Breach Notification
,
Data Breach
Underground Rumors Hint at Other Nine-Figure Breaches
Jeremy Kirk (jeremy_kirk) •
June 1, 2016

MySpace on Tuesday confirmed it is resetting accounts affected by the release of 360 million usernames, email addresses and weakly hashed passwords. But according to one expert, there may be more huge data breaches to be announced, and a posting on an underground website points in that direction.
See Also: Detecting Insider Threats Through Machine Learning
Troy Hunt, who runs the breach notification service "Have I Been Pwned?," says there are rumors of "other things in the pipeline with nine figures."
"At the moment, there is a recurring pattern of very large breaches from a long time ago making an appearance," Hunt says.
Tied to LinkedIn, Tumblr Breaches?
May was a rough month for some major online services: 165 million leaked LinkedIn accounts, 65 million from Tumblr and 41 million from Fling, all from data breaches that occurred years ago.
The data from MySpace, LinkedIn, Tumblr and Fling are offered for sale on The Real Deal, an underground marketplace hosted on a Tor hidden service, which obscures its real IP address.
The seller goes by the nickname "peace_of_mind." It's a mystery if "Peace" is the actual hacker or simply a vendor for other parties who compromised the data. Either way, "there is something that has been a catalyst in his life that is causing him to liquidate," says Hunt, who loaded the MySpace breach data into his service on Tuesday night.
In its breach notification on Tuesday, MySpace took a bold leap, writing that "we believe the data breach is attributed to Russian cyberhacker 'Peace.' This same individual is responsible for other recent criminal attacks such as those on LinkedIn and Tumblr."
As of Wednesday morning, MySpace remains peace_of_mind's most expensive batch of data at 6 bitcoins, or around $3,180. The LinkedIn data costs $1,060, with Tumblr at $95 and Fling at $297, all payable in bitcoin.
Stolen MySpace credentials for sale via The Real Deal. Cost: 6 bitcoins. pic.twitter.com/b44RDDKaqF
Leaked Source, a paid-for breach notification service, also has the MySpace data. On Friday, Leaked Source wrote that it had obtained the information from someone going by the alias "This email address is being protected from spambots. You need JavaScript enabled to view it.."
A search of underground forums by ISMG turned up a post from March 4 on a Russian-language carding site - where stolen credit card data is traded - by someone with the same alias.
The post offered batches of account data from seven services: social networking service Vkontakte (137 million accounts); games marketplace Mobango (6 million); MySpace (380 million); social network Badoo (126 million); Russian portal and instant messaging service Qip (133 million); file-sharing service Dropbox (103 million); and search engine and web portal Rambler.ru (101 million).
Whether Tessa88 actually does have all of that data is an open question. But the number of MySpace accounts cited in the post - 380 million - is fairly close to the number that has actually been confirmed.
Dropbox's Chris Peterson, head of security engineering, told Information Security Media Group on Wednesday that the company was aware of the post. The data advertised are not credentials for Dropbox and came from another source, he said.
Officials from the other services named in the post could not be immediately reached for comment. But it's not unheard of for hackers to falsely advertise credentials in order to tease buyers, even if the originated from a different breach.
MySpace and more: "Tessa88" claims to have additional stolen credentials data for sale. pic.twitter.com/FiFsKD3vir
When Was MySpace Breached?
MySpace, the social networking service that faded in 2008 with the rise of Facebook, said accounts created prior to June 11, 2013, were compromised. Those accounts were on MySpace's old platform, which was updated in mid-2013.
Based on feedback from people who had MySpace accounts, Hunt says his gut feeling is that the breach occurred in late 2008 or early 2009. Several people who have reached out to him said they created accounts in 2009 or 2010, but are not in the breach.
It's often difficult to determine the date range of affected accounts for breaches. The data could have been stolen at different points in time from multiple locations and then clumped together, which can cloud analysis, he says.
"This is not necessarily black and white," Hunt says. "There actually could be many shades in this."
The passwords for the MySpace accounts were hashed using SHA-1, a cryptographic function that has been considered vulnerable to cracking for more than a decade. Hashing turns plain-text data into a cryptographic representation, which is safer for online services to store.
But it is possible to reverse hashes, particularly for weak algorithms such as SHA-1, back to the original passwords, using graphics processors and purpose-built decoding tools. Generally, the longer and more complicated a password is - such as a mix of lower- and upper-case letters, symbols and numbers - the more time is needed to calculate the plain text.
With its new platform, MySpace said it strengthened its security. It now double-salts password hashes. Salting involves adding other data to a password before it gets hashed, which makes the hash much more computationally intensive to attempt to revert back into plain text.
Collateral Damage
As far as the latest breaches go, the MySpace release will not likely offer any particularly new insights. "It is like every other data breach in every other way except for the volume of records," Hunt says.
But it still adds to the hefty batches of data floating around. Spammers would likely find the email addresses useful. Since people often ignore the advice of security experts and reuse passwords, that data could be useful for account takeovers.
"All that stuff will get reused," Hunt says.
That poses challenges for other web services, and some are already taking action. Last week, Reddit said it had proactively reset 100,000 passwords in the previous two weeks in light of the password dumps.
"Though Reddit itself has not been exploited, even the best security in the world won't work when users are reusing passwords between sites," it wrote.
Amazon and LinkedIn have also in the past proactively reset accounts when the services suspect suspicious activity, Hunt says.
Meanwhile, Facebook in 2013 noted that it was actively monitoring data dumps for any email and password combinations that matched Facebook users' credentials, and forcing affected users to reset their accounts before regaining access.






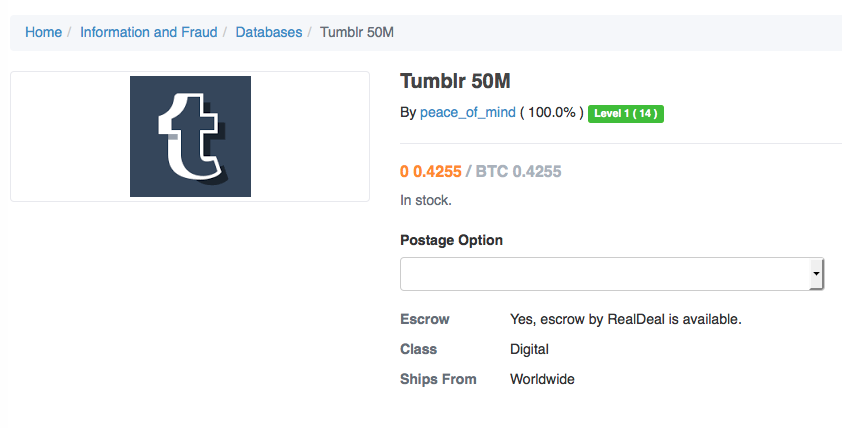 A hacker known as "Peace" has offered stolen Tumblr credentials for sale on the darknet marketplace known as The Real Deal.
A hacker known as "Peace" has offered stolen Tumblr credentials for sale on the darknet marketplace known as The Real Deal.