DDoS , Endpoint Security , Risk Management
Experts Testify on IoT Dangers and the Need for Standards, Regulations Cybersecurity experts Bruce Schneier and Kevin Fu testify.
Cybersecurity experts Bruce Schneier and Kevin Fu testify.What's needed to bolster the security of internet of things devices to help prevent cyberattacks, such as the October botnet-driven distributed denial-of-service attack on web services provider Dyn that crippled Netflix, Twitter and many other websites?
See Also: Protect Your Identity Infrastructure
It could boil down to a combination of implementing industry standards, incentives and regulations, a panel of experts testified at a joint House committee hearing on Nov. 16 exploring the role of connected devices in cyberattacks.
The hearing was aimed at helping Congress review recent DDoS attacks waged using botnets built on connected devices, understand current countermeasures and consider efforts to combat malicious actors that could target vulnerabilities, Rep. Greg Walden, R-Ore., noted in his opening remarks.
Worse Attacks on Horizon?
The recent DDoS attack on Dyn, which involved more than 100,000 IoT devices ranging from baby monitors to webcams, was relatively "benign" and could be a precursor to more sophisticated cyberattacks exploiting IoT device vulnerabilities, according to Bruce Schneier, a fellow at the Kennedy School of Government at Harvard University and CTO of Resilient, an IBM company.
In the Dyn cyberattack, he testified, "some websites went offline for a while. No one was killed. No property was destroyed. But computers have permeated our lives. The internet now affects the world in a direct physical manner. The internet of things is bringing computerization and connectivity to many tens of millions of devices worldwide. We are connecting cars, drones, medical devices and home thermostats. What was once benign is now dangerous."
Medical device cybersecurity expert Kevin Fu, CEO of Virta Labs and professor of electrical engineering and computer science at the University of Michigan, testified: "No one has been able to provide assurance that a future Dyn-like attack will not cause a massive, nationwide healthcare outage" or cause other major disruptions to, for example, power grids.
Multifaceted Approach?
Under questioning by committee members, the experts testified that shoring up security of IoT devices - without killing innovation - might require a multifaceted approach that includes incentives, regulations and standards designed to make sure security is built into products.
"We're asking consumers to shore up security," Scheier said, expecting buyers of IoT products, for example, to change default passwords. "There shouldn't be default passwords [in devices]; this shouldn't be consumers' problem."
Dale Drew, chief security officer of Level 3 Communications, testified: "The best place to start is with standards ... and then apply pressure. If, for example, IoT devices were capable of 'auto-patching,' ... [that would] help keep infrastructure healthy."
But many manufacturers aren't embedding security into their products because of a lack of economic incentives, the security experts said. Consumers and businesses aren't necessarily willing to pay extra for security - or often aren't even aware of the risks, the experts testified.
Also, manufacturers of IoT products containing software and hardware components from many different vendors - including foreign suppliers - aren't necessarily building security into all those components. To complicate matters, "there's no national testing lab" to assess the cybersecurity of IoT devices, and there are no clear national or global standards, Fu noted.
The experts didn't agree on whether one set of cybersecurity-related standards could fit all IoT devices or if standards and best practices should vary depending upon the industry where devices are used.
The National Institute of Standards and Technology has done a good job of setting standards and principles for cybersecurity, Fu noted (see: NIST Guidance Takes Engineering Approach to InfoSec). But that doesn't necessarily mean companies comply with principles, "many that have been known for 30 years," he said.
Potential Dangers
Potential risks posed by cyberattacks against medical devices are similar to preventable risks involved in automobile travel before airbags were implemented, Fu said.
"IoT security is woefully inadequate," he testified. "I do believe this will require some kind of government mandate. We don't have economic drivers."
Rep. Ann Eshoo, D-Calif., noted that she had previously introduced legislation "that hasn't gained much traction" proposing creation of "a good housekeeping seal of approval" for IoT devices meeting a set of cybersecurity standards. The idea is to promote "security without dampening innovation," she noted.
Schneier suggested that there may be a need for a new federal government agency to address the cybersecurity concerns of connected devices.
"The choice isn't between government or no government [involvement] - it's a choice between smart and stupid government involvement," Schneier testified. "I'm not a regulatory fan, but this is the world of dangerous things. There's a fundamental difference between [a cyberattack causing] a spreadsheet to crash and me losing data - and a car crashing and losing life. The internet era of fun and games is over."
Workforce Challenges
Fu suggested that to better protect the U.S. infrastructure, the nationwide cybersecurity talent shortage needs to be addressed.
"Universities, industry and government must find the strength and resolve to invest in embedded cybersecurity with interdisciplinary science and engineering, industrial partnerships for research and education, and service to the nation," he testified.




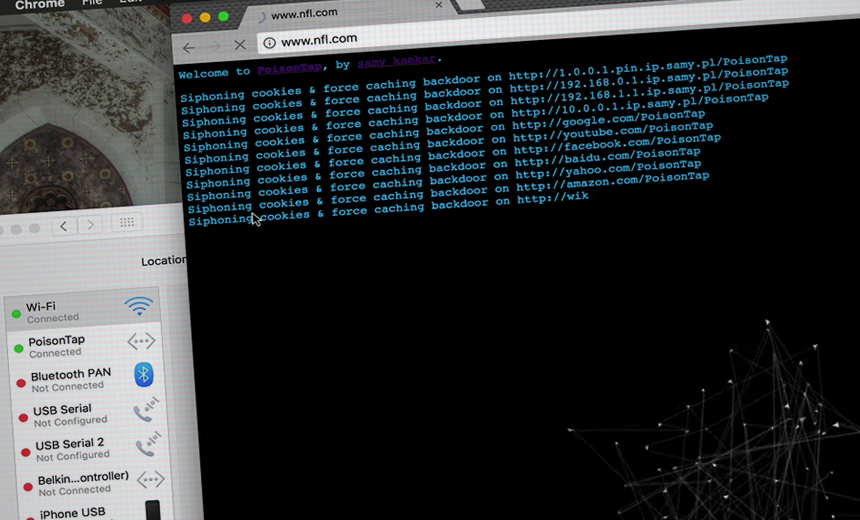 Image from Samy Kamkar video on PoisonTap
Image from Samy Kamkar video on PoisonTap
 How do you protect against cyberattacks? If you're like most organizations, you have layered security defenses that safeguard common threat vectors at your endpoints, as well as your apps and services. You may even have training policies in place to teach your employees not to click on malware embedded in a phishing email.
Increasingly, however, bad actors are leveraging techniques that don't require human interaction. An attacker can compromise a website exploiting, say, a WordPress or Drupal plugin to automatically launch a browser exploit that can lock up your organization's files. This webinar, hosted by Zscaler, will walk you through some of these seemingly invisible attacks and show how its Cloud Security Platform can identify the root cause of attacks - and stop them before they can impact your business.
Even the best layered cybersecurity defenses can fall victim to an innovative attack. Worse, because these defenses have so many moving parts, detecting and mitigating cyberattacks is difficult to do before the damage is done. Simply put, you need a defense that provides visibility into root causes of these myriad attacks - so that you can protect against evolving, oftentimes relentless exploits.
In this exclusive webinar, Deepen Desai, Senior Director, Security Research at Zscaler, will go through a real-time demo of a typical cyberattack. He will also delineate:
The evolution in the techniques cybercriminals are using to attack your systems;
Best practices and security recommendations to defend against multistage attacks; and
How Zscaler Cloud Security Platform can consolidate and harden your security posture.
How do you protect against cyberattacks? If you're like most organizations, you have layered security defenses that safeguard common threat vectors at your endpoints, as well as your apps and services. You may even have training policies in place to teach your employees not to click on malware embedded in a phishing email.
Increasingly, however, bad actors are leveraging techniques that don't require human interaction. An attacker can compromise a website exploiting, say, a WordPress or Drupal plugin to automatically launch a browser exploit that can lock up your organization's files. This webinar, hosted by Zscaler, will walk you through some of these seemingly invisible attacks and show how its Cloud Security Platform can identify the root cause of attacks - and stop them before they can impact your business.
Even the best layered cybersecurity defenses can fall victim to an innovative attack. Worse, because these defenses have so many moving parts, detecting and mitigating cyberattacks is difficult to do before the damage is done. Simply put, you need a defense that provides visibility into root causes of these myriad attacks - so that you can protect against evolving, oftentimes relentless exploits.
In this exclusive webinar, Deepen Desai, Senior Director, Security Research at Zscaler, will go through a real-time demo of a typical cyberattack. He will also delineate:
The evolution in the techniques cybercriminals are using to attack your systems;
Best practices and security recommendations to defend against multistage attacks; and
How Zscaler Cloud Security Platform can consolidate and harden your security posture.