Anti-Malware , Risk Management , Technology
Cyberattacks Are Hitting All Sectors, Including Government
Ransomware is such a serious cybersecurity concern that the Federal Bureau of Investigation has issued new guidance and yet another alert about the threat.
See Also: How to Illuminate Data Risk to Avoid Financial Shocks
In recent weeks, attacks involving ransomware, in which cybercriminals demand ransom to unlock data they've encrypted, have plagued the healthcare sector. And federal agencies reported 321 ransomware-related incidents in the second half of last year, according to a new report (see Ransomware Attacks Against Government Agencies Widespread).
The FBI offered new guidance about mitigating the risks of ransomware in a podcast last week. It noted that ransomware is evolving, increasingly targeting businesses rather than consumers. And it warned against paying ransoms.
In addition to the guidance, the FBI also issued an alert about a new type of ransomware known as MSIL/Samas, which encrypts entire networks, rather than data linked to one computer, according to Reuters.
The Baltimore Sun reports that actions taken by hackers in a March 28 cyberattack against MedStar Health are "almost identical" to actions associated with the MSIL/Samas ransomware.
But MedStar Health, a 10-hospital system serving Maryland and the Washington, D.C. area, has not yet confirmed that ransomware was involved in the cyberattack, which forced the healthcare provider to shut down many of its systems to avoid further spread of a virus.
Although most ransomware is still spread via phishing, newer ransomware families are much more damaging than earlier versions, says Oliver Tavakoli, chief technology officer at security firm Vectra Networks. "All early versions of ransomware (CryptoLocker, CryptoWall, Locky) encrypted files, both local and on network share, and left computers operational," he says. "The newer versions, like Petya, encrypt the file system structures and render an entire machine unusable."
Lack of Ransomware Awareness
Gartner analyst Avivah Litan laments that too many businesses "are not spending large amounts of resources on security and are not equipped to even understand these [ransomware] threats. These entities are not focused on fighting ransomware, so criminals' attack methods can easily stay ahead of their victims' ability to defend themselves."
And too many organizations are paying ransoms to extortionists, says cybersecurity attorney Chris Pierson, who also serves as CISO at electronic payments and invoicing provider Viewpost. "Whether due to speed, mission criticality or the lack of good backups and data proliferation, more companies are being forced to pay these days," he says.
For example, in February, Hollywood Presbyterian Medical Center paid a $17,000 ransom in bitcoins to unlock data encrypted by cyberattackers. Allen Stefanek, the hospital's president and CEO, noted that his organization decided to pay the ransom because obtaining the decryption key from the attackers was "the quickest and most efficient way to restore our systems and administrative functions."
A High-Profit Crime
The FBI, which has issued several alerts about ransomware, is concerned because so many businesses are paying ransoms to the hackers, says John Miller, director of the ThreatScape Cyber Crime division, a security consultancy run by iSIGHT Partners, a FireEye company. And the more companies are willing to pay, the more attractive ransomware attacks look to criminals, he adds.
"Ransomware does continue to draw in high profits for operators, and in many cases the damages it causes are highly publicized; both trends lead to growth in ransomware's user-base," Miller says. "Another trend which has exacerbated the ransomware issue is that the marketplace distribution models for various types of ransomware have become increasingly optimized."
The percentage of organizations that pay the ransom demanded by extortionists wielding ransomware has not likely changed over the last several months, despite the FBI's efforts to improve public awareness, says Vectra Networks' Tavakoli. "Given the sheer increase in volume of ransomware, it is pretty clear that more ransoms are being paid overall," he says. "And more ransom fuels more ransomware - both in funding the operations of existing purveyors of ransomware, as well as attracting more bad guys into the space."
Tom Kellermann, CEO of security firm Strategic Cyber Ventures, claims that between 60 and 70 percent of businesses targeted by a ransomware attack are paying their attackers to have files and systems unencrypted. "They are paying ransom in order to maintain business continuity," he says. "This is a terrible trend."
Who's Most Vulnerable?
Companies that don't have effective disaster recovery protocols in place, or those that have lax backup policies, are the most vulnerable to ransomware, says Nick Hyatt, senior consultant of enterprise incident management for the security firm Optiv.
"It is imperative that corporate IT departments take the threat of ransomware seriously, especially in the healthcare and financial sectors, and make serious movement toward protecting their users, networks and sensitive information," Hyatt says.
Real-time network monitoring solutions are helping some businesses better prevent ransomware infections, Hyatt says. "But, for the most part, the ransomware developers are one step ahead of the security industry," he adds.
And Kellermann says some endpoint security solutions can prove helpful in preventing malware infections. "But backing up drives daily and better URL filtering is tantamount to success in preventing an infection," he says.




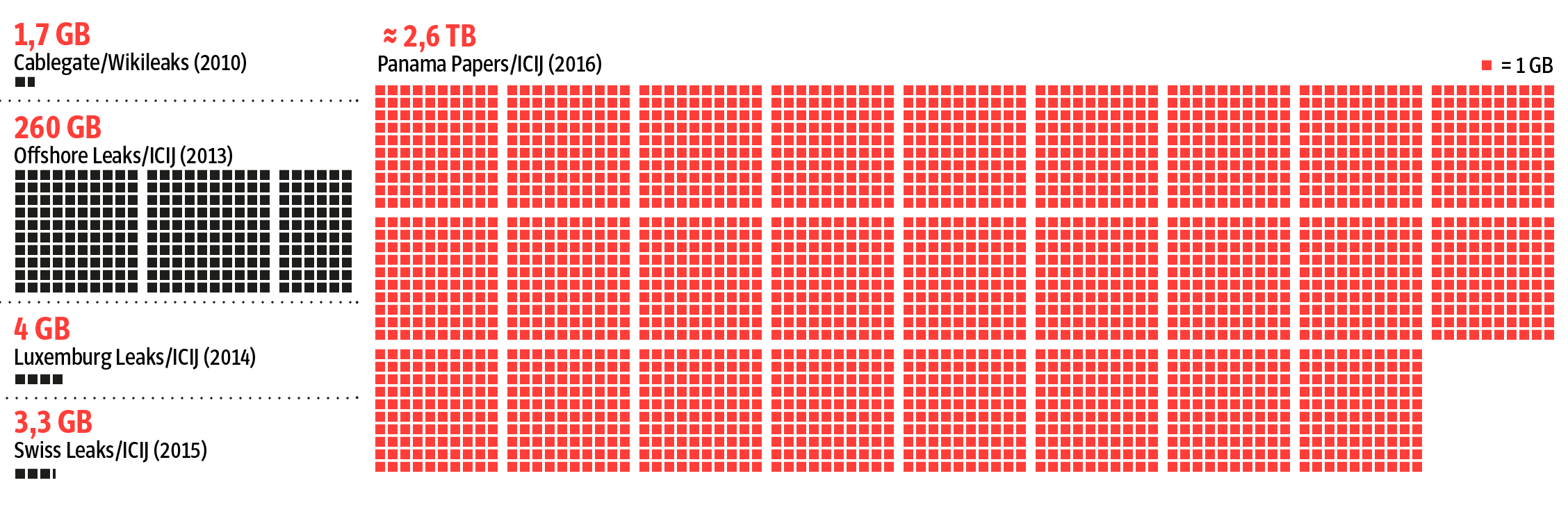 How the Panama Papers leak compares with previous leaks. Source: Süddeutsche Zeitung.
How the Panama Papers leak compares with previous leaks. Source: Süddeutsche Zeitung.