Artificial Intelligence & Machine Learning
,
Breach Preparedness
,
Cybersecurity
A Rundown of the Conference's Top Emerging Topics(
HealthInfoSec)
•
February 15, 2019

Another HIMSS conference is in the rear-view mirror. But what's up the road in terms of top cybersecurity-related challenges facing the healthcare sector?
See Also: Live Webinar: Building Secure Delivery Pipelines with Docker, Kubernetes, and Trend Micro
Based on the variety of sessions that I attended and the many conversations I had with security leaders and regulators at HIMSS19, the consensus is that healthcare organizations still have a lot of work to do to ensure that patient information is kept private and secure.
Many hospital security leaders feel like their hands are tied in dealing with those growing medical device risks.
Cyberattacks in the healthcare sector are becoming more targeted and more profitable for hackers, said Rod Piechowski, senior director of health information systems at the Healthcare Information and Management Systems Society. That includes attacks involving social engineering, such as business email compromises.
But that's just the tip of the iceberg. Other growing concerns include nation-state attacks with a socio-economic impact, supply chain attacks, compromises related to the internet of things and data-in-motion attacks, said Axel Wirth, a solutions architect of Symantec.
And let's not forget about vulnerabilities of connected medical devices, especially the big gaps in security for those devices running legacy operating systems.
Many hospital security leaders feel like their hands are tied in dealing with those growing medical device risks. That's because penetration testing and network scans of medical devices present potential safety risks to patients if the gear malfunctions as a result.
And many of the older medical devices in service today aren't going to be retired anytime soon.
"It would cost of hundreds of millions of dollars for us to replace everything running Windows 7 or earlier operating systems," Kevin McDonald, director of clinical information security at the Mayo Clinic, told a HIMSS19 audience.
And even if big health systems like Mayo were able to replace all their older devices, the equipment would likely become smaller healthcare providers' problem. "Hand-me-down medical devices are very common," McDonald noted.
What Are the Answers?
When it comes to newer gear coming to market, healthcare entities need to muscle their influence early in the game, suggested Andy Sargent, director of product security at device maker Philips.
"Procurement is a good time to talk security," he told the HIMSS19 audience.
Also, having vendors provide a list of software and components included that are built into the medical devices can also help healthcare entities. Mayo compares lists of key device components and software to a national vulnerabilities database to help keep tabs on potential problems, McDonald said.
Indeed, the Food and Drug Administration, as well as a panel of federal advisers, are pushing for all medical device makers to provide bills of materials to their customers.
Technology Quest
When it comes to emerging security technologies that can help healthcare organizations address an array of worries - including breach detection, response and prevention - artificial intelligence and machine learning were among the hottest topics at HIMSS19.
"The biggest technology stacks we've been implementing are around optimizing our analytics, which includes behavioral analytics, event management platforms [that are] tightly integrated into the process - making sure that people, process and technology are fully implemented in the response strategy, Ron Mehring CISO at Texas Health Resources, told me in an interview.
But another hot technology - blockchain - also holds promise for applications and processes ranging from supply chain management to health information exchange.
Mitch Parker, CISO at Indiana University Health, told me his organization is testing blockchain in hopes of rolling out new applications for security soon.
Regulator Activity
Despite the Trump administration's deregulatory mantra, the healthcare sector likely faces several new regulations as well as ramped-up enforcement activities.
On Feb. 11, two Department of Health and Human Services agencies - the Office of the National Coordinator for Health IT and the Centers for Medicare and Medicaid Services - issued proposed rules that deal with prohibiting the blocking of secure information exchange plus a number of other issues, including improving patients' access to their health records.
At a HIMSS19 press briefing, CMS Administrator Seema Verma said that under the proposals, regulators will "out" organizations that don't play by the new rules prohibiting information blocking.
"We want patients at the center of the healthcare system, and we want to make sure they have all the tools they need to make the decisions that work best for them," she said.
CMS' proposals include a provision to "publicly report the names of clinicians and hospitals who submit a 'no' response to certain attestation statements" about whether they pledge not to engage in information blocking.
When I asked Verma whether HHS' plans to publicly report information blocking offenders might take a road similar to the Office for Civil Right's "wall of shame" website listing health data breaches, she said: "Sure, I think all of that is appropriate. We're trying to use our authority under a penalty program and/or incentive program. ... So for hospitals not to be penalized, and for providers to get incentives, they're payment is tied to how they are performing around interoperability."
Under the 21st Cures Act, which led to the proposed new regulations, "interoperability" refers to "technology that enables the secure exchange of electronic health information with, and use of electronic health information from, other health IT without special effort on the part of the user."
HIPAA Enforcement
The federal government's HIPAA enforcement agency - the HHS Office for Civil Rights - also plans to keep a close eye on whether covered entities and business associates toe the line.
OCR will take enforcement action against those organizations that have "a culture of noncompliance and total disregard for the duty of care that is owed to protecting individuals' protected health information," Nick Heesters, OCR health information privacy and security specialist, told me in an interview.
Clearly, healthcare organizations have a long list of security-related obstacles, obligations and opportunities to navigate.


 If Facebook can't reach a penalty agreement with the FTC, the regulator could take the case to court and call on senior executives, such as CEO Mark Zuckerberg (pictured), to testify.
If Facebook can't reach a penalty agreement with the FTC, the regulator could take the case to court and call on senior executives, such as CEO Mark Zuckerberg (pictured), to testify. Marcus Hutchins, pictured on July 26, 2017, while attending the Black Hat conference in Las Vegas. (Photo:
Marcus Hutchins, pictured on July 26, 2017, while attending the Black Hat conference in Las Vegas. (Photo: 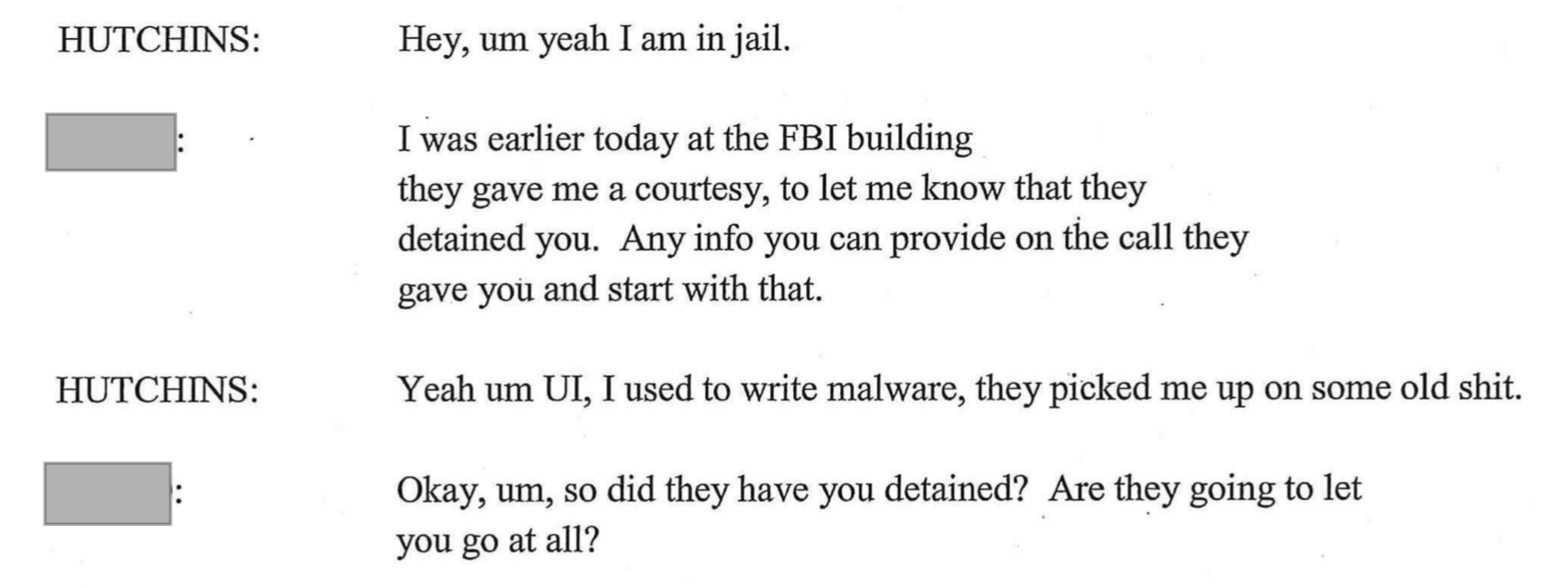 An excerpt from a phone call Hutchins made following his arrest in August 2017
An excerpt from a phone call Hutchins made following his arrest in August 2017
