Breach Preparedness , Breach Response , Compliance
Groups Provide Feedback on Potential Changes to the HIPAA Rules(HealthInfoSec) • February 19, 2019
Federal regulators have more than 1,300 comments to sort through in response to a request for information issued in December about potential changes to the HIPAA rules.
Comments submitted to the Department of Health and Human Services run the gamut from suggesting that HHS' Office for Civil Rights create new "safe harbors" to shelter certain organizations from breach-related HIPAA enforcement actions to better aligning other federal privacy regulations with the HIPAA rules.
OCR's December RFI sought feedback by Feb. 12 on a variety of potential changes to the HIPAA rules designed to reduce the "regulatory burden," including ways to improve secure data sharing for patient care coordination (see: HHS Seeks Feedback on Potential HIPAA Changes).
—CHIME
OCR has not indicated when it plans to issue a proposed rule to modify HIPAA. Of course, such modifications would have a direct impact on the policies that must be carried out by CISOs and chief privacy officers.
'Safe Harbors'
Several organizations - including the College of Healthcare Information Management Executives, the American Hospital Association, and the American Medical Association - suggest that OCR create new safe harbors that would shelter organizations from HIPAA enforcement actions - including financial penalties - after a health data breach if the breached entities had abided by certain standards for safeguarding PHI.
"We recommend OCR create a safe harbor for providers who have demonstrated they are meeting a set of best practices such as those developed under the public-private effort known as the Health Industry Cybersecurity Practices: Managing Threats and Protecting Patients," CHIME writes.
Among its other breach-related suggestions, CHIME also recommends "amending [HIPAA] language around the responsibilities of business associates by adding that for breaches that start with them they must bear responsibility." That includes notification of media and breach reporting to HHS. Under the current HIPAA rules, covered entities are responsible for notification of breaches by their business associates.
The AHA offers similar safe harbor suggestions. "Despite complying with HIPAA rules and implementing best practices, hospitals and healthcare providers will continue to be the targets of sophisticated cyberattacks, and some attacks will inevitably succeed," AHA writes.
Whether exploiting previously unknown vulnerabilities or taking advantage of an organization with limited resources, attackers will continue to be successful, AHA notes. "The AHA believes that victims of attacks should be given support and resources, and enforcement efforts should rightly focus on investigating and prosecuting the attackers," AHA writes.
"Merely because an organization was the victim of a cyberattack does not mean that the organization itself was in any way at fault or unprepared. Similarly, a breach does not necessarily equate to a HIPAA Security Rule compliance failure. Moreover, an aggressive regulatory enforcement approach could be counter-productive and hinder valued cooperation by the victims of cyberattack with other parts of the government, such as the Department of Homeland Security, FBI and the intelligence community. Instead, successful attacks should be fully investigated, and the lessons learned should be disseminated widely to prevent successful similar future attacks."
AHA says it urges OCR to consider ways "to develop a safe harbor for HIPAA covered entities that have shown, perhaps through a certification process, that they are in compliance with best practices in cybersecurity, such as those promulgated by HHS, in cooperation with the private sector, under ... the Cybersecurity Information Sharing Act."
 HHS OCR is considering changes to the HIPAA rules.
HHS OCR is considering changes to the HIPAA rules.Those best practices were developed through public-private collaboration after months of deliberation and development, AHA notes.
"A safe harbor would give covered entities clarity about the level of diligence they need to exercise, including when they agree to share and exchange PHI with other systems/organizations through tools like health information exchanges, to avoid OCR enforcement when an attacker gains access."
Providing Incentives
To best assist clinicians with implementing good security practices, the AMA writes, it "encourages OCR to help reframe the conversation around securing health information from punitive requirements - for example, fines and penalties associated with security failure - to developing positive incentives that encourage ways to bolster practice resilience and protect patient information."
One such incentive is to permit "multiple paths to compliance" with HIPAA's Security Rule, AMA writes. "OCR could revise [HIPAA] to include a new clause stating that covered entities that adopt and implement a security framework - such as the NIST Cybersecurity Framework - or take steps toward applying the Health Industry Cybersecurity Practices - the primary publication of the Cybersecurity Act of 2015 Task Group - are in compliance with the Security Rule. "This modification would help make cybersecurity more understandable and attainable to physicians, particularly those that are most vulnerable due to lack of resources and expertise."
Sharing PHI
Among the potential HIPAA modifications under consideration, OCR sought comment on promoting information sharing for treatment and care coordination and/or case management by amending the HIPAA Privacy Rule to encourage, incentivize or require covered entities to disclose PHI to other covered entities.
The AHA is not in favor of changes that would require covered entities to disclose PHI to other covered entities.
"Hospitals and healthcare providers want to share health information to support care coordination, case management and the transition to value-based health care and do so when permitted legally. Amending the privacy rules to require covered entities to disclose PHI to other covered entities will not promote greater information sharing for these important purposes," AHA writes.
The AHA notes, however, "The HIPAA medical privacy regulation should permit a patient's medical information to be used by and disclosed to all participant providers in an integrated care setting without requiring that individual patients have a direct treatment relationship with all of the organizations and providers that technically 'use' and have access to the data."
Accounting of Disclosures
Among other areas being scrutinized by OCR is the long overdue requirement under the HITECH Act to implement an accounting of disclosures regulation that has been on the shelf for several years.
HHS' previous proposal for an accounting of disclosures was published in May 2011, but feedback from the healthcare sector was mostly negative. That's because the proposal would have required healthcare organizations to provide patients, upon request, with a complete list of everyone who has electronically viewed their information.
In its RFI, OCR sought input related to entities providing upon patients' request an accounting of disclosures of patient information for treatment, payment and healthcare operations from electronic health records "in a manner that provides helpful information to individuals, while minimizing regulatory burdens and disincentives to the adoption and use of interoperable EHRs."
Some of the organizations submitting feedback note in their comments that most healthcare entities receive very few requests from patients for an accounting of disclosures.
In its comments, the American Health Information Management Association writes that its "members have noted that the number of requests they receive is significantly low, receiving anywhere from 0-3 accounting of disclosure requests per year ... Often times, the accounting of disclosures request is limited to a particular party or parties and not a request for all who may have accessed the record."
For example, the patient may be concerned that a family member, friend, or former spouse obtained access to their record for an inappropriate purpose, AHIMA notes.
"Once it is explained to the patient that an accounting would not necessarily indicate whether such access occurred by the particular individual, the health information management professional transitions to performing an investigation into a potential privacy breach, including an EHR access audit to determine whether such access occurred," AHIMA writes. "Such investigations, once completed, are generally performed to the satisfaction of the patient."
CHIME offers similar observations in its comments, saying that its members say requests for a true accounting of disclosures "are very few."
Rather, CHIME says, "patients will ask ... who touched or has seen their PHI and may request their entire record. What is often misunderstood by patients is they are not getting an accounting which involves treatment, payment or healthcare operations. The majority of requests, therefore, are not true AODs. Many members report getting requests from patients about who snooped into their record."
CHIME notes that "there is confusion ... around what a provider is required to release under an AOD and that more education from OCR would be helpful. Even among our members, it appears the understanding of what constitutes a true AOD is misunderstood."
Aligning Regulations
Some commenters, including the AHA, urge HHS to better align various federal privacy regulations, most notably 42 CFR Part 2 - which covers federally assisted substance abuse programs - with HIPAA privacy regulations.
"Applying the same requirements to all patient information - whether behavioral or medically related - would support the appropriate information sharing essential for clinical care coordination and population health improvement in today's patient care environment, where behavioral and medical health care are integrated to produce the best outcomes for all patients," AHA writes.
"The separate privacy structure under 42 CFR Part 2 creates challenges for the integration of behavioral and physical health care simply because patient data related to behavioral health cannot be handled like all other health care data."
CHIME offers similar comments. "There are growing challenges faced by providers and their business associates as more information is exchanged electronically as they must navigate a complex regulatory and legal landscape," CHIME writes.
"Providers must wrestle with myriad state laws coupled with the different consent policies associated with mental health and substance abuse rules under 42 CFR Part 2, making the electronic exchange of this information very challenging. Complicating matters is segmenting sensitive data within EHRs remains very challenging."
More Transparency?
But not all the industry groups submitting comments suggest that HHS ease up on various privacy or breach requirements.
Patient privacy advocacy group, Citizens' Council for Health Freedom, suggests that potential changes to HIPAA should offer patients more transparency about how their health data is allowed to be disclosed.
"HIPAA's primary focus is not privacy; it is security of the data before, after and while patient's privacy is being violated, which is what happens when the patient's data is disclosed and used without the patient's consent," CCHF writes.
"We support the right of patients to keep their private medical information confidential. Thus, we have long opposed HIPAA due to its intrusion on the patient-doctor relationship and its infringement of privacy rights," CCHF says. "Our opposition continues today and has only grown with the EHR mandate, health information exchanges ... and interoperability mandates."



 The first Wendy's restaurant in Columbus, Ohio (Photo: Wendy's)
The first Wendy's restaurant in Columbus, Ohio (Photo: Wendy's)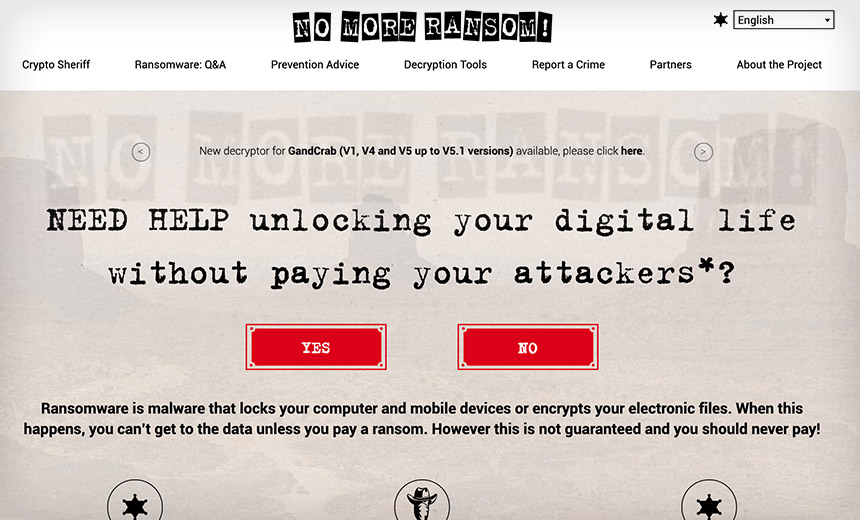 A new, free decryptor available via No More Ransom will unlock systems infected with GandCrab, up to version 5.1
A new, free decryptor available via No More Ransom will unlock systems infected with GandCrab, up to version 5.1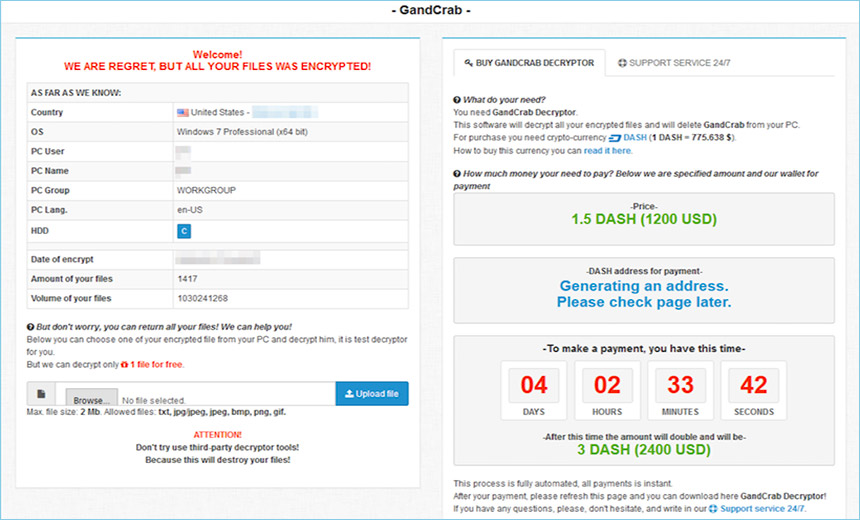 A GandCrab ransom-payment page, reachable only via a hidden TOR site (Source:
A GandCrab ransom-payment page, reachable only via a hidden TOR site (Source: 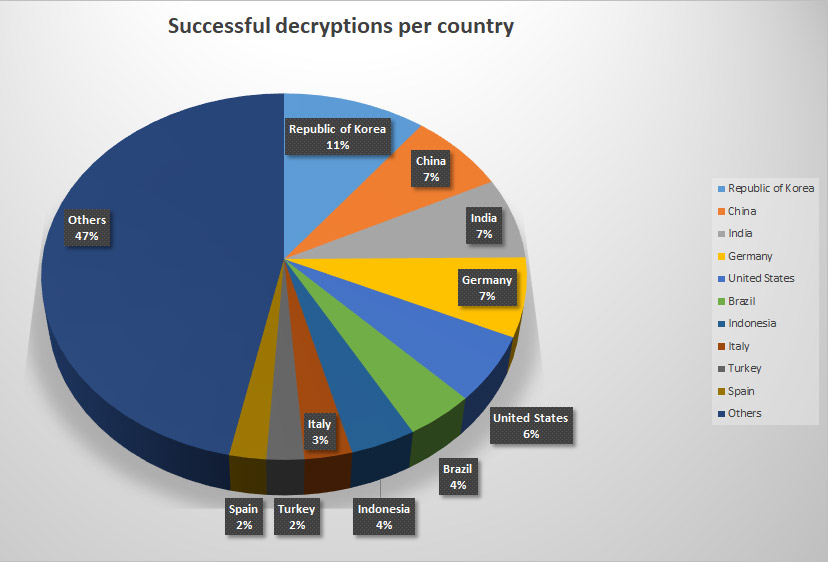 Successful GandCrab decryptions prior to Feb. 19, 2019 (Source: BitDefender)
Successful GandCrab decryptions prior to Feb. 19, 2019 (Source: BitDefender) The Australian Parliament Building in Canberra (Photo:
The Australian Parliament Building in Canberra (Photo:  Tom Uren
Tom Uren Four Iranian men along with a former Air Force servicewoman were charged in a hacking scheme that targeted military members. (Source: FBI)
Four Iranian men along with a former Air Force servicewoman were charged in a hacking scheme that targeted military members. (Source: FBI)


