Blockchain & Cryptocurrency
,
Cybercrime
,
Fraud Management & Cybercrime
Prosecutors in Japan Seek 10-Year Embezzlement Sentence for Mark Karpeles(
euroinfosec) •
December 28, 2018

Mark Karpeles, the head of the former Mt. Gox bitcoin exchange in Tokyo, has continued to maintain his innocence during the closing arguments in an embezzlement trial against him, Japanese broadcaster NHK reports.
See Also: Cybercrime 2.0: A New Era for the Identity and Authentication Challenge
Karpeles, a 33-year-old French national, has been under investigation in Japan after the Mt. Gox cryptocurrency exchange, of which he was CEO, went bust in 2014.
Karpeles has blamed a hack attack for the loss of 850,000 bitcoins, then worth about $500 million, as well as $28 million in cash that was stolen from the company's bank accounts. After halting trading in February 2014, Mt. Gox - then the world's largest cryptocurrency exchange - declared bankruptcy, blaming the missing bitcoins.
Subsequently, Karpeles said that he'd recovered 200,000 bitcoins from a cold wallet, meaning a storage device disconnected from the internet (see Bitcoin Trading Website Goes Dark).
Separate to the hack attack, however, Japanese authorities have accused Karpeles of embezzling 340 million yen ($3.1 million), tampering with Mt. Gox systems to inflate account balances and failing to honor users' requests for their missing funds to be returned.
In July 2017, a trial against Karpeles began in Tokyo District Court. "I swear to God I am not guilty," Karpeles told the court in a statement he read in Japanese on the first day of his trial, The Japan Times reported.
On Thursday, the trial concluded, with the former CEO continuing to maintain his innocence, denying all of the charges leveled against him. He has also apologized for having failed to prevent the hack attack.
Prosecutors are seeking a 10-year prison sentence for Karpeles. They argued in court that his alleged acts "were extremely vicious, as they completely undermined confidence in trading," NHK has reported.
The court is set to issue its verdict on the case on March 15, 2019.
As a result of the Mt. Gox meltdown, Japan became one of the first countries to regulate cryptocurrency exchanges at a national level to better protect investors.
Embezzlement Charges
Karpeles was first arrested in August 2015 on charges that he'd stolen funds from exchange users from 2011 to 2013 and moved the funds to his own accounts.
Later that year, Karpeles was rearrested and charged with embezzlement. Prosecutors accused him of transferring about $3.1 million in users' cryptocurrency to accounts that he controlled, between September and December 2013. They also accused him of using embezzled funds to invest in a software development startup, purchase luxury goods as well as hire prostitutes, cryptocurrency news site CCN has reported.
Karpeles, however, said the transferred money was a loan, although later said it was profits generated by his cryptocurrency exchange.
Karpeles was released on bail on the condition that he not leave Japan, Coindesk reported.
In June 2017, a Tokyo court halted the Mt. Gox bankruptcy proceedings and ordered that civil rehabilitation proceedings begin, which would allow the company's existing management team to draft a court-led reconstruction plan.
Earlier this year, Karpeles became the CTO for London Trust Media, a VPN service provider.
Hack Attack
Separate to the embezzlement charges, more details about how Mt. Gox appeared to have been hacked have emerged.
Police in Greece last year arrested Russian national Alexander Vinnik for allegedly running a massive money laundering operation that processed $4 billion in bitcoins, some of which were apparently stolen from Mt. Gox.
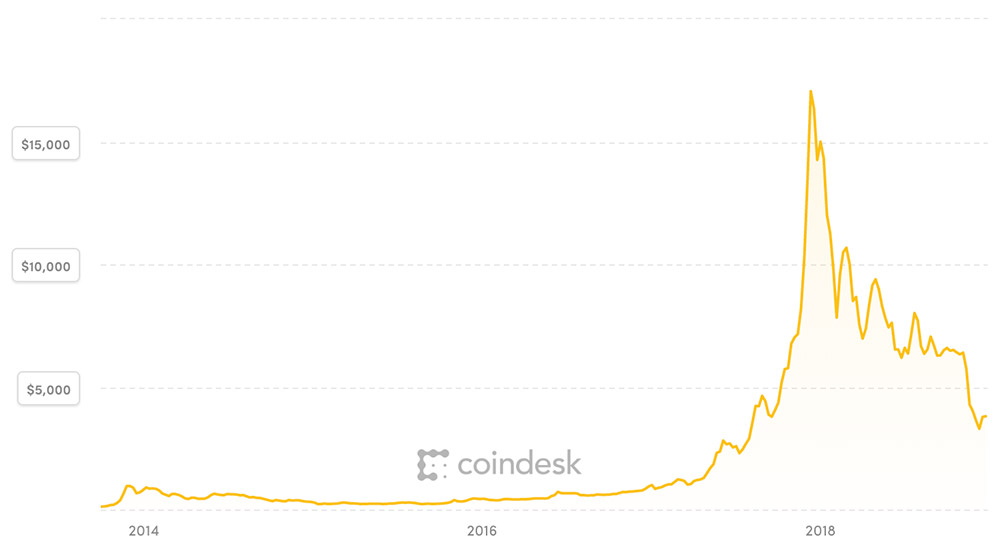
The value of a bitcoin on Dec. 28, 2018, was about $3,600, far above its value of about $590 when Mt. Gox went bust in 2014, but still below its all-time high of nearly $20,000 in December 2017. (Source:
Coindesk)
The U.S. Department of Justice has accused Vinnik of operating the BTC-e cryptocurrency exchange as an unlicensed money service business that was used to launder funds for numerous cybercriminal enterprises (see Feds Indict Russian Over BTC-e Bitcoin Exchange).
At the time of his arrest in Greece, Vinnik was the "chief suspect for involvement in the Mt. Gox theft - or the laundering of the proceeds thereof," according to a Tokyo-based group of bitcoin security researchers who call themselves WizSec.
Karpeles blamed Mt. Gox's bitcoin loss on a security issue called transaction malleability.
But WizSec says that Mt. Gox's security troubles appear to have begun in September 2011, when "the Mt. Gox hot wallet private keys were stolen," and Vinnik allegedly began using the keys to transfer bitcoins from customers' wallets to wallets that he controlled.
WizSec says that the wallet abuse confused Mt. Gox's system "into mistakenly interpreting some of the thief's spending as deposits," thus leading to erroneous credits to some users' accounts.
The researchers accused Vinnik of ultimately handling - if not having taken them outright - about 670,000 bitcoins stolen from Mt. Gox.
WizSec says it traced 300,000 of the stolen Mt. Gox bitcoins to BTC-e, where they were "presumably sold off or laundered." It said that other stolen bitcoins were laundered via other exchanges, in some cases even via Mt. Gox.




 The value of a bitcoin on Dec. 28, 2018, was about $3,600, far above its value of about $590 when Mt. Gox went bust in 2014, but still below its all-time high of nearly $20,000 in December 2017. (Source:
The value of a bitcoin on Dec. 28, 2018, was about $3,600, far above its value of about $590 when Mt. Gox went bust in 2014, but still below its all-time high of nearly $20,000 in December 2017. (Source:  South and North Korea complete field verification of the withdrawal of guard posts from within their demilitarized zone on Dec. 12, 2018. (Source: South Korea's Ministry of National Defense)
South and North Korea complete field verification of the withdrawal of guard posts from within their demilitarized zone on Dec. 12, 2018. (Source: South Korea's Ministry of National Defense) The headquarter of South Korea's Ministry of Unification in Seoul. (Source:
The headquarter of South Korea's Ministry of Unification in Seoul. (Source:  Photo:
Photo: 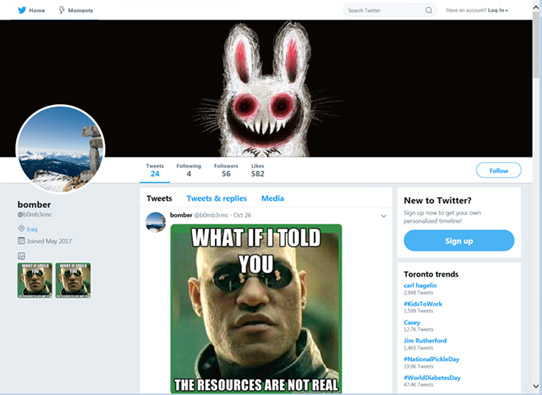 Trend Micro recently discovered that Twitter memes were being used to remotely control PCs infected with Berbomthum malware. (Source:
Trend Micro recently discovered that Twitter memes were being used to remotely control PCs infected with Berbomthum malware. (Source:  Dominic Schaub's brief history of steganography. (Source:
Dominic Schaub's brief history of steganography. (Source: 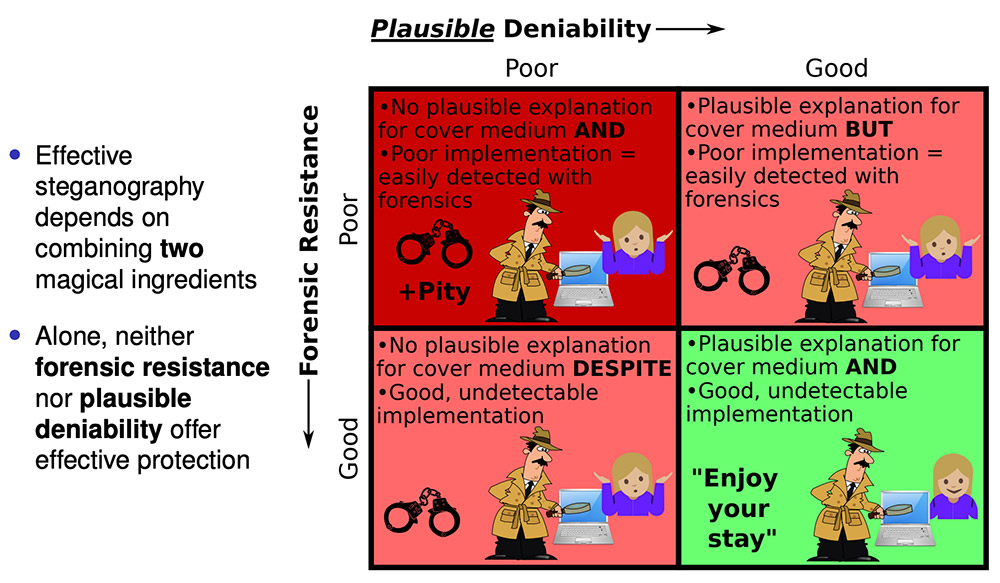 Effective steganography requires plausible deniability and forensic resistance, says Dominic Schaub. (Source:
Effective steganography requires plausible deniability and forensic resistance, says Dominic Schaub. (Source:  Rebecca Herold of the Privacy Professor and Simbus
Rebecca Herold of the Privacy Professor and Simbus