its ability to run operations or pay informants.
The FBI Agents Association, meanwhile, reports that many FBI agents have a security clearance, which relies on them avoiding debt. But with agents not getting paid, they are at greater risk of going into debt and losing their clearance, which could further compound the bureau's operational readiness. "Financial security is a matter of national security," the group warns in an open letter.
Government Certificates Expire
Other signs of the shutdown's security impact also continue to magnify. U.K. anti-cybercrime firm Netcraft on Thursday warned that due to the shutdown, more than 80 TLS certificate for .gov websites have not been renewed, thus making them inaccessible due to the stronger protections now in place in modern browsers. In some cases, the sites can still be accessed, but only if users click through security alerts warning that the sites may not be secure, in violation of good browser security practices.
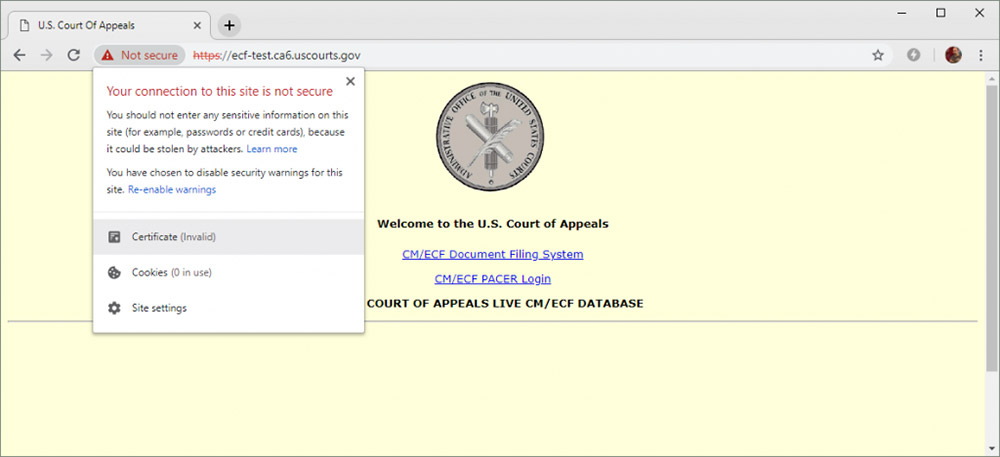
This U.S. Court of Appeals website, which provides links to a document filing system as well as the Public Access to Court Electronic Records - PACER - expired on Jan. 5 and has yet to be renewed. (Source: Netcraft)
"Dozens of U.S. government websites have been rendered either insecure or inaccessible during the ongoing U.S. federal shutdown," Netcraft says. "These sites include sensitive government payment portals and remote access services, affecting the likes of NASA, the U.S. Department of Justice and the Court of Appeals."
Declining Morale
The shutdown also carries a public relations cost. Cybersecurity is a hot industry: There simply aren't enough skilled people to fill the jobs created by the fast-growing field. While public service is respected, the pay doesn't come close to that offered by private companies.
It means that for those government workers going without a paycheck, a new employer - and a pay raise - could be just an email or a phone call away.
"Long term, I think it kills us on retention and morale," ThreatSTOP's Bambenek says. "If an incident happens I think they'll find a way to make it work. But I'd assume the recruiting and retention impact lasts years beyond the shutdown."
CTA's Daniel says that a prolonged shutdown could also dim people's views of public service if they've never had a government job before.
"The shutdown certainly deters some people from even considering working for the government," he says. "And even when it's done, the specter of the shutdown will linger as a deterrent for people considering whether to take a government cybersecurity position."
(Executive Editor Mathew Schwartz also contributed to this story.)







 Categories of websites hosting content requested for delisting, from Jan. 22, 2016, through Jan. 11, 2019 (Source: Google)
Categories of websites hosting content requested for delisting, from Jan. 22, 2016, through Jan. 11, 2019 (Source: Google)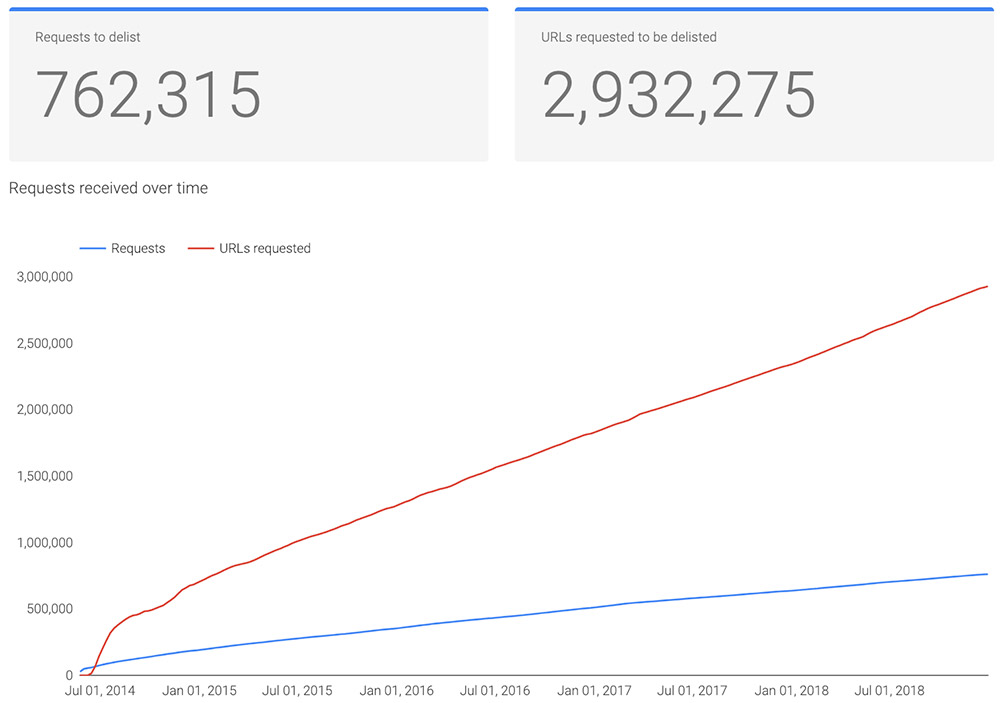 Delisting requests sent to Google from Jan. 22, 2016, through Jan. 11, 2019
Delisting requests sent to Google from Jan. 22, 2016, through Jan. 11, 2019
 Tom Kellermann
Tom Kellermann Michael Daniel
Michael Daniel NIST's website is mostly disabled.
NIST's website is mostly disabled. This U.S. Court of Appeals website, which provides links to a document filing system as well as the Public Access to Court Electronic Records - PACER - expired on Jan. 5 and has yet to be renewed. (Source: Netcraft)
This U.S. Court of Appeals website, which provides links to a document filing system as well as the Public Access to Court Electronic Records - PACER - expired on Jan. 5 and has yet to be renewed. (Source: Netcraft)