
The National Institute of Standards and Technology is moving ahead with an initiative to create standards for cryptographic algorithms for small computing devices, such as those found in automobiles, control systems, smart grids and the Internet of Things.
See Also: A Smarter Approach to Third-Party Vendor Risk: A Case Study
NIST last month issued a draft report, Interagency Report 8114: Report on Lightweight Cryptography, which provides an overview of its lightweight cryptography project and describes plans to standardize these algorithms.
Cryptographic algorithms designed to secure large computer devices - servers, desktops, tablets and smart phones - don't necessarily scale downward to function effectively on smaller devices - think embedded systems, radio frequency identification devices, sensor networks and thousands upon thousands of devices that make up the Internet of Things.
Vulnerability Anxieties
Experts have expressed some anxiety about the vulnerabilities created by the lack of encryption for smaller devices. "Everyone who understands cryptography standards and their applications shares the same feeling," says Lily Chen, NIST's acting group leader for cryptographic technology. "We have seen too many lightweight cryptography primitives [low-level algorithms used to build cryptographic protocols for computer security systems] broken. In order to achieve lightweight metrics, special design methodologies are applied. Some of the methodologies are less understood about the security impacts. Even for well-designed lightweight cryptography primitives, misuse could lead to security mishaps."
As smaller computing devices become ubiquitous, NIST is exploring ways to develop tailored algorithms to encrypt them. NIST, in 2013, initiated the lightweight cryptography project to study the performance of the existing NIST-approved cryptographic standards on these so-called constrained devices, understand the need for dedicated lightweight cryptographic standards and, if necessary, design a transparent process for standardization.
Constrained Environments
"We're talking about some very constrained devices, 8-bit processors [with] little memory, low speed, low power," says cryptographer and IT security author Bruce Schneier. He sees the lightweight cryptography project as important because "a lot of the algorithms we have just aren't suitable for these constrained environments. ... We want good algorithms for constrained devices."
NIST plans to create a portfolio of lightweight primitives through an open process, in which submitters describe physical, performance and security characteristics of these algorithms. NIST used a similar process to develop its portfolio of block cipher modes of operations. A block cipher mode is an algorithm that provides an information service, such as confidentiality or authentication.
Power Limits
Because many small computing devices have power and/or bandwidth constraints, lightweight cryptographic solutions must be designed, in many instances, for specific types of devices. For example, some RFID devices draw power from nearby sources to function. That lack of internal power places limits on how the devices can be encrypted.
"The guidance has to be very specific for each application environment," NIST's Chen says. "It is a different approach compared to our general purpose cryptography standards. For lightweight cryptography, to be specific is the key to make sure the guidance can be effective to avoid introducing security flaws."



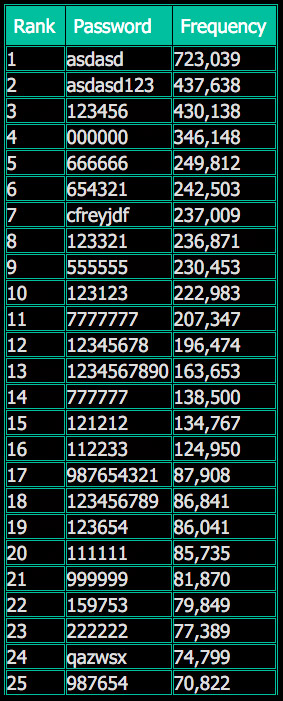 Top top 25 password choices of Rambler users. Source: LeakedSource
Top top 25 password choices of Rambler users. Source: LeakedSource Brazzersforums remained offline in the wake of the breach report.
Brazzersforums remained offline in the wake of the breach report. Cisco ASA 5540 Adaptive Security Appliance. Photo:
Cisco ASA 5540 Adaptive Security Appliance. Photo: 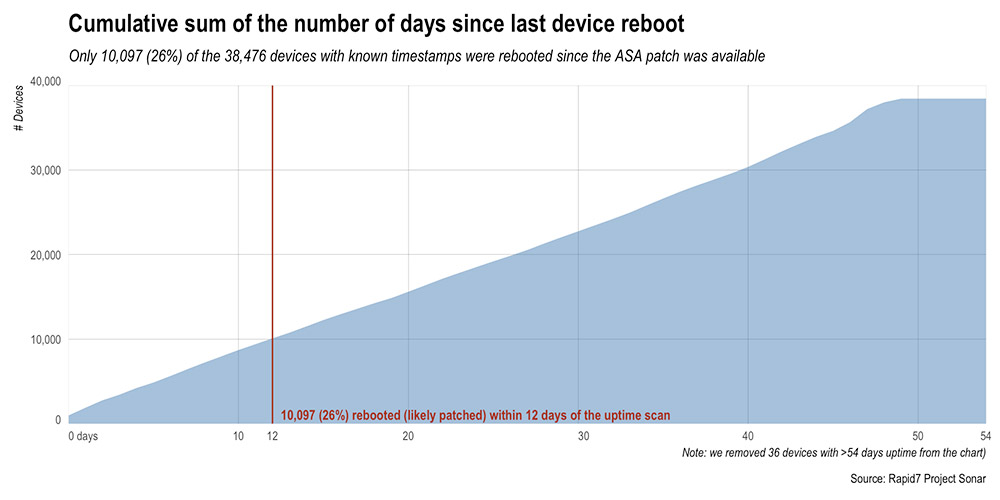 The number of detected Cisco ASA devices that have been rebooted - and thus theoretically patched - following EXTRABACON-related warnings. Source: Rapid7
The number of detected Cisco ASA devices that have been rebooted - and thus theoretically patched - following EXTRABACON-related warnings. Source: Rapid7