Data Breach , Fraud , Payments Fraud
Millennium and Noble House Learned of Breaches via Secret Service Millennium Broadway Hotel New York
Millennium Broadway Hotel New YorkTwo hotel chains are warning that they've suffered point-of-sale malware infections that compromised customers' payment card data. Both say they were alerted to related card fraud by the U.S. Secret Service and that they're now assisting law enforcement agencies' investigations.
See Also: The Inconvenient Truth About API Security
Millennium Hotels & Resorts North America, based in Denver, says that a malware infection that lasted more than three months resulted in a breach of card data from "food and beverage POS systems" at all 14 of its U.S. hotels. Separately, Noble House Hotels and Resorts, based in Kirkland, Wash., warned that systems at one of its properties were infected with POS malware for a two-month period.
In both cases, attackers may have compromised cardholders' names, payment card numbers, expiration dates and CVV numbers.
The timing of the two breach alerts, and fact that both hotel chains learned about the breaches via the Secret Service, suggests that the same cybercrime group may have been responsible. The Secret Service couldn't be immediately reached for comment on that possibility. But there's also strong evidence that the breach is tied to a recent alert from Oracle MICROS, warning that it had found malicious code in the software that runs POS devices that it provides to numerous businesses.
Millennium Breach: 14 U.S. Hotels Affected
Millennium says that after it was alerted to the breach at all of its 14 U.S. properties, it learned from its "third-party service provider - that supplies and services the affected point-of-sale systems - that it had detected and addressed malicious code in certain of its legacy point-of-sale systems, including those used by MHR," according to the hotel's breach notification. "MHR immediately adopted additional security measures as recommended by the third-party service provider."
The affected hotel properties are located in Anchorage, Alaska; Boston; Boulder, Colo.; Buffalo, N.Y.; Chicago; Cincinnati; Durham, N.C.; Los Angeles; Minneapolis; Nashville, Tenn; New York; and Scottsdale, Ariz.
Millennium says that hotel property management and booking systems are separated from its food and beverage POS systems, and that only the latter appear to have been infected. Millennium spokesman Peter Krijgsman tells Information Security Media Group that the company runs a number of systems on segmented networks - by region and hotel function - and that it changed all access passwords for affected POS systems following the breach. "We will continue to monitor for signs of intrusion, as we do as part of our standard security protocols," he says.
The company has not released details of how many customers may have been affected by the breach, which lasted from early March to mid-June. "We believe it involved less than 5,000 cards, and while the number of affected customers is not as large as the numbers reported by other, larger U.S. hotel operators, we take no comfort in that fact, as any breach is unacceptable," Krijgsman says, adding that Millennium's investigation remains ongoing. "If it reveals malware on our systems or if other types of personally identifiable information that can be used to commit identity theft have been potentially compromised, credit monitoring services likely will be provided."
The hotel chain declined to name its POS supplier, but said that "the third party is a significant supplier of POS systems to the hotel industry" and that "it is aware of these issues." The company also declined to name the outside incident response firm that it hired to investigate the breach.
Asked to clarify the hotel's reference to "legacy" POS systems, Krijgsman says that in this case it does not necessarily mean outdated. "While the affected POS systems are not the newest systems in the provider's portfolio, they are still supported by the supplier," he says. "Legacy systems can also signify systems provided by a company subsequently acquired by another."
A recent job listing offers a potential clue to the identity of its POS vendor. In the June 6 advertisement for a banquet manager, Millennium says that whoever gets the job must "utilize POS (Micros and Delphi) to accurately charge guests," apparently referring to Oracle MICROS, which provides POS systems to more than 330,000 locations, including hotels, across 180 countries. Oracle recently warned that it "has detected and addressed malicious code in certain legacy MICROS systems" (see Recent POS Attacks: Are They Linked?).
Breach at Ocean Key Resort & Spa
 Ocean Key Resort & Spa in Key West, Florida
Ocean Key Resort & Spa in Key West, Florida
Meanwhile, Noble House Hotels and Resorts says that its Ocean Key Resort & Spa in Key West, Fla., was infected by POS malware April 26 to June 8. Its breach alert says anyone who used a payment card at the hotel during that time - including at its restaurant and bars - may have had their card data compromised.
The Ocean Key breach follows a 2015 breach at The Commons, a Noble property in Minneapolis. Noble said that a POS malware infection at that hotel from January to August 2015 resulted in the suspected theft of 19,000 payment cards.
In the case of the Ocean Key breach, spokesman Simon Barker tells ISMG that the hotel chain hired FireEye's Mandiant incident response firm to investigate.
"At this time, it appears that 12,134 payment cards may have been affected by the incident at Ocean Key Resort," Barker tells ISMG. "We are in the process of sending notification letters to the guests for whom we have names and contact information. Legal notices have been placed in newspapers and a press release distributed nationally." The company says it's also working with payment card issuers to help them directly notify affected cardholders as well as institute heightened fraud monitoring.
The company has promised to reimburse any fraud that card issuers fail to cover. "If guests incurred costs that their financial institution declined to reimburse related to fraudulent charges on a payment card used at Ocean Key Resort & Spa, we will reimburse guests for any such reasonable, documented costs that their financial institutions decline to pay," he says. "We are not offering credit monitoring services as they do nothing to prevent fraudulent transactions on existing payment cards."
The hotel declined to discuss what security measures it had in place prior to the breach and what measures it plans to take. "We take the protection of payment card data security very seriously, but I'm afraid we are not prepared to discuss our specific security measures," Barker says.
These recent breaches at hotel chains follow a number of similar breaches in recent months that have affected Hilton, Hyatt, Starwood Hotels and Resorts, Omni and Trump Hotels, among others.



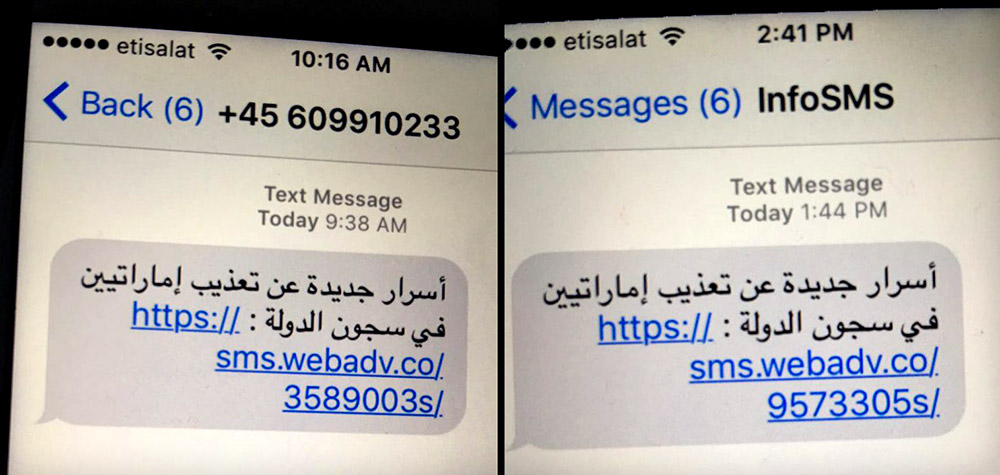 SMS text messages received by Mansoor (English: "New secrets about torture of Emiratis in state prisons"), via Citizen Lab. It says the sender's phone numbers were spoofed.
SMS text messages received by Mansoor (English: "New secrets about torture of Emiratis in state prisons"), via Citizen Lab. It says the sender's phone numbers were spoofed.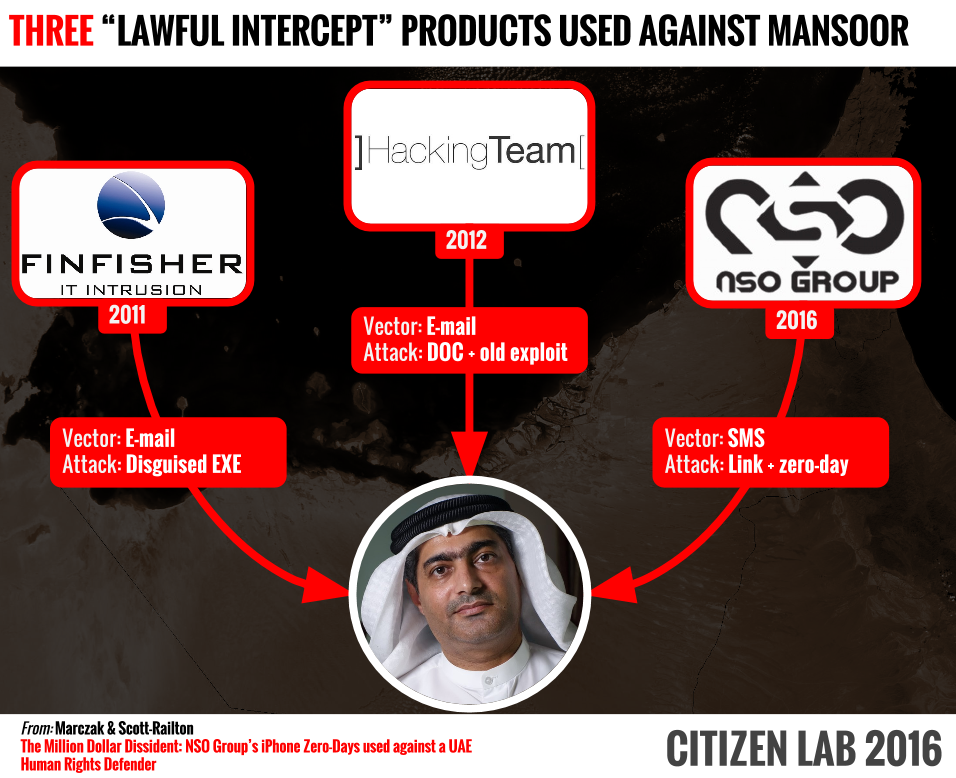 Ahmed Mansoor has been targeted multiple times using spyware sold to governments. Source: Citizen Lab
Ahmed Mansoor has been targeted multiple times using spyware sold to governments. Source: Citizen Lab
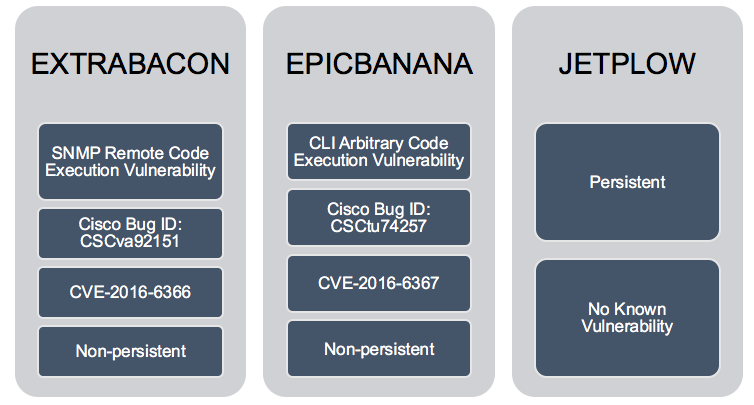 Exploits and related vulnerabilities targeting Cisco ASA, Cisco PIX and Cisco Firewall Services that have been ascribed to the Equation Group and/or NSA.
Exploits and related vulnerabilities targeting Cisco ASA, Cisco PIX and Cisco Firewall Services that have been ascribed to the Equation Group and/or NSA.

 Convicted hacker Roman Seleznev. Source: Department of Justice
Convicted hacker Roman Seleznev. Source: Department of Justice