Cybersecurity , Data Breach , Risk Management
State-of-the-Hack: The Top 10 Security PredictionsSecurity News
 Chris Pierson, CISO, Viewpost
Chris Pierson, CISO, ViewpostAs a result of high-profile breaches, emerging malware threats and heightened regulatory scrutiny, CISOs at financial institutions are under more pressure than ever to develop innovative strategies for enhancing cybersecurity.
See Also: How to Measure & Communicate Return on Cybersecurity Investments
And the evolving role of the CISO will be a hot topic at RSA Conference 2016, Feb. 29 through March 4 in San Francisco.
Cybersecurity attorney Chris Pierson, who serves as chief security officer for invoicing and payments provider Viewpost, will explore this topic with co-presenter Terry Ragsdale, CFO at financing services firm LSQ Funding Group, on March 1 during a 3:30 p.m. session: Partnerships with a CFO: On the Front Line of Cybersecurity .
Pierson and Ragsdale will discuss why partnerships between CISOs and CFOs make sense, and why CISOs need to break themselves free of the budgetary constraints placed upon them by CIOs. It should be a lively discussion.
"What is needed is a separate risk voice, a separate security voice," Pierson told me during a recent interview. "There will be increased collaboration with the chief financial officer and the other financial folks at the company. What you'll have are ... lawyers, technology professionals, security professionals and finance professionals all at the same table and on equal footing with equal budget to support the needs that they have."
This year's RSA Conference has many other sessions aimed at exploring the CISO's evolving role, including:
From Cave Man to Business Man, the Evolution of the CISO to CIRO (Feb. 29, 3 p.m.): Third-party risk expert James Christiansen of cybersecurity firm Optiv will review how successful IT security leaders are using their skills to effectively communicate cybersecurity risks to the board and executive team to ensure greater cybersecurity budgetary success. CISO Success Strategies: On Becoming a Security Business Leader (March 2, 9:10 a.m.): SANS Institute CISO Frank Kim will walk us through why cybersecurity is a vital component of business growth. Habits of an Effective CISO (March 3, 8 a.m.): During this panel discussion, four CISOs, Ben Rothke, Jack Jones, Phil Agcaoili and Roland Cloutier, will review key steps that help them manage new cybersecurity and management responsibilities.In addition to CISO-focused sessions, other sessions of particular interest to the financial community include.
Be sure to frequently check our RSA Conference 2016 news site for the latest video interviews, podcasts, blogs and news items from the biggest information security event of the year.

The RSA Conference 2016 in San Francisco has drawn advance buzz from some quarters - and outright scorn from others - over its decision to run a panel that features the creator and two cast members of the hit TV show "CSI: Cyber" (see Real Hackers Wield Social Engineering).
See Also: Cyber Insurance and Cyber Security
But what will arguably make this year's conference even more interesting, compelling and relevant are recent real-world news events, including the crypto court battle now unfolding between Apple and the FBI (see Apple vs. FBI: Readers Debate).
8 Hot Sessions
Looking beyond all of that drama, here are my picks for some top sessions:
The Cryptographers' Panel (March 1, 9:50 a.m.): Cryptography heavyweights Whitfield Diffie, Ronald Rivest, Adi Shamir and Moxie Marlinspike discuss the latest encryption trends. Malware as a Service: Kill the Supply Chain (March 2, 10:20 a.m.): Leading information security experts - including Johannes Ullrich and Lance James - outline strategies for shuttering malware rings. Habits of an Effective CISO (March 3, 8:00 a.m.): Hear four CISOs share their secrets. Data Breach Litigation: How to Avoid It and Be Better Prepared for Defense (March 3, 11:30 a.m.): CISO Andrea Hoy and attorney Ronald Raether offer advice. Opportunities and Challenges to Securing the Internet of Things (March 3, 8 a.m.): The U.S. Department of Homeland Security's Suzanne Spaulding joins experts from Symantec and PKWARE to discuss consumer and commercial IoT devices and address the question of what it will take to make them secure. Confronting Cybercrime: Exploring the Legal and Investigative Challenges Bridging Cybercrime and Cybersecurity - How Law Enforcement Battles Cyberthreats (March 3, 11:30 a.m.): Panelists from the Department of Justice, FBI and U.S. Secret Service talk offense, defense and partnerships. Beyond Encryption: Why We Can't Come Together on Security and Privacy - and the Catastrophes That Await If We Don't (March 3, 2:50 p.m.): Security and privacy heavyweights - including former RSA chief Art Coviello, Center for Democracy & Technology head Nuala O'Connor, and Trevor Hughes, who heads the International Association of Privacy Professionals, debate privacy and security.Going Out With Sean Penn
As in years past, the conference has also turned to a "closer" who hails from outside the security realm. This time, it's actor and director Sean Penn, who last month made headlines after secretly interviewing drug kingpin Joaquín Archivaldo Guzmán Loera, a.k.a. El Chapo, in October 2015, on behalf of Rolling Stone.
It's not clear if Penn's interview ultimately led to Guzman's arrest. But you can be sure it's a question Penn will get asked.
Breach Preparedness , Data Breach , Risk Management
Could Failure to Embrace 20 Critical Controls Pose Legal Threat to Enterprises? California Attorney General Kamala Harris
California Attorney General Kamala HarrisA new report from California's attorney general says failure to implement the 20 critical security controls that define a minimum level of information security constitutes a lack of "reasonable security."
See Also: Proactive Malware Hunting
So, could failure to adopt these or similar controls pose a legal threat to organizations? Perhaps, under certain circumstances.
"The attorney general issuing guidance, by itself, doesn't set a legally binding duty on a company, but it certainly is indicative of what the AG thinks, and would likely be cited by the AG in cases the AG brought regarding data security," says privacy and data security attorney Andrew Serwin of the law firm Morrison & Foerster.
The controls Harris cited were developed seven years ago as the Consensus Audit Guidelines by a consortium of public-private IT security experts under the auspices of the think tank Center for Strategic and International Studies and the SANS Institute. The 20 critical security controls - now managed by the not-for-profit Center for Internet Security - is a prioritized list of specific and actionable steps aimed to mitigate the most pervasive and dangerous cyberattacks (see Public/Private Group Creates Plan to Protect Critical Infrastructures).
Complying with the Law
Harris didn't explicitly say the recommendations in the report had the force of law, but she suggested that following them would be what the law encourages. "This report clearly articulates basic steps that businesses and organizations must take to comply with the law, reduce data breaches and better protect the public and our national security," Harris said in a statement issued with the report.
The report also recommends organizations adopt multifactor authentication on consumer-facing online accounts and use strong encryption on laptops and mobile devices to protect individual privacy, "a particular imperative for healthcare, which appears to be lagging behind other sectors in this regard."
The attorney general said many breaches reported to her office "could have been prevented by taking reasonable security measures, and an organization that voluntarily chooses to collect and retain personal information takes on a legal obligation to adopt appropriate security controls."
California's Influence on InfoSec
What California does regarding enforcing data privacy and online privacy laws matters beyond its borders. As the nation's most populous state, many national businesses operate or are based there. California is a trend leader in IT security law; in 2002, it became the first state to enact a data breach notification law.
"California has been the state to watch, and many other states have taken lessons from California's pronouncements and issuances and have mimicked those pronouncements," says privacy and cybersecurity lawyer Lisa Sotto of the law firm Hunton & Williams. "It's absolutely a state that is ahead of the curve on data privacy and data security issues. We have to sit up and take notice when the California AG makes this sort of a statement."
Lawyer Lisa Sotto explains why the California attorney general's pronouncement on the 20 security controls is significant.Sotto characterizes Harris' pronouncement as warranting significant attention. "We now understand where she thinks the bar is set, and she, presumably, will be initiating investigations against companies that fall below that bar," Sotto says.
The California AG's report points out that the legal obligation to secure information is contained in an expanding set of laws, regulations, enforcement actions, common law duties, contracts and self-regulatory regimes. California has an information security statute that requires all businesses that collect personal information on California residents to use "reasonable security procedures and practices appropriate to the nature of the information, to protect the personal information from unauthorized access, destruction use, modification or disclosure."
Detecting Breaches Rapidly
A review of 658 data breaches over the past four years by the California attorney general suggests that many could have been prevented or at least detected and corrected more rapidly had the basic security measures in the controls been implemented.
Harris and other legal experts are not saying that organizations must adopt the 20 critical security controls. Yet, not doing so could be deemed as failing to take proper steps to safeguard protected personal information when determining damages in a lawsuit in the eyes of jurors and judges after reviewing expert testimony. After all, in determining damages, a court could hold an organization liable if it does not follow standard industry practices.
"What one expert would say is reasonable isn't always agreed upon, and can also depend upon the sensitivity of the information, the damage to consumers, if any, and other factors," Serwin says.
In 2015 alone, 84 million new pieces of malware were created. How can organizations hope to keep pace with the new strains and tactics? Through advanced endpoint protection, says John Peterson of Comodo.
To put things in perspective, the amount of new malware created last year equals about 27 percent of the malware ever created, says Peterson, Comodo's vice president of enterprise product management and product marketing.
"There's not only more new malware, but there are more strains of malware," Peterson says. "It's gotten so bad that the rate of malware creation is just really hard to keep up with."
Traditional blacklisting cannot keep pace with the evolution of malware, but whitelisting, sandboxing and machine learning all have their challenges as well, Peterson says.
The problem in the marketplace, he adds, is that many security vendors offer point solutions - but not suites that incorporate all of the different antimalware tools.
"All of these solutions are actually good at what they do, but they're not enough to cover the problem," Peterson says. "The challenge is: Trying to do too much of a point solution leaves an area of exposure for malware to come in because you're not addressing the whole [problem]."
In an interview about advanced endpoint protection, Peterson discusses:
The state of malware today; Why many modern security solutions still struggle to succeed; The principles behind Comodo's "default deny" and containment strategies.With a deep history and career in cybersecurity, Peterson is responsible for shaping the enterprise product roadmap for the company, along with the execution of the company's product marketing strategy
Peterson works across the leadership, engineering, sales and marketing teams within Comodo to integrate the product strategy and ensure the success of all enterprise product lines in the market.
Before joining Comodo in November of 2015, he led Sales Engineering efforts at Zscaler, managing a team focused on Internet security delivered through the cloud. Over his 25 year career in B2B and cybersecurity engineering, he has held engineering and leadership positions at Barracuda Networks, Juniper Networks, Websense, Montego Networks, Cisco Systems, 3Com and Fortinet.
Encryption , Privacy , Technology
Magistrate in New York Says U.S. Can't Compel Apple to Retrieve Data from Device
A federal magistrate in Brooklyn, N.Y., unlike another judge in California, has denied a request by federal authorities to force Apple to retrieve data from an iPhone, this time in a New York narcotics case.
See Also: Cyber Insurance and Cyber Security
Magistrate Judge James Orenstein on Monday said the government cannot compel Apple to help law enforcement bypass a locked screen on an iPhone seized by prosecutors.
In the California case, involving the iPhone of one of the San Bernardino shooters who killed 14 people, U.S. Magistrate Sheri Pym approved a Justice Department order citing an 1789 law known as the All Writs Act to require Apple to help the FBI crack open the phone (see Apple, FBI Draw Lines in Crypto Battle). Government lawyers contend the All Writs Act allows courts to require actions to comply with their orders when not covered by existing law. Apple is fighting the California order.
But Orenstein, in the New York case, said the government's interpretation of the All Writs Act is too broad. To apply the All Writs Act, Orenstein wrote, the government would need to show that Apple had a close relationship to underlying criminal conduct of the suspect named Jun Feng of Queens, N.Y., and government investigators. In addition, Orenstein said to apply the 18th century law, he must consider the burden such a request would impose on Apple as well as the necessity of inflicting the burden on the iPhone maker.
Kind of Corporation Apple Aspires to Be
In a footnote, Orenstein wrote that in considering the burden, "it is entirely appropriate to take into account the extent to which the compromise of privacy and data security that Apple promises its customers affects not only its financial bottom line, but also its decisions about the kind of corporation it aspires to be.
"The fact that the government or a judge might disapprove Apple's preference to safeguard data security and customer privacy over the stated needs of a law enforcement agency is of no moment: in the absence of any other legal constraint, that choice is Apple's to make, and I must take into account the fact that an order compelling Apple to abandon that choice would impose a cognizable burden on the corporation that is wholly distinct from any direct or indirect financial cost of compliance."
Orenstein ruled the government failed to justify imposing on Apple "the obligation to assist the government's investigation against its will. I, therefore, deny the motion."
Order Extolled
Civil liberties groups quickly praised Orenstein's order.
"Orenstein argues persuasively that Apple's decisions to implement robust security features in iOS must be viewed against the backdrop of congressional inaction," Electronic Frontier Foundation staff attorney Andrew Crocker and copyright activism director Parker Higgins write in a blog. "Under current law, Apple's choice to design its software this way is entirely legal; indeed some members of Congress have introduced legislation to protect the right to uncompromised encryption."
The Justice Department expressed disappointment with Orenstein's order and said it would appeal, according to published reports. "This phone may contain evidence that will assist us in an active criminal investigation, and we will continue to use the judicial system in our attempt to obtain it," a Justice Department statement says.
The U.S. federal government designed Einstein, the Department of Homeland Security's intrusion detection and prevention system, to use signatures - or patterns of malicious data - to identify cyber incursions. However, Einstein cannot detect intrusions employing methods such as analyzing anomalous behaviors in an IT system.
But DHS is working on new ways to detect intrusions that would either be incorporated into Einstein or operate separately as a complementary system. One area is malware provenance, the art and science of attributing elements of one object to another, similar to genetics. Simply, malware provenance examines malicious code to identify attributes that could be shared by other malware.
A team of IT security experts at DHS will host a session March 3 at the RSA Conference 2016 in San Francisco titled Understanding Malware Provenance: A Federal View, moderated by Peter Fonash, DHS chief technology officer for cybersecurity and communications, and including Phyllis Schneck, DHS deputy undersecretary for cybersecurity.
In an audio report (click player beneath image to listen):
Schneck compares malware provenance to genetic drug therapy as an approach to battle a cyber virus. She has been a longtime advocate of developing information security systems that mimic the human immune system (see Spotting Abnormal Behavior Automatically Without Need for Signatures). Gregory Wilshusen, the Government Accountability Office information security issues director, discusses the weaknesses in Einstein. Hear about a pilot conducted at the U.S. Air Force Academy's Center for Innovation that rapidly detected previously unidentified relationships between families of malware by employing malware provenance.Before becoming DHS deputy undersecretary for cybersecurity in 2013, Schneck served as chief technology officer for the public sector for McAfee, now part of Intel security, as well as the company's vice president of threat intelligence. She has a strong academic and research background, having earned a Ph.D. in computer science from Georgia Tech. Schneck holds three patents in high-performance and adaptive information security and has six research publications in the areas of information security, real-time systems, telecom and software engineering.
As a director at GAO, Wilshusen leads cybersecurity and privacy-related studies and audits of the federal government and critical infrastructure. He has more than 30 years of auditing, financial management and information systems experience. Prior to joining GAO in 1997, Wilshusen held a variety of public- and private-sector positions. He was a senior systems analyst at the Department of Education, controller for the North Carolina Department of Environment, Health and Natural Resources and held several senior auditing positions at Irving Burton Associates and the U.S. Army Audit Agency.
Cybersecurity , Risk Management , Technology
Hack My Ride Electric Cars Join the Internet of Unsecured Things
To the list of vulnerable, Internet-connected devices, now add the world's most popular electric car: the Nissan LEAF, of which 200,000 have now been sold (see The Internet of Dangerous Toys?).
See Also: Stop Fraud, Not Customers: Focus On Good User Experience
Australian information security expert Troy Hunt announced in a Feb. 24 blog post that a month prior, after teaching a development-focused "Hack Yourself First" course in Norway, one of the seminar participants decided to take a close look at the Nissan LEAF, including a smartphone app that owners can use to remotely control aspects of their car, such as turning the heater on in the morning before they get in - no doubt a popular feature in Scandinavia.
What he and British security researcher Scott Helme found won't shock anyone who's been following information security for any length of time: He could control many features - including adjusting the climate controls and accessing trip details - in any LEAF, anywhere in the world, simply by knowing or guessing any LEAF vehicle's VIN number.
Security researchers Troy Hunt and Scott Helme demonstrate remotely hacking Nissan LEAF car features.All VIN numbers in the world have 17 digits, but the first 12 digits are the same for all LEAF vehicles, leaving just five digits - and thus 100,000 potential combinations - for would-be car hackers to brute-force guess.
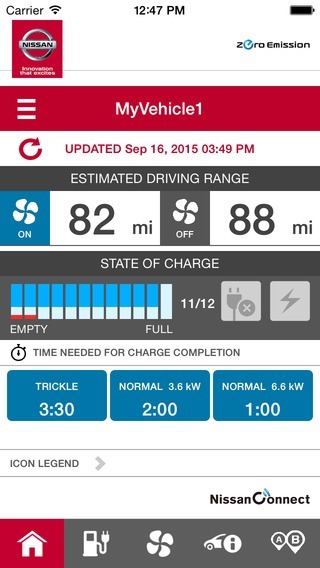 Nissan's app enables remote access to car environmental controls, trip data.
Nissan's app enables remote access to car environmental controls, trip data.Hunt says he reported the vulnerabilities directly - and privately - to Nissan on Jan. 23. But he decided to make the research public because it was being discussed on a public forum by legions of irate French Canadians, and the details were easily available to any non-native speakers via Google Translate.
"Nissan needs to fix this," Hunt says in his blog post. "It's a different class of vulnerability to the Charlie Miller and Chris Valasek Jeep hacking shenanigans of last year, but in both good and bad ways" (see Car Hacking Spurs Automakers to Share Threat Information).
Hunt says the good news is that the car's driving controls can't be hacked. But the bad news is "that the ease of gaining access to vehicle controls in this fashion .... [is] profoundly trivial," and portends long-term problems for the Internet of Cars.
"As car manufacturers rush toward joining in on the 'Internet of Things' craze, security cannot be an afterthought nor something we're told they take seriously after realizing that they didn't take it seriously enough in the first place," he says. "Imagine getting it as wrong as Nissan has for something like Volvo's 'digital key' initiative where you unlock your car with your phone."
Nissan Disables Related APIs - Mostly
In response to Hunt's post, Nissan on Feb 25 temporarily blocked APIs connected to the online app, telling the BBC that "the NissanConnect EV app - formerly called CarWings - is currently unavailable." But it denies the information security vulnerabilities pose a safety issue.
I've received a public response from Nissan: pic.twitter.com/rn6975oQw6
But Hunt notes that the approach Nissan appears to have taken - disabling access to the vulnerable APIs used by its app - doesn't appear to have disabled the functions in all countries. In comments to his blog post, some LEAF owners in Canada on Feb. 25 reported that they were still able to hack their vehicles.


 This year is crucial as we expect the size, severity and complexity of cyber threats to continue to increase exponentially. Attacks will continue to evolve, forcing organizations to expand their focus and be flexible to withstand unexpected, high impact events. Some of the notable predictions include cyber criminals leveraging personally identifiable information (PII), trusted partner networks, hacktivism, ransomware for corporations, and many more.
Do you know the top 10 security predictions that may impact your growing organization this year?
Join Michael Sutton, CISO, Zscaler, Inc., for a comprehensive overview of what to expect in 2016, including:
The top 10 security predictions
How these key trends will impact your organization
Critical takeaways for a comprehensive security strategy
About Zscaler
Zscaler is revolutionizing Internet security with the industry's first Security as a Service platform. As the most innovative firm in the $35 billion security market, Zscaler is used by more than 5,000 leading organizations, including 50 of the Fortune 500. Zscaler ensures that more than 15 million users worldwide are protected against cyber attacks and data breaches while staying fully compliant with corporate and regulatory policies.
Zscaler is a Gartner Magic Quadrant leader for Secure Web Gateways and delivers a safe and productive Internet experience for every user, from any device and from any location -- 100% in the cloud. With its multi-tenant, distributed cloud security platform, Zscaler effectively moves security into the internet backbone, operating in more than 100 data centers around the world and enabling organizations to fully leverage the promise of cloud and mobile computing with unparalleled and uncompromising protection and performance. Zscaler delivers unified, carrier-grade internet security, next generation firewall, web security, sandboxing/advanced persistent threat (APT) protection, data loss prevention, SSL inspection, traffic shaping, policy management and threat intelligence -- all without the need for on-premise hardware, appliances or software. To learn more, visit us at
This year is crucial as we expect the size, severity and complexity of cyber threats to continue to increase exponentially. Attacks will continue to evolve, forcing organizations to expand their focus and be flexible to withstand unexpected, high impact events. Some of the notable predictions include cyber criminals leveraging personally identifiable information (PII), trusted partner networks, hacktivism, ransomware for corporations, and many more.
Do you know the top 10 security predictions that may impact your growing organization this year?
Join Michael Sutton, CISO, Zscaler, Inc., for a comprehensive overview of what to expect in 2016, including:
The top 10 security predictions
How these key trends will impact your organization
Critical takeaways for a comprehensive security strategy
About Zscaler
Zscaler is revolutionizing Internet security with the industry's first Security as a Service platform. As the most innovative firm in the $35 billion security market, Zscaler is used by more than 5,000 leading organizations, including 50 of the Fortune 500. Zscaler ensures that more than 15 million users worldwide are protected against cyber attacks and data breaches while staying fully compliant with corporate and regulatory policies.
Zscaler is a Gartner Magic Quadrant leader for Secure Web Gateways and delivers a safe and productive Internet experience for every user, from any device and from any location -- 100% in the cloud. With its multi-tenant, distributed cloud security platform, Zscaler effectively moves security into the internet backbone, operating in more than 100 data centers around the world and enabling organizations to fully leverage the promise of cloud and mobile computing with unparalleled and uncompromising protection and performance. Zscaler delivers unified, carrier-grade internet security, next generation firewall, web security, sandboxing/advanced persistent threat (APT) protection, data loss prevention, SSL inspection, traffic shaping, policy management and threat intelligence -- all without the need for on-premise hardware, appliances or software. To learn more, visit us at 







