Data Breach
LinkedIn Sale: Mega Bucks, No Matter Mega Breach
Do Consumers Really Defect From Breached Businesses?
Mathew J. Schwartz
(euroinfosec)
•
June 14, 2016

All in the Microsoft family (from left): LinkedIn CEO Jeff Weiner, Microsoft CEO Satya Nadella and LinkedIn Executive Chairman Reid Hoffman. (Source: Microsoft)
My initial reaction to Microsoft's announcement that it plans to buy LinkedIn for $26.2 billion in cash: I guess that massive 2012 data breach didn't hobble the company's prospects (see LinkedIn's Password Fail).
See Also: From Authentication to Advanced Attack Vectors: Top Trends in Cybercrime in Q1 2016
That's relevant because one oft-repeated breach bromide - regularly trotted out via vendors' surveys of customers' self-reported perceptions - is that consumers will defect from breached businesses. The warning is meant to be a cautionary note to all organizations: Get your security house in order, or else you might lose customers.
"The only businesses that seem to take an irreversible hit from breaches are the ones that get driven out of business."
The sentiment is worthwhile. As a consumer, I want the organizations that I choose to do business with - or in the case of LinkedIn, the service I choose to use in exchange for however the site is monetizing my personal information and professional connections - to protect my information.
But it's clear that when businesses get breached, consumers might cry foul, although it's unlikely that they're going to go elsewhere.
Kansas Heart Hospital suffered a ransomware infection last month, for example, but chances are that if you're living in the Wichita area and planned to get a heart procedure done there prior to the attack, you're not going to let a little malware get in the way.
Switching bank accounts, too, is such a pain that few users actually do so, even when their bank suffers a breach.
Target Users Switched to Cash
On the retail and restaurant front, big-named breached businesses include P.F. Chang's, Wendy's as well as Target. In the wake of Target's 2013 mega-breach and reports of stolen payment card data, the reaction from many consumers was that they would continue to shop at Target, but pay cash. Likewise, even though Zappos suffered a massive 2012 breach that revealed substandard password practices, has a single person ever decided, based on that breach, to not buy a pair of shoes from the online retailer?
Meanwhile, TalkTalk suffered three separate breaches in 2015, but CEO Dido Harding remains at the helm, thus suggesting that however bad the hack attacks were, despite the loss of 100,000 customers following the October breach, and the company's stock price since then losing a third of its value, the board of directors still has faith in Harding.
Here's how @TalkTalk stock has performed on London exchange before/after Oct. 2015 breach. (Source: Google Finance) pic.twitter.com/FN05FLDvsL
In fact, the only businesses that seem to take an irreversible hit from breaches are the ones that get driven out of business, such as DigiNotar, a certificate authority that issued bad certificates in 2011; Code Spaces, which had its cloud-based data overwritten by attackers in 2014; or any number of bitcoin exchanges. But none of those were brand names or failed due to customer defections.
After 2012 Breach, LinkedIn Thrives
That's a relevant discussion when it comes to LinkedIn. While its data breach came to light four years ago, it's been in the limelight in recent weeks thanks to the paid breach-notification service LeakedSource getting its hands on 165 million LinkedIn credentials. LinkedIn was always mum about the 2012 breach, and never commented on whether it involved just the credentials related to 6.5 million password hashes that got posted to an underground password forum by a hacker who was seeking help in cracking them.
Looking back, it's likely that LinkedIn, which didn't have a CISO at the time - but quickly got one - did not know that hackers had stolen what appears to be almost every LinkedIn user's credentials. But whatever LinkedIn did - or did not - know, it chose to only reset the credentials associated with 6.5 million accounts. Four years later, of course, that looks to have been a really bad move.
Unfortunately, LinkedIn wasn't an outlier, exactly, as a number of other big-name firms had also been hacked and their poorly secured user credentials stolen (see 'Historical Mega Breaches' Continue: Tumblr Hacked).
LinkedIn + Microsoft = ?
Back to the LinkedIn acquisition. Microsoft CEO Satya Nadella says he expects the deal to close later this year, and that the combined companies "can accelerate the growth of LinkedIn, as well as Microsoft Office 365 and Dynamics as we seek to empower every person and organization on the planet."
Reading between the empowerment lines, the deal appears to be an attempt to make Microsoft's online collaboration environment "stickier," although Sean Sullivan, a security adviser at Finnish security firm F-Secure, warns that there can be related downsides. "In the short run, I'd raise the concern that tighter integration between LinkedIn, Skype and Exchange/OneDrive could open up new vectors for business email fraud," he tells me, highlighting the potential for "CFO impersonation via Skype for Business, rather than via email."
One recent banking malware campaign, for example, used LinkedIn information to personalize emails sent to phishing targets, according to information security firm Fox-IT. Hence, in the post-Microsoft LinkedIn regime, "hopefully it all ties together well in a way that makes it easy to tell outsiders from insiders," he says.
A big impetus for this deal also appears to be to give a boost to the Microsoft Dynamics software, which by many estimates plays fourth fiddle - after salesforce.com, SAP and Oracle - in the customer relationship management software market.
In fact, given the price being offered by Microsoft - 50 percent more than the company's share price was worth - I'd bet that one of these CRM competitors was sniffing around LinkedIn too.
From a security standpoint, that's not a bad turn for a company that managed to lose virtually all of its users' access credentials just four years ago.



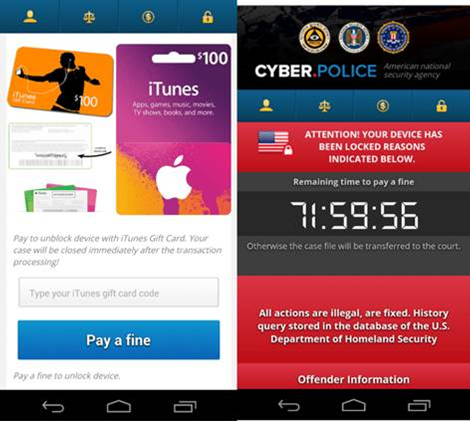 FLocker - Android malware's ransom page. (Source: Trend Micro)
FLocker - Android malware's ransom page. (Source: Trend Micro) All in the Microsoft family (from left): LinkedIn CEO Jeff Weiner, Microsoft CEO Satya Nadella and LinkedIn Executive Chairman Reid Hoffman. (Source: Microsoft)
All in the Microsoft family (from left): LinkedIn CEO Jeff Weiner, Microsoft CEO Satya Nadella and LinkedIn Executive Chairman Reid Hoffman. (Source: Microsoft)
 Decoy "china.pdf" file fed to Operation Daybreak victims by APT attack group "ScarCruft." (Source: Kaspersky Lab.)
Decoy "china.pdf" file fed to Operation Daybreak victims by APT attack group "ScarCruft." (Source: Kaspersky Lab.)