 Spear-phishing message. Source: Volexity
Spear-phishing message. Source: VolexityOne of the two groups that hacked the Democratic National Committee - both believed to be operating from Russia - has been spotted lurching into action again, targeting a range of organizations and even sending fake emails bearing the Clinton Foundation name.
See Also: Managing Identity, Security and Device Compliance in an IT World
Shortly after Donald Trump became president-elect, the group that security researchers have nicknamed Cozy Bear - aka CozyDuke or APT 29 - launched a volley of malware-laced emails that targeted a range of organizations relating to national security, defense, international affairs, public policy as well as European and Asian studies, according to Volexity, a security firm based in Washington, D.C. Volexity refers to the group as "The Dukes."
"They have had tremendous success evading anti-virus and anti-malware solutions at both the desktop and mail gateway levels," writes Volexity's founder, Steven Adair, who has worked with the Shadowserver Foundation, a volunteer effort that gathers information relating to online attacks, including malware and botnets.
Cozy Bear was identified by cybersecurity firm Crowdstrike as being one of two suspected Russia-leaning groups that penetrated the DNC, later causing turmoil in the party after it released batches of emails (see DNC Breach More Severe Than First Believed).
With the 2016 U.S. presidential election over, it appears the group, which Crowdstrike suspects is affiliated with Russian intelligence, has resumed its regular operations. In the case of these attacks, the group appears to be trying to milk post-election chatter to trick people into clicking on malicious emails.
Spoofed Messages
Adair writes that Volexity has been watching Cozy Bear closely since August, when the group launched spear-phishing attacks on U.S. think tanks and other non-governmental organizations. Spear-phishing refers to attackers crafting fake emails that they send to carefully selected targets. The emails, which arrive with malicious links or attached malware, are designed to trick users into opening them, leading to attackers seizing control of the target's PC, stealing the data it stores and using it to penetrate additional networks or systems to which the endpoint connects.
 A spear-phishing email attributed to Cozy Bear by Volexity.
A spear-phishing email attributed to Cozy Bear by Volexity.In August, Volexity saw Cozy Bear send spoofed messages to victims that appeared to come from such respected groups as Transparency International, the Center for a New American Security, the Institute for Strategic Studies, Eurasia Group and the Council on Foreign Relations.
Those emails contained Microsoft Word or Excel attachments that included legitimate content. But the documents were rigged with malicious macros - a type of small application designed to enable some other kind of functionality - that downloaded a PNG image file from another server. Inside that PNG file was a backdoor hidden using steganographic techniques, which means hiding data inside another file.
The latest volley of emails, meanwhile, came from Gmail accounts created by the attackers, using what appears to have been compromised email accounts belonging to individuals within Harvard University's Faculty of Arts and Sciences. Adair notes that two of the messages pretended to have been forwarded from the Clinton Foundation, officially known as the Bill, Hillary & Chelsea Clinton Foundation.
Some of the messages sought to exploit suggestions by President-elect Donald Trump prior to the election that the process could be corrupted, sporting such subject lines as "Why American Elections Are Flawed." But Trump's surprising victory on Nov. 8 probably diminishes interest in that kind of bait, at least from his supporters.
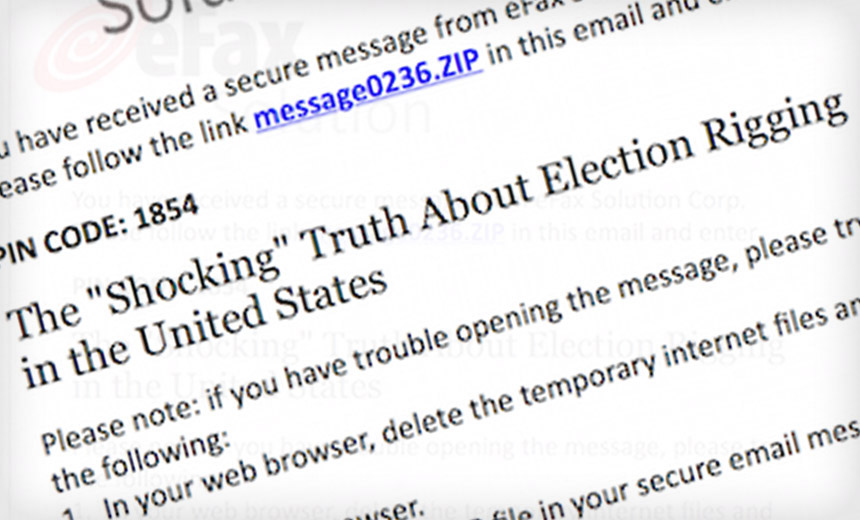
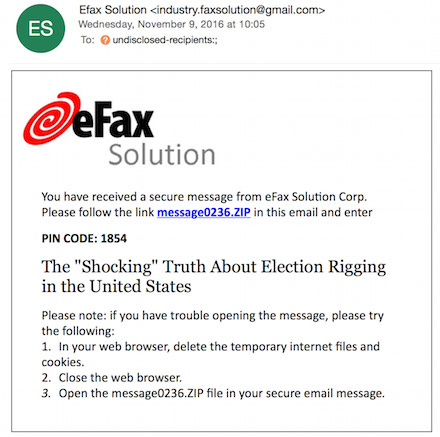
Another email spotted by Volexity was headlined: "The shocking truth about election rigging in the United States." That sample purported to come from online fax service provider eFax. Adair writes that it included a link to a zip file with a ".lnk" Microsoft shortcut file.
"This shortcut file contains PowerShell commands that conduct anti-VM [virtual machine] checks, drop a backdoor and launch a clean decoy document," he writes.
Reminder: Email Is Dangerous
The tactics purported to be used by Cozy Bear are similar to the ones reportedly employed by its more flamboyant brother, known as Fancy Bear, to compromise the DNC and the World Anti-Doping Agency. Both breaches caused considerable embarrassment and controversy, but technologically speaking the attacks weren't sophisticated (see Hackers Dump U.S. Olympic Athletes' Drug-Testing Results).
The breaches are a reminder of this fact: Email is dangerous. If a spear-phishing email manages to pass security checks, even hardened security experts can be tricked by messages that look real or that were sent from an email account used by someone they know, but which may have been hacked.
While security software has improved, it's still a leaky defense. Accordingly, the usual advice applies: Patch regularly, run security software and if there's any whiff of doubt about an email or an attachment, don't open it.


 President-elect Donald Trump
President-elect Donald Trump


