Anti-Fraud
,
Business Email Compromise (BEC)
,
Cybercrime
Don't Fall for Fraudsters or You'll Be Poor and Brokenhearted Too(
euroinfosec) •
February 14, 2019
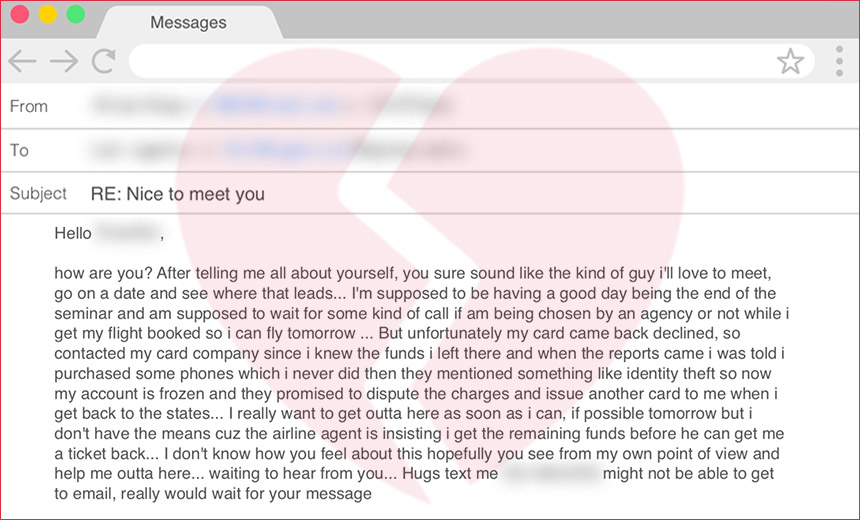
Source: Agari
This Valentine's Day, authorities are once again warning individuals to watch out for anyone perpetrating romance scams.
See Also: Live Webinar: Building Secure Delivery Pipelines with Docker, Kubernetes, and Trend Micro
Such "fauxmance" often takes the form of fraudster Romeos and Juliets, many of whom are operating from West Africa or Eastern Europe. Email security firm Agari, based in San Mateo, California, says names commonly assumed by scammers include Laura Cahill, Britney Parkwell, Lisa Frankel and U.S. Army Captain Starling Michael.
Romance scams typically start with the promise of companionship or romance, always leading to a demand for one thing. "We're talking about people you meet online, who lavish you with attention ... and then ask for money," the Federal Trade Commission says in a romance scam advisory. "Usually they want the money by wire transfer or gift card. They might claim they need it for a medical emergency or to come visit you. Then they take your money, but there's no surgery and no trip," only heartache.
"There are many romance scams out there, and the psychology of it is exploitation of feelings," says Alex Holden, CISO of Hold Security, an information security and incident response firm based in Wisconsin.
Many social engineering attacks use one of six "influencing levers," which are techniques for influencing the subconscious defined by psychologist Robert Cialdini. Raj Samani, chief scientist at security firm McAfee, says romance scams hit many of these levers: getting targets to like the social engineer, appealing to something being in short supply and exploiting victims' propensity to stick to any decision they've made.
International Affair
Romance scams and their cousin, business email compromise schemes, have been growing more sophisticated. "Many of the classic scams, such as technical support scams, advanced fee fraud and romance scams, still result in a considerable numbers of victims," the EU's law enforcement intelligence agency, Europol, says in its Internet Organized Crime Threat Assessment for 2018 (see: Cybercrime: 15 Top Threats and Trends).
As with so many online scams, criminals target victims around the world. In the U.S., women over the age of 40 are frequent targets.
"West African romance scams are straightforward, targeting older women by creating an artificial attraction and then playing on emotions from love all the way down to blackmail," Holden says. Having investigated some romance scams and worked with real victims, he says that "the effects are devastating psychologically."
Compared to fraudsters operating from West Africa, Eastern Europeans' approach appears to be more no less ruthless, but more industrialized. "While their African counterparts are not afraid to be on camera or on the phone, Eastern Europeans are mastering fraud by pretending to be attractive females - and lately gay young men," Holden says. "They have extensive manuals for endearment and abuse, templates on how to approach a victim and keep them enticed, images taken from professional models who are in on the scam, videos of the same young ladies, phone centers who will make a call to anyone, and even extensive techniques to leach money from the victims."
These are not isolated enterprises. Holden says some romance scammers also appear to be closely associated with crimes involving abuse and human trafficking.
Booming Business
Americans lost $143 million to romance scams in 2017, with each incident resulting in an average loss of $2,600, although victims over the age of 70 lost $10,000 on average, the FTC says. The Better Business Bureau estimates that since 2015, U.S. and Canadian victims' romance scam losses have reached nearly $1 billion.
Action Fraud, which is the U.K.'s national reporting center for fraud and cybercrime, says British victims filed 4,555 romance fraud reports in 2018, claiming total losses of more than £50 million ($64 million).
Social-engineering attacks appear to be popular with criminals because they're simple and effective. "Hacking people is easier than hacking technology," says Chris Morales, head of security analytics at Vectra, a San Jose, California-based threat detection and response firm. "Why break into a user's digital bank account when you can just have them send you the money? Why hack a password when you can just call a user and have them give you the password instead? Social engineering is by the far the most successful method to compromise a user or organization."

Source: CyberScout
One crime group, dubbed "Scarlet Window" by Agari, is based in Nigeria and registers dozens of different identities on dating sites large and small.
"While they hit the popular dating sites like Match, eHarmony, and OKCupid, the group also targeted relationship seekers on more specialized sites, such as Dating4Disabled.com, Farmers Dating Site and DivorcedPeopleMeet.com," according to a report from Agari. "Farmers in rural areas and people with disabilities are at higher risk of isolation and loneliness, making them especially vulnerable targets."
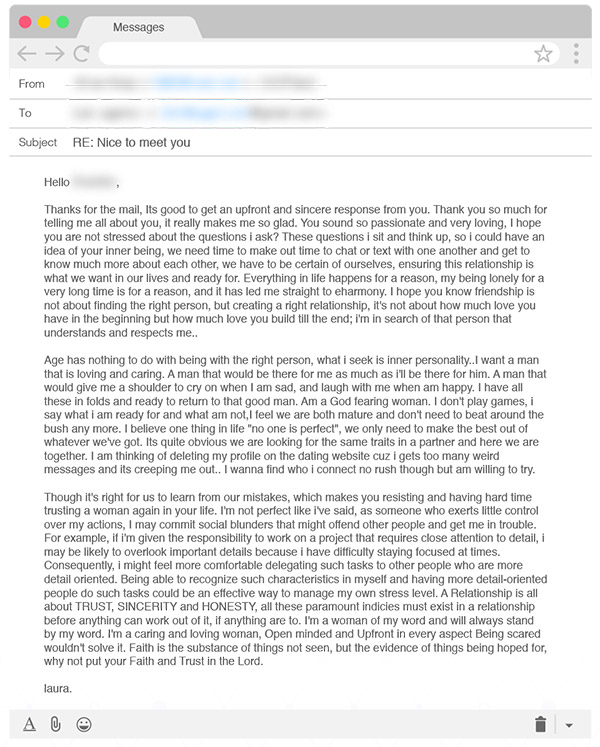
Example of a "Laura Cahill" email template used with a romance scam target (Source: Agari)
The group's more successful scams appear to have made a connection with victims via religion. "It is clearly an area the group actively tries to exploit," Agari says. "This is likely one way to test willingness to fall for the scam, and a way to build connection and trust with religious-minded victims."
Busting Bad Romeos and Juliets
Authorities continue to battle scammers via cross-border operations (see: Churchgoing Nigerians Drive Business Email Attacks).
Ronayerin K. Ogolor, 49, a naturalized U.S. citizen from Nigeria, was charged with one count of conspiracy to commit wire fraud in a criminal complaint filed in Missouri federal court in October 2018. Ogolor has been accused of running romance scams since 2014, often targeting elderly people in search of either romance or companionship via sites such as Facebook, ChristianMingle.com and Hangout.com.
"One victim - a widow in Indiana who received a friend request on Facebook - believed a co-conspirator was a widower working on an oil rig off the coast of Louisiana; she sent a total of $450,000 to Ogolor," the Department of Justice said. "Another victim in Texas, who believed a co-conspirator was a widower and U.S. Army general deployed in Afghanistan, lost at least $300,000."
In June 2018, an international investigation - dubbed Operation Wire Wire, targeting business email compromise and romance scammers who received funds via wire transfers - resulted in 74 arrests - many in the U.S., a few across Canada, Mauritius and Poland, as well as 29 in Nigeria.
Separately, in 2017, a U.S. judge sentenced three Nigerian nationals to lengthy prison terms. During a three-week jury trial after being extradited to the U.S. from South Africa in 2015, the men were convicted of numerous crimes, including identity theft, payment card fraud and romance scams.

Rasaq Raheem, Oladimeji Seun Ayelotan and Femi Alexander Mewase (Photos: Department of Justice)
Prosecutors told the court that the three men - Rasaq Aderoju Raheem, Oladimeji Seun Ayelotan and Femi Alexander Mewase - would allegedly often pretend to be European women to establish a romantic relationship with victims, often to trick them into serving as money mules for the gang or on behalf of others (see: Don't Be a Money Mule for the Holidays).
Money Mule Recruitment
The FBI says crime gangs often recruit money mules or use "work at home scams" to move money and make it more difficult for investigators to unravel their operations.
In August 2016, Interpol and the Nigerian Economic and Financial Crime Commission announced the arrest of "Mike," a 40-year-old Nigerian man accused of being tied to $60 million in fraud. Together with a 38-year-old alleged accomplice, Mike was arrested in the southern Nigerian city of Port Harcourt, thanks to a tip to Interpol from security firm Trend Micro.
A digital forensic review of devices seized when Mike was arrested revealed that he was involved in numerous business email compromise and romance scams, authorities said. "Heading a network of at least 40 individuals across Nigeria, Malaysia and South Africa, which both provided malware and carried out the frauds, the alleged mastermind also had money laundering contacts in China, Europe and the U.S. who provided bank account details for the illicit cash flow," Interpol and EFCC said in a joint statement.
Hacking the User
Despite such arrests, as long as romance scams keep generating profits, criminals will keep playing Romeo or Juliet. "Social engineering attacks like this will continue to be used because of their high success rates and potential for larger financial payoffs. Granted, they're harder to setup and execute than, say, a standard phishing campaign or trying to run a ransomware scam, but the payoff makes it worthwhile," says Nathan Wenzler, senior director of cybersecurity at Moss Adams, a Seattle-based public accounting firm.
"Plus, as industries focus more and more on securing their networks, servers, databases and application, they're making it harder for the more traditional methods of cyberattack to work," Wenzler says. "Since attackers are operating, by and large, for financial gain, they're going to take the path of least resistance to attack. And more and more, that's now the users themselves, rather than the technology they use."


 Image copyright
Getty Images
Image copyright
Getty Images
 Source: Agari
Source: Agari Source: CyberScout
Source: CyberScout Example of a "Laura Cahill" email template used with a romance scam target (Source: Agari)
Example of a "Laura Cahill" email template used with a romance scam target (Source: Agari)
 Rasaq Raheem, Oladimeji Seun Ayelotan and Femi Alexander Mewase (Photos: Department of Justice)
Rasaq Raheem, Oladimeji Seun Ayelotan and Femi Alexander Mewase (Photos: Department of Justice) International Computer Science Institute
International Computer Science Institute
 Source: FBI
Source: FBI
 The four indicted Iranian men (Source: FBI)
The four indicted Iranian men (Source: FBI)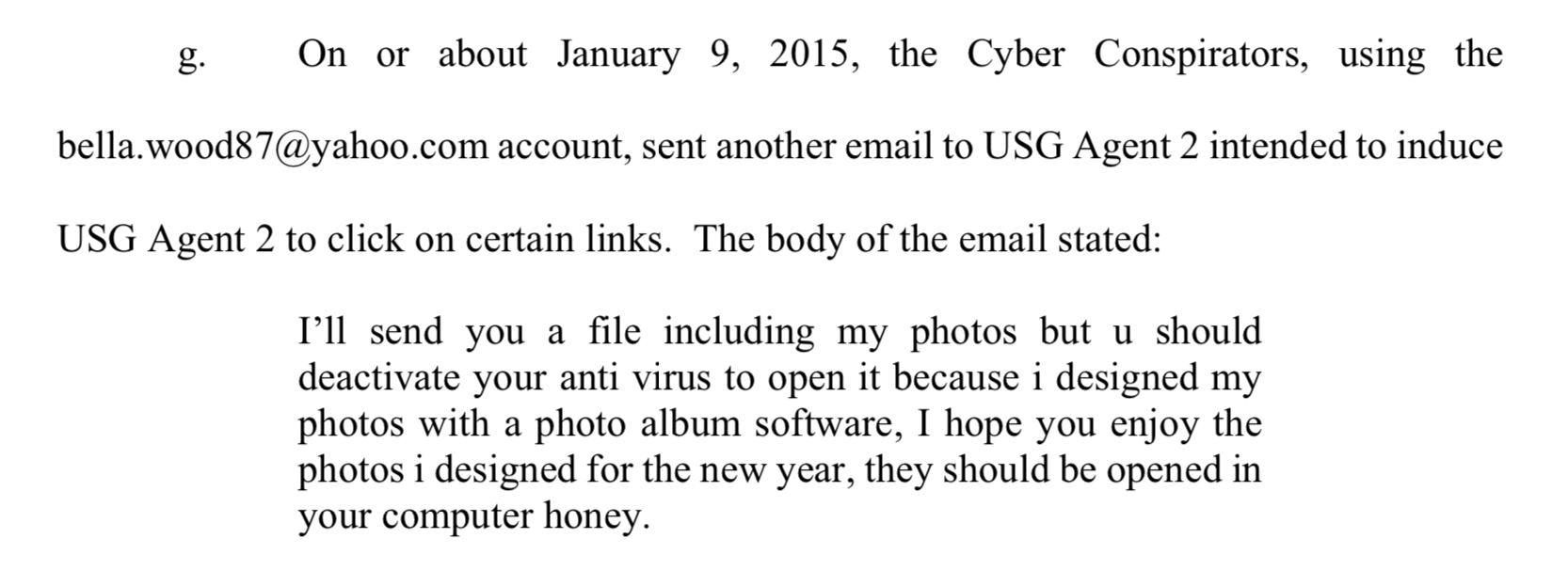 An excerpt from an email sent by "Bella Wood" to a U.S. government agent
An excerpt from an email sent by "Bella Wood" to a U.S. government agent
 Number of Facebook users in Asia (Source: Statista)
Number of Facebook users in Asia (Source: Statista)