Breach Preparedness , Breach Response , Data Breach
Democrats Slam Republican Report for Not Advancing New Breach-Prevention Laws(euroinfosec) • December 11, 2018
The hack attack and subsequent data breach suffered by credit reporting agency Equifax in 2017 "was entirely preventable," says the Republican majority staff of the U.S. House of Representatives Committee on Oversight and Government Reform.
See Also: Five Steps to Masterminding an Effective Security Awareness Program
Those findings are contained in a 96-page report issued by the committee's majority staff on Monday. Following its publication, however, two Democratic lawmakers slammed the report for being devoid of legislative proposals or oversight changes that would help to prevent these types of breaches, and they released their own set of recommendations.
Equifax, one of the world's biggest credit reporting agencies, profits from accumulating and selling personal information. "Equifax, however, failed to implement an adequate security program to protect this sensitive data,'" according to the Republicans' report. "As a result, Equifax allowed one of the largest data breaches in U.S. history. Such a breach was entirely preventable."
The breach compromised personal data for 148 million individuals in the U.S, or 56 percent of all American adults, representing nearly half of the total U.S. population. The breach also exposed information for 15 million U.K. citizens and about 20,000 Canadians.
Equifax had numerous security defenses in place, but it failed to use them to full effect, according to the majority report.
"Equifax failed to fully appreciate and mitigate its cybersecurity risks," according to the report, which notes that the company failed to spot a breach that began on May 23, 2017, and lasted for 76 days. "Had the company taken action to address its observable security issues prior to this cyberattack, the data breach could have been prevented."
Equifax has responded to that report by saying it had scant time to review the findings prior to its release. Even so, "we identified significant inaccuracies and disagree with many of the factual findings," the company says in a statement.
Follows GAO, ICO Reports
The House report follows the September release of a report on the breach by the U.S. Government Accountability Office (see: Postmortem: Multiple Failures Behind the Equifax Breach).
Also that month, the U.K. Information Commissioner's Office, which enforces the U.K.'s data privacy laws, announced the results of its probe into the breach. The ICO imposed a £500,000 ($630,000) fine on Equifax, which was the maximum possible penalty allowed under the pre-General Data Protection Regulation law in effect at the time of the breach. The ICO found that Equifax violated more than half of the country's applicable data protection principles. In one particularly egregious example, the credit bureau was storing personal information, including plaintext passwords, in a testing environment (see: Equifax Hit With Maximum UK Privacy Fine After Mega-Breach).
The only other organization in history to be hit with the maximum possible fine by the ICO has been Facebook, for the string of failures that helped precipitate the Cambridge Analytica breach.
How to Fail to Block a Breach
The House Oversight report doesn't reveal any new smoking guns in what has now become a case study about failures in management, IT oversight and information security practices and procedures. But it does again clearly lay out the long list of missteps that helped facilitate the breach.
"In total, I count 34 control and process failures that contributed to the Equifax breach," tweets information security expert Adrian Sanabria, vice president of strategy and product marketing at vulnerability remediation firm NopSec. "Perhaps five or so could have prevented the breach entirely. Many of the remaining 29 could have detected the breach in enough time to stop it."
Legacy System Didn't Get Patched
One of Equifax's chief missteps was its failure to patch its Automated Consumer Interview System, or ACIS, which the report describes as being "a custom-built internet-facing consumer dispute portal developed in the 1970s, [which] was running a version of Apache Struts containing the vulnerability."
Equifax failed to patch an Apache Struts installation that was running ACIS, and it was was this instance of Struts that attackers successfully exploited, the report says (see: Equifax's Colossal Error: Not Patching Apache Struts Flaw).
Subsequently, Equifax failed to spot that attackers were querying internal databases and then exfiltrating data. "Attackers sent 9,000 queries on these 48 databases, successfully locating unencrypted personally identifiable information (PII) data 265 times," according to the report.
The attackers transferred this data out of the Equifax environment, unbeknownst to Equifax, it says. "Equifax did not see the data exfiltration because the device used to monitor ACIS network traffic had been inactive for 19 months due to an expired security certificate."
This was not a problem unique to Equifax's data exfiltration technology. "At the time of the breach ... Equifax had allowed at least 324 of its SSL certificates to expire," the report says, "including 79 certificates for monitoring business-critical domains."
After Equifax finally renewed the expired certificate for its data exfiltration monitoring device on July 29, 2017, its administrators "immediately noticed suspicious web traffic," the report says, leading to the breach finally being detected.
Attacks Found Unencrypted Credentials
Before that, however, attackers had exploited the Struts flaw and installed 30 "web shells" - web-based backdoors - across Equifax's network.
Thanks to these web shells, "they found a file containing unencrypted credentials (usernames and passwords), enabling the attackers to access sensitive data outside of the ACIS environment," according to the report. "The attackers were able to use these credentials to access 48 unrelated databases." (See: Why Was Equifax So Stupid About Passwords?)
The GAO report said that attackers successfully stole data from a total of 51 databases.
Two Primary Points of Failure
The report cites a lack of accountability at Equifax, including "no clear lines of authority in Equifax's IT management structure existed." In addition, "Equifax's aggressive growth strategy and accumulation of data resulted in a complex IT environment," including it continuing to run - rather than replace - a number of custom-built legacy systems.
"Both the complexity and antiquated nature of Equifax's IT systems made IT security especially challenging," the report says. "Equifax recognized the inherent security risks of operating legacy IT systems because Equifax had begun a legacy infrastructure modernization effort. This effort, however, came too late to prevent the breach."
Republicans Recommend Voluntary Changes
The report lists seven recommendations in light of the Equifax breach, including a call to "empower consumers through transparency." This would entail requiring consumer reporting agencies to "offer consumers a free, simple summary explaining the data collected on the individual." It also recommends considering whether breached businesses should provide more than one year of prepaid identity theft monitoring to breach victims.
The report also suggests giving the Federal Trade Commission more power to "monitor CRA data security practices, both prior and subsequent to a breach occurring, and incentivize CRAs to adequately safeguard the consumer data they store." And it says that federal agencies, including the Securities and Exchange Commission, "should continue to encourage the public disclosure of cyber risks to increase awareness of a company's cybersecurity posture."
But the recommendations, with their focus on incentives and encouragement, focus only on voluntary moves. They include no recommendations that would directly give consumers greater privacy rights or penalize organizations that mishandle people's personal information.
Democrats Press for New Regulations
Two Democratic lawmakers have slammed the Republican members of the House Oversight Committee for failing to advance new legislative or oversight measures. They also said the report offers little of substance beyond what was already included in the GAO's report and news media reports.
"Unfortunately, committee Republicans issued a report without including Democratic suggestions to prevent data breaches in the future," said Rep. Elijah E. Cummings of Maryland, who's the ranking member of the House Oversight Committee, and Rep. Eddie Bernice Johnson of Texas, who's the ranking member of the House Committee on Science, Space and Technology, in a statement.
Their committees had run joint, bipartisan probes into the Equifax breach, and they expressed surprise at the Oversight committee's majority issuing its own report. "This was a missed opportunity to convert the committees' oversight efforts into concrete reforms that would help prevent future data breaches, hold companies accountable and protect American consumers and their sensitive personal information," they said.
On Monday, the Democratic lawmakers issued a seven-page report, prepared by the staff of their two committees, titled "What the Next Congress Should Do to Prevent a Recurrence of the Equifax Data Breach."
The minority report includes a number of legal and oversight steps that the lawmakers say would help prevent breaches, including a federal data breach notification law as well as giving the FTC more power to impose civil penalties on businesses that mishandle PII.
Equifax Sees 'Significant Inaccuracies' in Majority Report
In a statement sent to Information Security Media Group, Equifax says that it was not given sufficient time to prepare a response to the House Oversight Committee's majority report.
"We are deeply disappointed that the committee chose not to provide us with adequate time to review and respond to a 100-page report consisting of highly technical and important information. During the few hours we were given to conduct a preliminary review, we identified significant inaccuracies and disagree with many of the factual findings," Equifax says in its statement.
"Equifax has worked in good faith for nearly 15 months with the committee to be transparent, cooperative and shed light on our learnings from the incident in order to enrich the cybersecurity community," it says. "While we believe that factual errors serve to undermine the content of the report, we are generally supportive of many of the recommendations the committee laid out for the government and private industry to better protect consumers, and have already made significant strides in many of these areas."


 Google's campus in Mountain View, California. (Photo:
Google's campus in Mountain View, California. (Photo:  Some of the types of data supplied by Google's People API for Google+, which the search giant says inadvertently exposed user data to app developers (Source: Google)
Some of the types of data supplied by Google's People API for Google+, which the search giant says inadvertently exposed user data to app developers (Source: Google) Baylor Scott & White Medical Center - Frisco reported a breach involving a credit card processing system.
Baylor Scott & White Medical Center - Frisco reported a breach involving a credit card processing system. Under GDPR, organizations that suffer certain types of breaches must inform the ICO within 72 hours of learning that they have been breached.
Under GDPR, organizations that suffer certain types of breaches must inform the ICO within 72 hours of learning that they have been breached.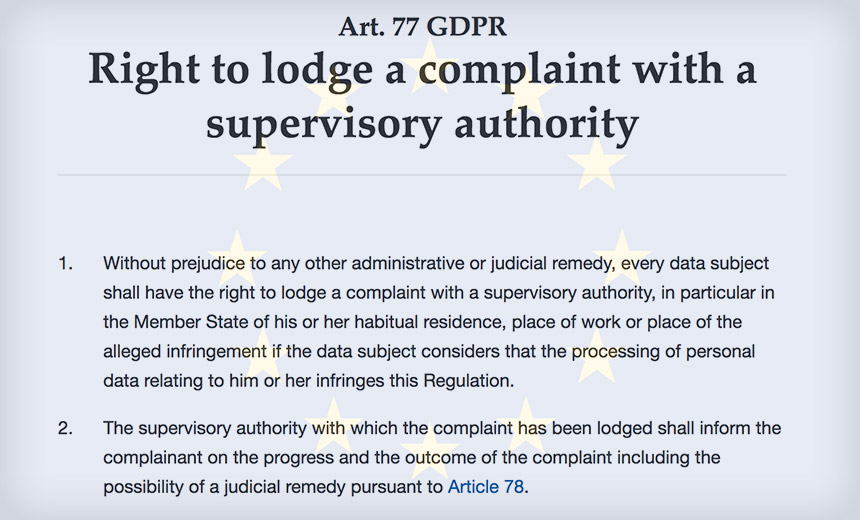 Excerpt from the
Excerpt from the