Application Security , Mobility , Technology
How to Win Pokémon Go (By Cheating) What RASP Can Do For Your App
The hottest game in the market today is the new release Pokémon Go, developed by Niantic. The game forces you to go outside and interact with the real world (in a safe manner, hopefully). As you walk around, Pokémon appear and allow you to toss Pokéballs at them in an attempt to catch them all. The more you walk the more you can attempt to catch and the stronger your Pokémon become. The key mechanic in the game is to be able to use GPS to track your movement and combine that with mobile data points.
See Also: The Inconvenient Truth About API Security
Only 3 days after the release, reports of hacks started to roll in. This is common for the gaming industry. In the world of PC games, the most popular games usually are hacked the same day they release. In the mobile world, there is a false sense of security. The PC platform has been around for years, and developers and consumers are well aware of all the attacks out there. On the mobile platform, people still are not fully aware of what attackers can do, but they are learning quickly.
On a mobile platform, the most damaging attack is Jailbreaking or Rooting. This is the holy grail of attacking a mobile phone. Once the attacker has access to this, they control your device. This means that they can view any applications secret inner workings and have access to all your encrypted data. This also means they can modify how any application works and perform hacks that are even more nefarious.
With Pokémon Go, the attackers did just that, they Jailbroke their phones and analyzed the Pokémon Go application. If the key mechanism is to use GPS to track your location, then this is the first thing the attackers were aiming for. The attackers built a special library that injected itself into the Pokémon Go app that manipulated the GPS data that the Pokémon Go app tracked. This allowed the hacker (now cheater) to appear to be in places that they never were, and walk to areas they had never been.
The developers at Niantic tried to remediate this problem. They patched their code and added checks for jailbreak detection. Unfortunately, the damage had already occurred, and the hackers were able to quickly apply their own patches that disabled the applications jailbreak detection.
When it comes to Jailbreaking and Root detection, it is always better to start early and not share what you are doing. In the case of Pokémon Go, it was obvious that the application now included a jailbreak detection mechanism because the data that was being used stopped being allowed. In most applications, it is better to use a Runtime Application Self Protection (RASP) that checks for Jailbreaking and Rooting every time the application launches or becomes the front running application on the phone. When RASP checks for this, then it is best to simply exit the application gracefully and not let on to the hacker that something was found.
Even if jailbreak and root detection is compromised, and the attacker is able to patch the application, RASP can offer further technologies to help prevent the types of attacks that Pokémon Go experienced. The next attack used on the Pokémon Go application is a Library Injection attack. This is where the hacker was able to manipulate the GPS library and inject his own. By leveraging a RASP solution, the application will be able to detect these rouge libraries and will be able to prevent the application from loading them.
No solution is ever failsafe and no platform is ever free from attack. Every day new attacks are being rolled out, and every day a new solution is being developed. Technology like RASP will help the new mobile application ecosystem protect itself and make things easier in the life of an application developer.
Will LaSala is a Director of Services at VASCO, and a security industry veteran with a passion for gaming and ethical hacking.
For more information on Mobile Application Security solutions including RASP, visit https://www.vasco.com/products/application-security/digipass-for-apps.html.



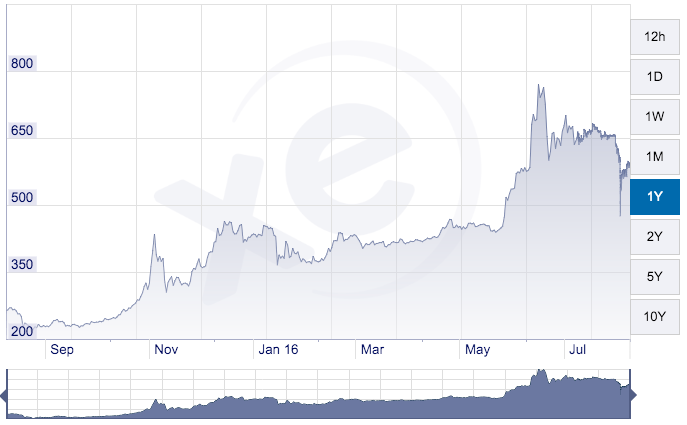 The value of a single bitcoin, in U.S. dollars, from August 2015 to August 2016. Source: XE Trade.
The value of a single bitcoin, in U.S. dollars, from August 2015 to August 2016. Source: XE Trade.

 Healthcare is in the middle of a major evolution toward digital, personalized medicine and the empowered patient. This massive push toward digital medicine brings about numerous security and interoperability challenges, including a shift in thinking from "supposedly known users" to "secure and trusted identities."
Ongoing regulatory and monetary incentive programs are driving healthcare providers to increase their EHR and E-Prescribing adoption. Additionally, the U.S. Office of the National Coordinator for Health Information Technology (ONC) is focused on strengthening identity-proofing and authentication of all participants in the healthcare system: providers, staff, business associates, and patients. With many organizations including HIMSS, AHIMA and CHIME calling for a nationwide unique patient identifier with support from the National Strategy for Trusted Identities in Cyberspace's (NSTIC), Identity Ecosystem Steering Group, a trusted digital identity will likely soon be on your IT agenda.
Knowing who is accessing PHI at any point in time is beyond critical to ensure security. How can the healthcare community move closer to making this leap to digital medicine without sacrificing security and confidentiality?
This exclusive webinar, sponsored by VASCO, will talk about ways your healthcare organization can create a secure bridge between the verified identity in the physical world and the online identity in the cyberspace on a state or national level. Co-hosts Michael Magrath, Director of Business Development at VASCO and a nationally recognized leader in the healthcare identity management field, and Andrew Showstead, Director of Technical Consultancy at VASCO, will discuss how your organization can deploy a unique, reusable and trusted digital patient credential that provides interoperability and links multiple players via a trust framework.
In this exclusive webinar, Magrath and Showstead will also discuss:
Different options to provide better patient and provider electronic authentication;
How superior identity management naturally leads to improved HIPAA and HITECH compliance;
How to implement remote ID verification;
How to secure end-to-end communications between patients and providers.
You might also be interested in …
Healthcare is in the middle of a major evolution toward digital, personalized medicine and the empowered patient. This massive push toward digital medicine brings about numerous security and interoperability challenges, including a shift in thinking from "supposedly known users" to "secure and trusted identities."
Ongoing regulatory and monetary incentive programs are driving healthcare providers to increase their EHR and E-Prescribing adoption. Additionally, the U.S. Office of the National Coordinator for Health Information Technology (ONC) is focused on strengthening identity-proofing and authentication of all participants in the healthcare system: providers, staff, business associates, and patients. With many organizations including HIMSS, AHIMA and CHIME calling for a nationwide unique patient identifier with support from the National Strategy for Trusted Identities in Cyberspace's (NSTIC), Identity Ecosystem Steering Group, a trusted digital identity will likely soon be on your IT agenda.
Knowing who is accessing PHI at any point in time is beyond critical to ensure security. How can the healthcare community move closer to making this leap to digital medicine without sacrificing security and confidentiality?
This exclusive webinar, sponsored by VASCO, will talk about ways your healthcare organization can create a secure bridge between the verified identity in the physical world and the online identity in the cyberspace on a state or national level. Co-hosts Michael Magrath, Director of Business Development at VASCO and a nationally recognized leader in the healthcare identity management field, and Andrew Showstead, Director of Technical Consultancy at VASCO, will discuss how your organization can deploy a unique, reusable and trusted digital patient credential that provides interoperability and links multiple players via a trust framework.
In this exclusive webinar, Magrath and Showstead will also discuss:
Different options to provide better patient and provider electronic authentication;
How superior identity management naturally leads to improved HIPAA and HITECH compliance;
How to implement remote ID verification;
How to secure end-to-end communications between patients and providers.
You might also be interested in …








 Disrupting the Cyber Kill Chain by Choking the Attack Where it is Most Vulnerable
API's, Server Integrity and Identities
Our adversaries follow a fairly well defined process of gaining access, establishing residency and exploiting our networks. If we understand how they act during each of these phases then we can make huge strides in curtailing their malicious endeavors. This session examines some best practices for defeating each phase of the attack:
Getting In With the growing deployment of inter application communications, attacks such as those at SnapChat, Yahoo and Tesla are increasingly leveraging insecure API's as entry points into networks. This webinar will examine why API protection must be implemented to minimize these vulnerabilities.
Staying In - Malicious code is very vulnerable while it is being installed and as it attempts to become resident. We'll explain how continuously refreshing the integrity of servers prevents malware from establishing a foothold.
Acting - If you have the keys to every door in a house, there is no need to hack through each door individually. Since one of the primary targets for attackers are credentials, they go after those with extensive privileges to a broad array of resources within your infrastructure in order to expedite their penetration. We'll see how to implement fine grained access control by granting authorization and access to resources only to those individuals that need it, decreasing the vulnerability of more users.
The "Cyber Kill Chain," adapted by Information Security Media Group experts from the military "Kill Chain" concept, has been demonstrated thoroughly over the past several years. Some of the most famous retail breaches, including the more recent OPM breach, are examples of successfully executed cyber kill chains.
Threat actors rely on their ability to:
Gain access to the network;
Remain on the network without being identified in a timely fashion;
Take action on the network.
While some see these as opportunities to exploit, they are also opportunities to shut-down and eliminate and attack.
Hear from industry experts on how to:
Keep the bad actors out of your network;
Keep the threat from staying in the network; shut down any breach by cycling systems;
Keep threat actors who have made it into the network from taking any action.
You might also be interested in …
Disrupting the Cyber Kill Chain by Choking the Attack Where it is Most Vulnerable
API's, Server Integrity and Identities
Our adversaries follow a fairly well defined process of gaining access, establishing residency and exploiting our networks. If we understand how they act during each of these phases then we can make huge strides in curtailing their malicious endeavors. This session examines some best practices for defeating each phase of the attack:
Getting In With the growing deployment of inter application communications, attacks such as those at SnapChat, Yahoo and Tesla are increasingly leveraging insecure API's as entry points into networks. This webinar will examine why API protection must be implemented to minimize these vulnerabilities.
Staying In - Malicious code is very vulnerable while it is being installed and as it attempts to become resident. We'll explain how continuously refreshing the integrity of servers prevents malware from establishing a foothold.
Acting - If you have the keys to every door in a house, there is no need to hack through each door individually. Since one of the primary targets for attackers are credentials, they go after those with extensive privileges to a broad array of resources within your infrastructure in order to expedite their penetration. We'll see how to implement fine grained access control by granting authorization and access to resources only to those individuals that need it, decreasing the vulnerability of more users.
The "Cyber Kill Chain," adapted by Information Security Media Group experts from the military "Kill Chain" concept, has been demonstrated thoroughly over the past several years. Some of the most famous retail breaches, including the more recent OPM breach, are examples of successfully executed cyber kill chains.
Threat actors rely on their ability to:
Gain access to the network;
Remain on the network without being identified in a timely fashion;
Take action on the network.
While some see these as opportunities to exploit, they are also opportunities to shut-down and eliminate and attack.
Hear from industry experts on how to:
Keep the bad actors out of your network;
Keep the threat from staying in the network; shut down any breach by cycling systems;
Keep threat actors who have made it into the network from taking any action.
You might also be interested in …