Fraud , Governance , Incident Response
CEO Fraud: Lessons From an Attack Why Employees Are the Best Lines of Defense
CEO fraud email campaigns are becoming far more common. And because these scams hinge on well-crafted social engineering, employee education is the best way to mitigate risk and avoid fraud losses.
See Also: Unlocking Software Innovation with Secure Data as a Service
The scams, also known as business email compromise attacks, are designed to fool accounting staff into scheduling and approving fraudulent wire transfers.
In recent weeks, my employer, Information Security Media Group, was targeted by one of these scams, but we dodged any fraud losses thanks to the alertness of my ISMG colleague who received the request.
Most of the bankers I've spoken to about these schemes, which continue to plague their small business customers, say they're increasingly dedicating time and resources to customer education - either by going out to visit clients, hosting educational events at their branches or posting information to their websites about the common types of CEO fraud they see.
CEO Fraud Losses Exploding
The FBI warned in August 2015 that losses linked to business email compromise attacks worldwide totaled more than $1.2 billion from October 2013 through August 2015.
But David Pollino, deputy chief security officer at Bank of the West, says losses in 2015 alone likely exceeded $1 billion.
According to the 2016 Association for Financial Professionals' Payments Fraud and Control Survey, 64 percent of organizations in 2015 were exposed to business email compromise scams, a leading cause of wire fraud today. As a result, 48 percent of organizations were exposed to wire fraud, up from 27 percent in 2014, the AFP notes.
"Each year, payments and cyber fraud schemes grow in sophistication, and knowing how to recognize and manage these threats is critical to protecting your organization," notes Nancy McDonnell, managing director and treasury executive for JPMorgan Chase, the underwriter for the AFP's annual survey. "Investing in the appropriate data-protection tools, infrastructure controls and employee education is essential for all businesses."
Simple Attacks Have Big Payout Potential
CEO fraud attacks are relatively unsophisticated, but nevertheless, often successful. They're typically waged with a spoofed email address that mimics that of a CEO, with the email demanding that an accounting staff member schedule an urgent wire transfer. The more sophisticated versions of these scams are well-researched and well-written, using company details that make the message appear legitimate.
Because of the success these types of attacks have seen in recent years, I'm not surprised ISMG was targeted.
The spoofed request we received, which went to an employee on our marketing team, immediately raised red flags. The URL for the reply-to email address feigning to be from our CEO was nothing close to the URL we use for email. What's more, the first name of our CEO was misspelled in the reply-to line as well as the body of the message.
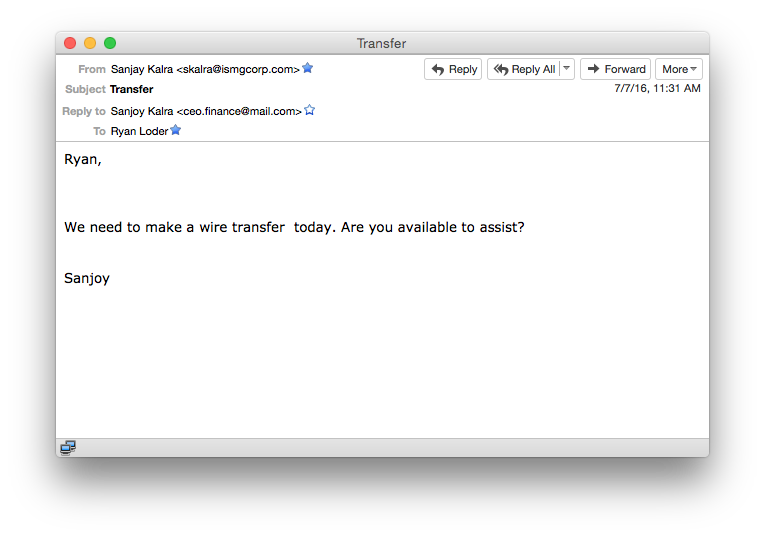 The first email ISMG received requesting a fraudulent wire. Note the URL for the reply-to line and the misspelling of our CEO's first name, which is spelled correctly in the from line. Also note the misspelling of his name in the body of the email message.
The first email ISMG received requesting a fraudulent wire. Note the URL for the reply-to line and the misspelling of our CEO's first name, which is spelled correctly in the from line. Also note the misspelling of his name in the body of the email message.The fraudster sent multiple requests asking our employee to transfer nearly $18,000 to an account at a top-tier bank in Texas. When we didn't comply, the requests eventually stopped.
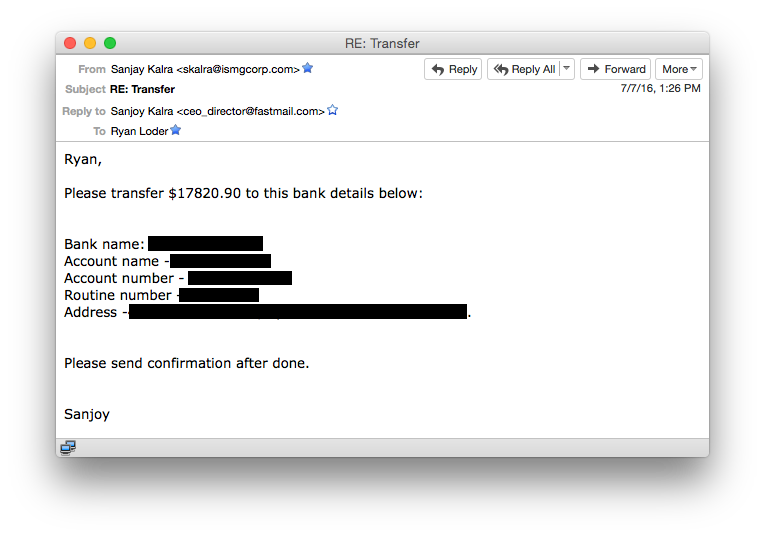 After a couple of email exchanges, the fraudster goes in for the kill, naming the amount and account to which the urgent wire should be sent.
After a couple of email exchanges, the fraudster goes in for the kill, naming the amount and account to which the urgent wire should be sent.Why Employees Are Fooled
Of course, some CEO fraud campaigns are far more sophisticated than the one that hit us at ISMG. So it can be relatively easy to trick someone not suspicious of the signs of danger to simply push payments through as a result of what appears to be urgent, persistent requests from the CEO.
Even in the campaign that hit one of our marketing employees, you can see the urgency the fraudster keeps stressing. In one of the requests, the fraudster notes that the wire must be scheduled immediately.
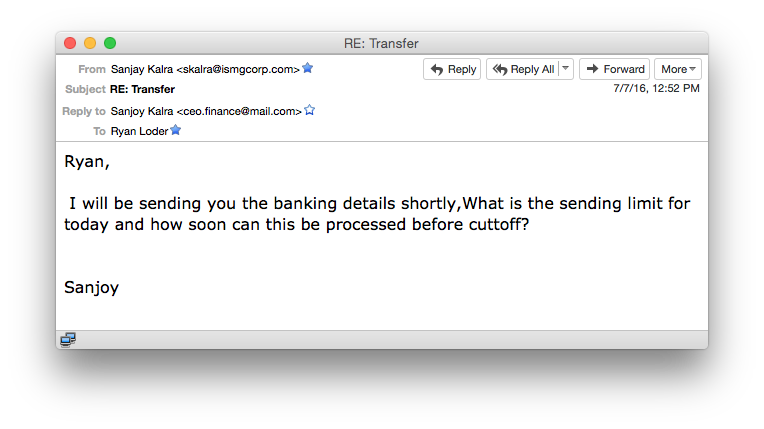 Urgency is typically part of all socially engineered schemes, and the CEO fraud attack that targeted ISMG was no different.
Urgency is typically part of all socially engineered schemes, and the CEO fraud attack that targeted ISMG was no different.It's easy to see how these scams often trick otherwise diligent employees into bypassing basic security measures designed to authenticate wire transfers, especially those going to unknown accounts.
Mitigating the Risks
Email authentication can help mitigate the risks, but nothing beats good old-fashioned employee education.
What should businesses do first if they fall victim to a CEO fraud scam? Fraud-fighting experts advise them to contact the fraud department at their banking institution, explain what happened and ask the bank to contact the fraud department at the recipient bank. After that, contact law enforcement.
After ISMG was targeted by a scam, we were advised by a U.S. attorney's office to file a complaint with the FBI's Internet Crime Complaint Center.
We did quite a bit of outreach to see if we could help law enforcement catch the fraudster. But so far, we haven't made much headway.
We're thankful that we didn't fall for the scam and glad we could share some of our experience with you.
And next week, at our New York Fraud and Breach Prevention Summit, we'll offer an important opportunity for banking institutions to learn more about what they should be doing to keep their business customers informed about emerging CEO fraud schemes - as well as the steps they should take when a scam is identified.
John Wilson, chief technology officer at online security firm Agari, will review some of the latest trends in email fraud schemes and describe what businesses can do to reduce their risks and what banks should be doing to educate their customers. I hope you'll join us.



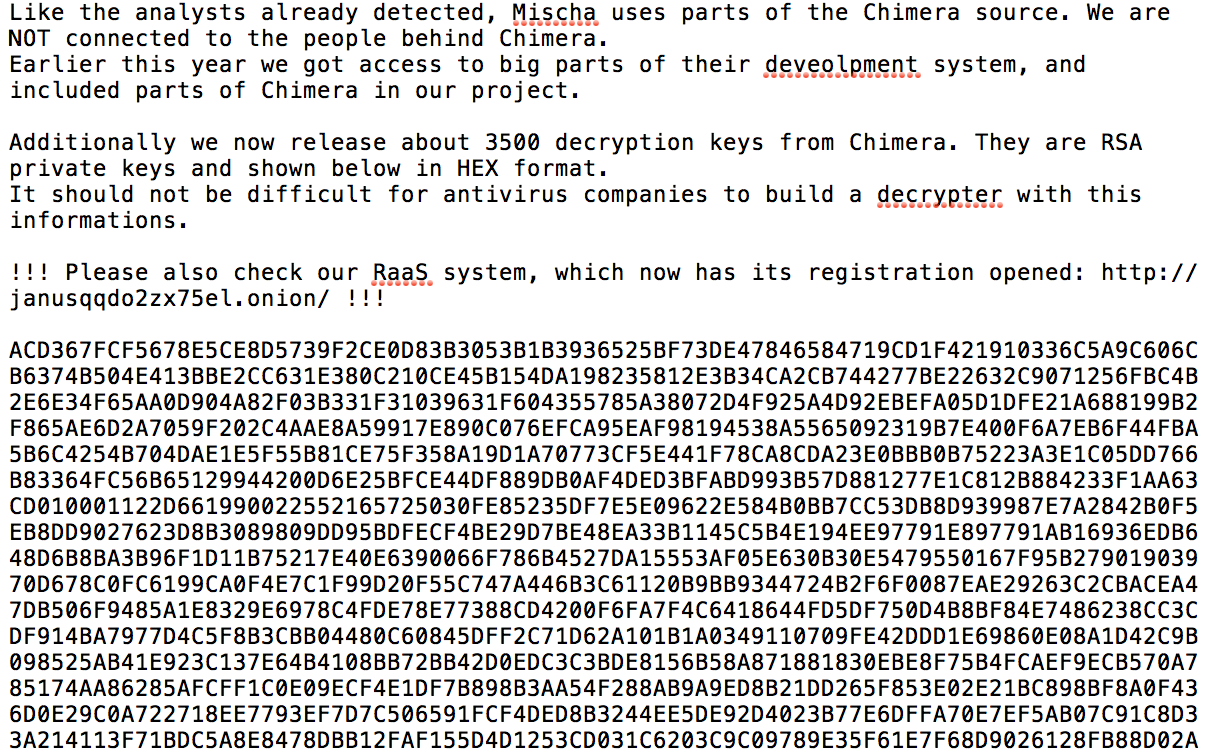 The Petya ransomware gang claims to have leaked 3,500 Chimera keys. (Source: Pastebin)
The Petya ransomware gang claims to have leaked 3,500 Chimera keys. (Source: Pastebin)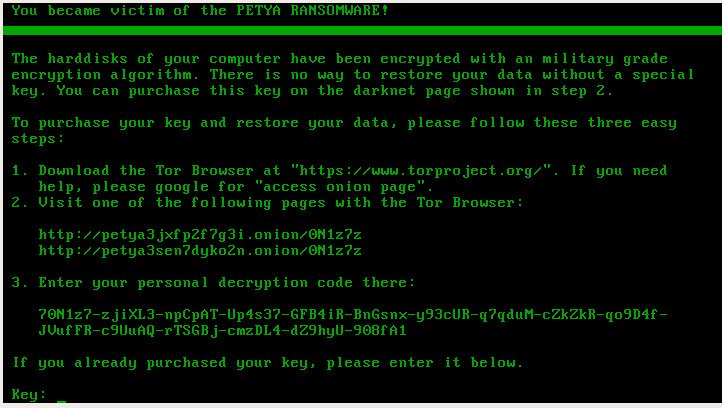 Pictured: Petya ransom demand. (Source: Malwarebytes)
Pictured: Petya ransom demand. (Source: Malwarebytes)


 Healthcare, more than any other industry, is increasingly in the crosshairs of attackers who seek to cause business disruption through evolving attacks such as ransomware. It's inevitable, frankly, that the vast majority of healthcare organizations will be diagnosed with ransomware. How must they prepare? What treatment is available for when they are struck?
FireEye's Dan McWhorter offers insight and strategies, including:
The size and scope of current attacks on healthcare entities;
Strategies and tools to help avoid being crippled by ransomware;
How organizations can harness threat intelligence in their defenses.
A surge in ransomware attacks on hospitals is driving healthcare organizations large and small to consider new and improved approaches to dealing with this evolving threat. In fact, one healthcare expert recently reported that one large East Coast health system turned away over 1 million ransomware emails in the month of March alone, more than any other industry. What can organizations do to avoid being the next victim - or the next big news headline?
Register for this session and get first-hand advice from Dan McWhorter, FireEye's Chief Intelligence Strategist. McWhorter is a member of the Department of Health and Human Services Health Care Industry Cybersecurity Task Force and has spent years analyzing cyberattacks on healthcare entities. In this informative webinar, McWhorter will provide you with case studies and first-hand advice on ways to leverage your threat intelligence - and prevent ransomware from victimizing your organization.
You might also be interested in …
Healthcare, more than any other industry, is increasingly in the crosshairs of attackers who seek to cause business disruption through evolving attacks such as ransomware. It's inevitable, frankly, that the vast majority of healthcare organizations will be diagnosed with ransomware. How must they prepare? What treatment is available for when they are struck?
FireEye's Dan McWhorter offers insight and strategies, including:
The size and scope of current attacks on healthcare entities;
Strategies and tools to help avoid being crippled by ransomware;
How organizations can harness threat intelligence in their defenses.
A surge in ransomware attacks on hospitals is driving healthcare organizations large and small to consider new and improved approaches to dealing with this evolving threat. In fact, one healthcare expert recently reported that one large East Coast health system turned away over 1 million ransomware emails in the month of March alone, more than any other industry. What can organizations do to avoid being the next victim - or the next big news headline?
Register for this session and get first-hand advice from Dan McWhorter, FireEye's Chief Intelligence Strategist. McWhorter is a member of the Department of Health and Human Services Health Care Industry Cybersecurity Task Force and has spent years analyzing cyberattacks on healthcare entities. In this informative webinar, McWhorter will provide you with case studies and first-hand advice on ways to leverage your threat intelligence - and prevent ransomware from victimizing your organization.
You might also be interested in …