Fraud News
Data Breach , Governance , HIPAA/HITECH
Hospital Pays $75,000 Penalty in Case Involving Lost Unencrypted Devices(HealthInfoSec) • December 20, 2018 Massachusetts Attorney General Maura Healey
Massachusetts Attorney General Maura HealeyIn the latest HIPAA enforcement action taken by a state, Massachusetts Attorney General Maura Healey's office has signed a $75,000 consent judgement with McLean Hospital, a psychiatric facility, for a breach that affected 1,500 individuals.
See Also: Third-Party Cyber Risk Management - A Data-Driven Approach
The HITECH Act of 2009 gave state attorneys general the authority to bring civil actions for violations of the HIPAA privacy and security rules.
Among other recent HIPAA-related enforcement actions by states, the New Jersey attorney general's office on Dec. 10 announced a $100,000 settlement in a case involving health insurer EmblemHealth for a 2016 breach that exposed Social Security numbers on mailings to more than 81,000 plan members.
In March, that same EmblemHealth breach resulted in a $575,000 settlement with New York's attorney general's office involving the insurer's business associate, United Parcel Service Mailing Innovations.
—David Holtzman, CynergisTek
New Jersey's attorney general took action in another HIPAA case in April, smacking medical practice Virtua Medical Group with a $418,000 penalty for a 2016 breach. That was followed in November by a $200,000 settlement with the vendor involved in that incident, which did business as Best Medical Transcription.
State Activity Uptick
State AGs are finding that by bringing actions through their authority to enforce the HIPAA standards, and incorporating additional violations of state-enacted data security or consumer protection laws, they can pose substantial penalties that "get the attention of the public and other healthcare organizations," notes privacy attorney David Holtzman, vice president of compliance at the security consultancy CynergisTek.
"We are clearly seeing an uptick in state attorneys general filling a void through enforcement of the HIPAA rules when the Department of Health and Human Services' Office for Civil Rights has been perceived as falling short of its mission to hold accountable organizations failing to effectively safeguard personally identifiable health information from unauthorized access."
McLean Hospital Settlement
In a statement about the settlement with Belmont-based McLean Hospital, Healey's office says the case centers on a former employee who failed to return four unencrypted backup computer tapes containing personal and health information of patients, employees and deceased donors of the Harvard Brain Tissue Resource Center.
The hospital violated HIPAA as well as the state Consumer Protection Law and the Massachusetts Data Security Law when it failed to properly protect patients' information, the AG's office says.
McLean Hospital is part of the Boston-based integrated health system Partners HealthCare, which has also been the subject of a handful of other HIPAA-related enforcement cases in recent years.
That includes a $1 million HIPAA settlement in 2011 citing Partners' Massachusetts General Hospital and its physicians for a 2009 breach case involving the loss of scheduling documents for 192 patients in the hospital's General Infectious Disease Associates outpatient practice, including those with HIV/AIDS.
Missing Back-Up Tapes
In the McLean Hospital case, the Massachusetts AG's office alleges that the facility allowed an employee to regularly take home eight unencrypted back-up tapes containing clinical and demographic information from the Harvard Brain Tissue Resource Center. The tapes contained personal information, such as names, Social Security numbers, diagnoses and family histories.
"When the employee was terminated from her position at McLean in May 2015, she only returned four of the tapes, and the hospital was unable to recover the others," the statement from Healey's office says.
The AG also claims several other failures by McLean to identify, assess and plan for security risks, including failing to properly train employees, report the loss of the tapes in a timely manner and encrypt portable devices containing personal information.
"Hospitals must take measures to protect the private information of their patients," Healey says. "This settlement requires McLean Hospital to implement a new information security program and train its staff on how to properly handle the private information of those they serve."
In a statement provided to Information Security Media Group, McLean Hospital says that since this incident, the hospital has "continued to enhance its privacy and security practices and procedures within the brain bank and throughout the research operation. The agreement with the attorney general represents a continuation of those efforts. "
Taking the Right Steps
"Organizations maintaining personally identifiable information must account for security threats created when employees are permitted or required to remove from the worksite devices or media on the data is stored," Holtzman says.
"If you have employees that are removing the data or working remotely, it's important to make a list of the level of information to which they have access."
Organizations should encrypt PII and PHI stored on any devices or media, he says. "Keep logs of the data that is stored on portable devices and removable media. Track the movement of devices and media on which PII is stored as well as conduct periodic audits to ensure that the data can be accounted for."
Yapstone Holdings Settlement
Healey's office also announced this week a $155,000 breach-related settlement with payments processing firm Yapstone Holdings Inc. That case stemmed from exposure via the internet of the personal information of consumers, including bank account and Social Security numbers, addresses, and driver's license numbers.
The AG says Yapstone violated Massachusetts data security regulations.
The AG's office began its investigation after Yapstone notified the office of the incident in 2015.
The investigation into the incident revealed that in July 2014, while modifying Yapstone's website, the company's engineers accidentally removed password protections from public-facing websites used to sign users up for Yapstone's service.
The mistake rendered the webpages publicly viewable to anyone on the internet for more than a year, the AG's statement says. The investigation found that Yapstone employees appeared to have been aware of the vulnerability in August 2014 but neglected to fix it until August 2015, when another employee discovered it.
In addition to the financial penalty, the settlement requires Yapstone to hire a CISO, train employees on data security and assess and update information security policies relating to changes to its systems and to external vulnerabilities.
Cybercrime , Cyberwarfare / Nation-state attacks , Fraud Management & Cybercrime
Prosecutors Say They Were Part of APT10 Group and Had Government Ties(HealthInfoSec) • December 20, 2018
The U.S. Department of Justice on Thursday unsealed an indictment charging two Chinese nationals in connection with a cyber espionage campaign, alleging they acted in association with a government agency.
See Also: Third-Party Cyber Risk Management - A Data-Driven Approach
"The indictment alleges that the defendants were part of a group that hacked computers in at least a dozen countries and gave China's intelligence service access to sensitive business information," said Deputy Attorney General Rod Rosenstein.
The indictment, which was preceded by similar indictments of Chinese nationals revealed in October, could further increase U.S. tensions with China. The U.S. reached a landmark agreement with China in 2015 to stop cyberattacks aimed at stealing intellectual property. But after a lull, experts say suspected China-backed attacks have resumed.
The security industry has often referred to the group as APT 10 or "Cloud Hopper," because the attackers targeted IT managed service providers (MSPs). Because MSPs serve many corporate customers, it meant that a successful attack against one MSP could result in the compromise of many more companies.
"APT10 has been tracked by FireEye for years and is one of the most prolific cyber espionage groups", says Ben Read, senior manager, cyber espionage analysis, with FireEye.
Chris Pierson, CEO of BlackCloak, says attacking MSPs can result in high return for hackers.
"Why attack one specific target company when you can attack someone who can give you access to one thousand other companies or their intellectual property?" Pierson says.
Members of APT10 Group
The Justice Department says the two hackers - Zhu Hua and Zhang Shilong, who both go by a variety of other aliases - were members of the APT10 hacking group operating in China.
—Dermot O'Reilly, U.S. Department of Defense
Prosecutors say the two defendants worked for the Chinese company Huaying Haitai Science and Technology Development Company - or Huaying Haitai - and acted in association with the Chinese Ministry of State Security's Tianjin State Security Bureau.
The two are charged with conspiracy to commit computer intrusions, conspiracy to commit wire fraud and aggravated identity theft.
Prosecutors say that through their involvement with the APT10 Group, from about 2006 to about 2018, the two conducted global campaigns of computer intrusions targeting, among other data, intellectual property and confidential business and technological information at managed service providers.
Those MSPs remotely manage the information technology infrastructure of businesses and governments around the world. Those targeted included more than 45 technology companies in at least a dozen U.S. states, and U.S. government agencies, the DOJ notes.
The APT10 Group targeted a diverse array of commercial activity, industries and technologies, including aviation; satellite and maritime technology; industrial factory automation; automotive supplies; laboratory instruments; banking and finance; telecommunications and consumer electronics; computer processor technology; information technology services; packaging; consulting; medical equipment; healthcare; biotechnology; pharmaceutical manufacturing; mining; and oil and gas exploration and production, the DOJ says.
"Among other things, Zhu and Zhang registered IT infrastructure that the APT10 Group used for its intrusions and engaged in illegal hacking operations," prosecutors say.
"The theft of sensitive defense technology and cyber intrusions are major national security concerns and top investigative priorities for the DCIS," said Dermot O'Reilly, director of the Defense Criminal Investigative Service of the U.S. Department of Defense.
Extensive Espionage Campaigns
Prosecutors say members of the APT 10 Group, including Zhu and Zhang, conducted extensive campaigns of intrusions into computer systems around the world. The group used some of the same online facilities to initiate, facilitate and execute its campaigns during the conspiracy.
Beginning in about 2014, members of the APT10 Group, including Zhu and Zhang, targeted MSPs to leverage their networks to gain unauthorized access to the computers and computer networks of the MSPs' clients and to steal, among other data, intellectual property and confidential business data on a global scale, prosecutors allege.
"For example, through the MSP theft campaign, the APT10 Group obtained unauthorized access to the computers of an MSP that had offices in the Southern District of New York and compromised the data of that MSP and certain of its clients ..." prosecutors say.
Earlier, beginning about 2006, members of the APT10 Group, including Zhu and Zhang, engaged in an intrusion campaign to obtain unauthorized access to the computers and computer networks of more than 45 technology companies and U.S. government agencies in order to steal information and data concerning a number of technologies, prosecutors say.
Through this technology theft campaign, the APT10 Group stole hundreds of gigabytes of sensitive data and targeted the computers of victim companies in several industries, according to DOJ.
As part of the APT10 Group's intrusion campaigns, Zhu and Zhang, worked for Huaying Haitai and registered malicious domains and infrastructure. In addition, Zhu, a penetration tester, engaged in hacking operations on behalf of the APT10 Group and recruited other individuals to the APT10 Group, and Zhang developed and tested malware for the APT10 Group, prosecutors say.
APT10 touched many countries. Australia issued a warning in April 2017 about attacks against global MSPs, some of which had operations in the country. The Australian Cyber Security Centre said it was working with international partners to track the activity.
On Friday, the Australian government warned that China risks abrogating commitments it made at the G20 meeting in 2017 and separately with Australia in 2017 regarding cyberattacks.
"Australia calls on all countries - including China - to uphold commitments to refrain from cyber-enabled theft of intellectual property, trade secrets and confidential business information with the intent of obtaining a competitive advantage," according to a statement from Foreign Affairs Minister Marisa Payne and Home Affairs Minister Peter Dutton.
On Thursday, the U.K. Foreign Minister Jeremy Hunt warned governments against undertaking attacks aimed at intellectual property and commercial data.
"Our message to governments prepared to enable these activities is clear: together with our allies, we will expose your actions and take other necessary steps to ensure the rule of law is upheld," Hunt says.
U.S. Legal Pressure On China
On Oct. 18, federal prosecutors filed an indictment of two Chinese intelligence officers and eight others for stealing trade secrets intended to help the country shortcut the development of a turbofan airplane engine plus other technology (see U.S. Again Indicts Chinese Intel Agents Over Hacking).
In that case, prosecutors said the two officers, Chai Meng and Zha Rong, worked for the Jiangsu Province Ministry of State Security in Nanjing, a provincial foreign intelligence arm of the People's Republic of China's Ministry of State Security.
The two men were accused of orchestrating an extensive scheme running between January 2010 to May 2015 that recruited other hackers to gain access to companies as well as recruiting insiders to plant malware.
And on Oct. 10, the Justice Department announced that an alleged Chinese Ministry of State Security officer had been charged with economic espionage and attempting to steal trade secrets. Yanjun Xu was arrested in Belgium and extradited to the U.S. He's accused of stealing data from "multiple U.S. aviation and aerospace companies."
DigiCert just conducted a global study of how organizations across sectors are approaching IoT security. What are some of the best practices of the organizations that emphasize securing connected devices? Mike Nelson of DigiCert shares the findings.
In all, the survey attracted more than 700 responses from individuals with hands-on experience with connected devices, says Nelson, VP of IoT Security at DigiCert. And the results showed sharp differences between organizations that have a handle on IoT security and those that don't.
"There are dramatic differences between the top and the bottom [performers re: IoT security]," he says. "Organizations that are successfully implementing security are reaping a lot of benefits - monetary, reputational ..."
In an interview about IoT security, Nelson discusses:
Real consequences companies have faced because of IoT-related breaches; Key results of DigiCert's IoT study; Lessons learned from the most IoT-savvy organizations.Nelson is the VP of IoT Security at DigiCert, a global leader in digital security. In this role, Nelson oversees the company's strategic market development for the various critical infrastructure industries securing highly sensitive networks and Internet of Things (IoT) devices, including healthcare, transportation, industrial operations, and smart grid and smart city implementations. Nelson frequently consults with organizations, contributes to media reports, participates in industry standards bodies, and speaks at industry conferences about how technology can be used to improve cyber security for critical systems and the people who rely upon them.
Nelson has spent his career in healthcare IT including time at the US Department of Health and Human Services, GE Healthcare, and Leavitt Partners - a boutique healthcare consulting firm. Nelson's passion for the industry stems from his personal experience as a type 1 diabetic and his use of connected technology in his treatment.
 (Image: ACSC)
(Image: ACSC)
Nine global service providers are known to have been compromised in attacks by China's APT10 group, according to Alastair MacGibbon, head of the Australian Cyber Security Centre (ACSC).
On Friday, the US formally attributed these attacks to China's Ministry of State Security (MSS) in its indictment of two Chinese nationals who it alleges are members of the group.
APT10 is the name given to the group by FireEye. Other names assigned to it are Red Apollo (PwC), CVNX (BAE Systems), Stone Panda (CrowdStrike), POTASSIUM (Microsoft), and MenuPass (Trend Micro).
Hewlett Packard Enterprise (HPE) and IBM are among the MSPs affected, Reuters reported on Friday. The companies were infiltrated "multiple times in breaches that lasted for weeks and months", the report said, although neither company has commented officially.
"We're not naming any managed service providers," MacGibbon told ZDNet.
"One, we said we wouldn't name them. And two, I can't be sure, and none of our allies can be sure, that we know all of the compromised global providers," he said.
"We know of, I think, nine global service providers that have been compromised... And they're the ones we know about. Very Rumsfeldian, but it's what you don't know that is problematic. The unknown unknowns."
The ACSC does not know how many of the MSPs' customers have been affected either, MacGibbon said.
In part that is because of the "subtlety" and "sophistication" of the attacks, and in part because of the way the MSPs have built their systems to be "scaleable and global in nature".
"[This] often means that they don't segment, and do other things to their networks, that you would argue is sensible," he said.
Australian customers of compromised MSPs have not been named, but MacGibbon says that globally the targets have been organisations like mining companies, tech companies, and those involved in advanced manufacturing.
"It's commercial secrets. It's not about the traditional strategic intelligence. It's not about, frankly, defence systems, or secrets from governments... [It's] all of those things where a country may want to win in that competition, stealing the lifeblood from their competitors in the West," MacGibbon said.
"The reason why I said on RN [the Australian Broadcasting Corporation's Radio National] that I don't believe but can't prove that government entities are being victims is because generally the way government uses outsourced IT providers is different to how some corporates will. We put in place some different architectures."
But why name China now?
A key question is why China is being called out now.
In April 2017, Premier Li Keqiang and then Prime Minister Malcolm Turnbull signed an agreement to refrain from the cyber-enabled theft of intellectual property, trade secrets, or confidential business information.
The activities of APT10 had been revealed just two weeks beforehand in PwC's Operation Cloud Hopper report, produced in conjunction with BAE Systems and the UK's National Cyber Security Centre (NCSC).
"As a result of our analysis of APT10's activities, we believe that it almost certainly benefits from significant staffing and logistical resources, which have increased over the last three years, with a significant step-change in 2016," PwC wrote at the time.
In April this year, the NCSC warned that third-party suppliers were now an organisation's weakest link, citing the success of Cloud Hopper as an example.
And as recently as last month, joint Fairfax Media/Nine News reporting confirmed that China's Ministry of State Security is behind Cloud Hopper.
MacGibbon uses what he called his "tortured" doctor analogy. If you're in pain, a doctor might at first advise a couple of days off work, and to come back if pain persists. Next might come manipulation of the limb, and so on.
"We're now into what I call radical surgery phase. We've tried other things. Clearly, to dislodge the threat actor themselves, and to send a message to them, in this case APT10 working on behalf of the Ministry of State Security (MSS) in China.
"That's an important lever we need to pull to get them to change."
This is presumably part of the coordinated diplomatic campaign against nation-states breaching the so-called "cyber norms" that named Russia as the nation-state actor behind the NotPetya attack, and blamed North Korea for the WannaCry incident.
But the ACSC's announcement is also intended to drive action inside Australia's economy.
The ACSC's website has posted advice for Australian businesses in the wake of the MSP breaches.
"[MSPs] need to change the way they do their business, because if they are compromised it could potentially compromise all of their customers. Then those that consume those services, what can you do to architect this arrangement to still get the benefits of outsourced IT and reduce the risks," MacGibbon said.
"So it's a wake-up call, and we're using, frankly, naming the MSS as a fulcrum to create leverage to change the way we behave domestically."
MacGibbon acknowledges that it's "not the best time of year" to launch an awareness campaign, however. He cites the US indictments as a trigger for it happening now.
"Once everyone's eaten enough turkey and had enough ham, we'll be back out again to drive change, where we hope that members of boards, CEOs, and customers start asking questions on how to change the way they construct their IT systems."
Related Coverage
US charges two Chinese nationals for hacking cloud providers, NASA, the US Navy
The two Chinese nationals were members of the infamous APT10 cyber-espionage group, DOJ said.
DHS aware of ongoing APT attacks on cloud service providers
Attacks most likely linked to APT10, a Chinese cyber-espionage group, also known as Red Apollo, Stone Panda, POTASSIUM, or MenuPass.
Advanced Chinese hacking campaign infiltrates IT service providers across the globe
'Cloud Hopper' campaign by sophisticated APT10 hacking group uses advanced phishing and customised malware to conduct espionage.
Elite Chinese hackers target board directors at some of the world's largest firms
The APT 10 hacking group has struck again, this time using a watering hole attack to compromise the National Foreign Trade Council website and gather sensitive data about its directors.
Top 4 security threats businesses should expect in 2019 (TechRepublic)
Cybercriminals are developing more sophisticated attacks, while individuals and enterprises need to be more proactive in security practices.
3rd Party Risk Management , 3rd Party Risk Management , Cyberwarfare / Nation-state attacks
DC Attorney General Alleges Violation of Consumer Protection Law(jeremy_kirk) • December 20, 2018 Facebook CEO Mark Zuckerberg at the F8 Developer Conference in San Jose, Calif., on May 1 (Photo: Facebook)
Facebook CEO Mark Zuckerberg at the F8 Developer Conference in San Jose, Calif., on May 1 (Photo: Facebook)Facebook violated consumer protection law by failing to protect personal data that consumers thought they'd locked down using the social networking site's confusing privacy controls, the District of Columbia alleges in a lawsuit filed on Wednesday.
See Also: Five Steps to Masterminding an Effective Security Awareness Program
The lawsuit, initiated by D.C. Attorney General Karl A. Racine, marks the first court action by a state attorney general against Facebook related to Cambridge Analytica, the now-defunct political consultancy that worked for Donald Trump's presidential campaign.
Cambridge Analytica received personal data for 87 million Facebook profiles in violation of the company's policies. Despite knowing of the situation, Facebook did not inform users until two years later, the lawsuit alleges.
A Facebook official reached in Sydney on Thursday says the company did not have an immediate comment on the lawsuit.
The district's lawsuit comes shortly after a bombshell report from The New York Times that Facebook had data-sharing agreements with a range of companies, including Netflix, Spotify, Microsoft, Yahoo, Apple and the Russian search engine Yandex.
The agreements allowed the companies to collect personal data without the direct consent of users, bypassing whatever privacy settings Facebook users had in place, the Times reports. The agreements helped grow Facebook's advertising revenue and boost its number of users.
Facebook's director of privacy and public policy, Steve Satterfield, disputed the Times' characterization of the data sharing, saying in a statement: "Facebook's partners don't get to ignore people's privacy settings, and it's wrong to suggest that they do."
Nonetheless, Satterfield went on to say that Facebook continues to wind down those kinds of integration partnerships.
"We know we've got work to do to regain people's trust. Protecting people's information requires stronger teams, better technology and clearer policies, and that's where we've been focused for most of 2018," he says.
Facebook: Promises Broken
The District of Columbia's lawsuit alleges that Cambridge Analytica is just one of many examples of how Facebook claimed consumers could lock down their data, but nonetheless shared it data anyway without consent.
"Facebook's consumers reasonably expect that Facebook will take appropriate steps to maintain and protect their data," the lawsuit says. "Facebook tells them as much, promising that it requires applications to respect a Facebook consumer's privacy. Facebook has failed to live up to this commitment."
The lawsuit alleges Facebook violated the district's Consumer Protection Procedures Act, which gives consumers the right to truthful information about consumer goods and services.
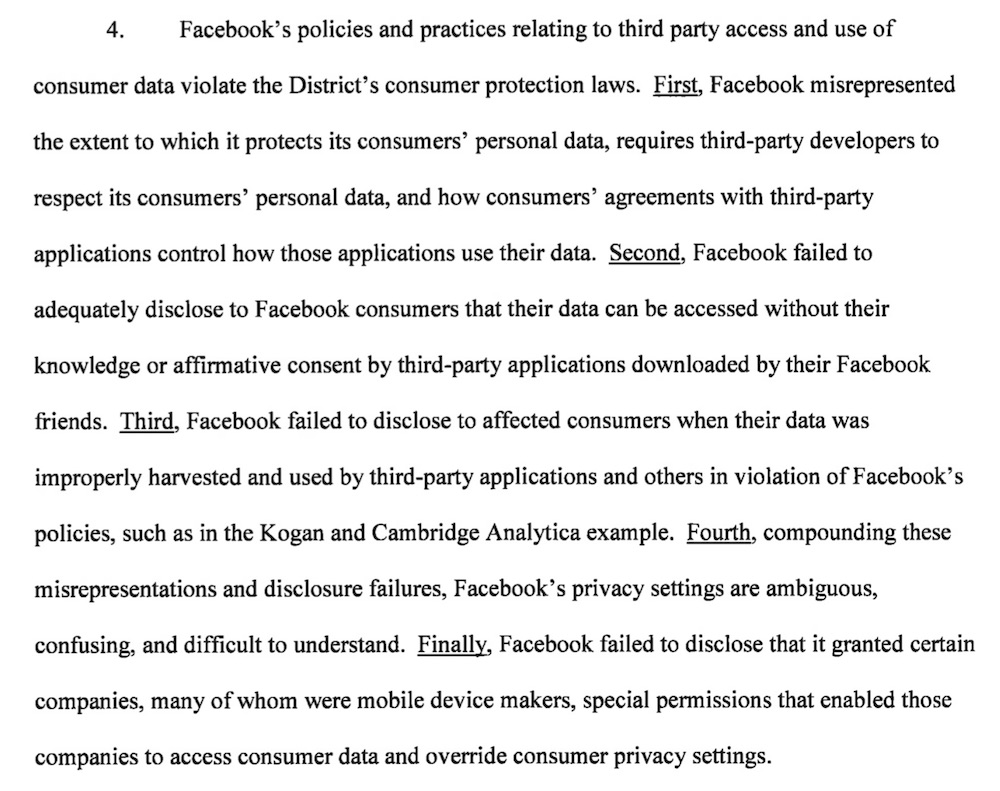 Five key points within the lawsuit filed by the District of Columbia's attorney general against Facebook
Five key points within the lawsuit filed by the District of Columbia's attorney general against FacebookBecause the U.S. lacks a federal privacy law, questionable practices that have arisen in the age of aggressive data trading have been dealt with under consumer protection laws that generally forbid deceptive practices. The Federal Trade Commission handles those enforcement actions.
The FTC opened an investigation into Cambridge Analytica in March, but the agency has yet to announce an enforcement action or settlement.
In October, the U.K.'s Information Commissioner's Office fined Facebook £500,000 ($645,000) for violating rules on processing personal data related to Cambridge Analytica. Facebook is appealing the fine, which is the maximum that the ICO can levy (see: Facebook Slammed With Maximum UK Privacy Fine).
On Monday, Ireland's data protection watchdog opened an investigation into two Facebook breaches. One involved the exposure of private photos to app developers, and the other a hacking incident that exposed 50 million accounts (see: Ireland's Privacy Watchdog Probes Facebook Data Breaches and Facebook Breach: Attackers Exploited Privacy Feature.
FTC Investigated Facebook Before
In theory, the Cambridge Analytica scandal and the sharing of personal data without consent with other companies shouldn't have happened because of a previous settlement with the FTC.
In 2011, Facebook reached an agreement with the FTC after the agency filed a complaint that alleged the company deceived consumers through a range of dodgy data-sharing practices. That included allowing third-party apps to have access to far more data than needed to operate.
Also, the FTC alleged that despite if consumers set a privacy control to share data with "Friends Only," third-party apps could still collect their data if a person's friend used a particular app. As of 2011, that practice of apps reaching into friends of friends data should have stopped.
But that continued ability is what amplified the Cambridge Analytica situation. About 270,000 people took the personality quiz, called "thisisyourdigitallife," which was developed by a Cambridge University psychology researcher Aleksandr Kogan. It was deployed for at least two to three months on Facebook in 2014 (see: Facebook and Cambridge Analytica: Data Scandal Intensifies).
But because of Facebook's policies at the time, the app was allowed to collect friends of friends' data, seemingly in violation of the FTC consent decree. The personality quiz scooped up data for 87 million people worldwide. The D.C. lawsuit alleges that Kogan subsequently sold the data to Cambridge Analytica for $800,000, although Kogan has denied that he personally profited.
The lawsuit further says that Facebook's failure to disclose to consumers that their data was improperly harvested is an omission of fact that "tended to mislead consumers and are unfair and deceptive trade practices."
As part of the FTC settlement, Facebook was required to obtain a third-party audit every two years for 20 years. It's unclear why the audits did not highlight the data-sharing practices.
Facebook Disputes Report
The Times report shows that Facebook's data-sharing with third parties was on a much larger and intentional scale, a revelation that is likely to prompt scrutiny from data protection regulators worldwide and more lawsuits.
The Times obtained hundreds of page of internal records from a system that Facebook used to track partnerships. The records show that Facebook continued to share personal data with third parties despite claiming it tightened its controls after it discovered the Cambridge Analytica situation in early 2015.
— Steve Satterfield, Facebook
Microsoft's Bing search engine, for example, had unfettered access to the names of all Facebook users without consent, the Times reports. Netflix, Spotify and the Royal Bank of Canada were allowed full access to users' private messages, apparently to share content using Facebook's Messenger, according to the Times. Facebook addressed this kind of access in a blog post on Thursday, saying the capabilities were made clear to users when they logged into those services using Facebook's Login feature.
Amazon could obtain user names and contact information for friends of friends, and Apple could see contact numbers and calendar entries of people even if the account settings disabled sharing, the Times reports.
Konstantinos Papamiltiadis, Facebook's director of developer platforms and programs, explained in a blog post on Tuesday that the program, known as instant personalization, ran from 2010 through 2014. It was intended to make Facebook features available within other apps when use of Facebook on mobile wasn't as widespread.
Papamiltiadis says that Facebook, however, didn't deactivate the APIs for instant personalization until last year, which was a mistake. Nearly all of the partnerships have now been shut down over the past several months, with the exception of ones with Amazon and Apple. He maintained that users authorized the access to the integration partners because they used their Facebook account to log in to the services.
Satterfield, Facebook's director of public policy, says that partners were "unable to use information for independent purposes." Facebook told the Times that none of the companies have abused the data and that its privacy policy circa 2010 stated that it shared data.
Still, Satterfield repeated what founder Mark Zuckerberg and Chief Operating Officer Sheryl Sandberg have acknowledged throughout this year as Facebook endured a backlash.
"We know we've got work to do to regain people's trust," Satterfield says. "Protecting people's information requires stronger teams, better technology and clearer policies, and that's where we've been focused for most of 2018."
US coffee store chain Caribou Coffee announced a security breach today after it discovered unauthorized access of its point of sale (POS) systems.
The company listed 239 stores of its total 603 locations as impacted, which roughly amounts to 40 percent of all its sites.
All customers who used a credit or debit card at one of the affected stores between August 28, 2018, and December 3, 2018, should consider their card details compromised and take precautions such as asking for a card replacement, reviewing credit card reports, and enrolling in identity protection programs.
Users can consult the list of impacted stores via the company's data breach notice, posted on its homepage.
Caribou Coffee officials said they detected that something was wrong last month, on November 28, when its IT staff was alerted of "unusual activity" on its network via its security monitoring processes.
The company said it worked with experts from Mandiant, a cyber-security firm specialized in investigating data breaches. Two days later, Mandiant informed Caribou Coffee that it discovered unauthorized access of the company's POS system that also exposed some of the coffee store's customer data.
Caribou Coffee said that names, card numbers, expiration dates, and card security codes might have been exposed and collected by intruders.
Card payments made through the company's website were not affected, as this payment system is separate from in-store POS systems.
"At this time, we are confident that the breach has been contained," said Caribou Coffee officials. "We also are in regular communication with the credit card companies and will provide them with the information necessary to notify the banks that may have issued the affected payment cards."
The FBI is also on the case.
More data breach coverage:
Updated No flights have arrived or left London's Gatwick Airport since just before 21:00 UTC last night after drones were apparently spotted over the airspace.
Chris Woodroofe, Gatwick's chief operating officer, told the BBC's Today programme [from 1:09.39] on Radio 4 this morning that 20 police units from two forces were hunting down the drone operator as "that is the way to disable the drone". He added: "We also have the helicopter up in the air."
Woodroofe said that "two drones" had been spotted by staff the night before. "They were over [the runway]... over the perimeter fence and into where the runway operates from..."
The COO confirmed that another drone sighting had been made just minutes before he began speaking to host John Humphrys. At around 07:12 UTC, he said: "In the last five minutes we saw drones back over the perimeter fence in our runway and taxiway area"...
Answering the question on everyone's lips as they pulled imaginary triggers at the air while scoffing, he told Today that police had advised that "it would be dangerous to seek to shoot the drone down because of what may happen to the stray bullets".
Reg reporter Richard Speed, literally our man on the ground, is one of the 2,000 people whose flights have been unable to take off. He told El Reg's London HQ: "For some reason, only the robot voice is allowed to use the tannoy, [which] means airline staff are having to yell updates from the info desks.
"Flight crew and cabin crew are also milling about. 'We know as much as you do – no one is telling us anything'."
"Anything scheduled after 8am is now cancelled. If I was a drone hobbyist I would be seriously worried about [the] kneejerk reaction."
Air traffic control organisation Eurocontrol said Gatwick – UK's second biggest airport – would be closed until 12:00 UTC, in an update issued at 09:06 UTC.
The runway was closed on 21:00 on Wednesday night – trapping thousands of people in the terminals awaiting direct and connecting flights in the runup to the Christmas break.
The airfield was opened briefly at 03:01 but was sealed off about 44 minutes later due to a "further sighting of drones".
The airport said in a tweet an hour ago that it was working with the Sussex* police and wouldn't reopen the runway until it had "suitable reassurance" it was safe to do so.
Angry travellers took to the microblogging platform to complain. Tinkerbell81 opined: "You seriously expect us to believe that 'drone activity' shuts an airport down for nearly 12 hours ........ it was raining hard most of the night! Finding the 'operator' would be a needle in a haystack..."
Although "Jaeyeon Park", who asked the location of the gate for a British Airways flight, must have been relieved to have been told:
Said our man on the scene: "I'd have an airport beer, but the queue for Wetherspoons is epic." ®
* In the tradition of London airports (other than the marvellous London city, in East London's Docklands), Gatwick is in one of the home counties surrounding Greater London – in LGW's case, Sussex.
Passengers are being sent to their gates. But El Reg has noticed Air traffic control organisation Eurocontrol pushing back reopening times to 1300.
Sussex police has called the drone disruption a "deliberate act" but said "There are no indications to suggest this is terror-related". It has asked anyone who can help identify the operators to ring 999.
Passengers have been turned back from the gates again, Reg man Richard Speed told us.
At 11:20 UTC Eurocontrol extended the closure until 14:00 UK time, but just 20 minutes later, it sent out an update saying the closure would remain in place until 16:00 UTC.
Gatwick, meanwhile, confirmed at 11:54 UTC that "ongoing drone activity around the airfield" has kept all flights suspended from Gatwick. It said the "significant disruption" was the result of "what appears to be a deliberate attempt to disrupt flights".
Sussex cops have assured the public that the drone pic it used in a previous tweet – a Shutterstock image of a drone quadcopter with digital camera - was "not [one of] the devices being sought". It added: "It is believed that the Gatwick devices used are of an industrial specification. We are continuing to search for the operators."
The Reg has deduced this is to allay any concerns that the devices were military. We have contacted the cops asking for clarification.
16:00 UTC has come and gone and Gatwick airfield is still closed. Sussex cops have reportedly requested help from the Army.
Flights have now been suspended for over 19 hours.



