Fraud
,
Phishing
Experts Say Alert Over $3.1 Billion in Losses Is Late, Offers Little Advice
Jeremy Kirk (jeremy_kirk) ,
Tracy Kitten (FraudBlogger) •
June 17, 2016

The Federal Bureau of Investigation is now warning U.S. businesses of a new type of business email compromise scam, a.k.a. CEO fraud, that takes aim at personally identifiable information, rather than simply tricking accounting staff into scheduling fraudulent wire transfers.
See Also: How to Illuminate Data Risk to Avoid Financial Shocks
Additionally, the FBI has revised its tally of losses attributed to BEC attacks once again, putting worldwide fraud losses at more than $3 billion through the end of May. Just two months earlier, the agency said $2.3 billion had been lost to these scams between October 2013 and February 2016. Less than a year ago, it said losses were around $1 billion.
"Since January 2015, there has been a 1,300 percent increase in identified exposed losses," the FBI states. "The scam has been reported by victims in all 50 states and in 100 countries."
But in its June 14 public service announcement about the shifting focus of BEC attacks, the FBI notes that hacked email accounts linked to executives are now also being used to request personally identifiable information and W-2 tax forms from human resources and auditing departments.
Targeting PII was first seen earlier this year, prior to U.S. tax season, the FBI adds.
Email Authentication Won't Reduce Risk
To mitigate emerging risks, the FBI suggests companies implement two-factor authentication for email, which requires password entry and use of a dynamic PIN or code to log in to the email account.
"TFA [two-factor authentication] mitigates the threat of a subject gaining access to an employee's email account through a compromised password," the FBI says.
But experts say dual-factor authentication for email is not going to mitigate risks associated with BEC attacks, regardless of whether the attackers are after PII or want to schedule fraudulent wires. Because most BEC attacks are waged via spoofed, not compromised, email accounts, two-factor authentication will not mitigate risk, they contend.
"The majority of BEC attacks do not involve stealing the email password of executives," says Dave Jevans, vice president of mobile security at cyberthreat defense firm Proofpoint and chairman of the Anti-Phishing Working Group, a global coalition focused on unifying response to cybercrime. "BEC attacks involve sophisticated email spoofing. Two-factor authentication on the email of executives won't do much to solve this problem, and almost nobody has implemented 2FA on corporate email."
Rather than dual-factor authentication for email, companies should implement DMARC - Domain-based Message Authentication, Reporting & Conformance, which standardizes how email recipients authenticate emails through a uniform reporting mechanism, says Tom Kellermann, CEO of Strategic Cyber Ventures, a cybersecurity technologies investment firm.
"Businesses should mandate the use of DMARC and also require secondary, out-of-band authentication, like a text message or phone call, to validate a request for information or a transfer of funds," he says.
Bill Nelson, president and CEO of the Financial Services Information Sharing and Analysis Center, says companies also should enhance email security by using cryptographic techniques to secure emails. But Nelson agrees email authentication is not the answer.
"Financial institutions and their corporate customers can do a lot more to filter email and make sure that phishing emails don't get through," he says. "But in the case of BEC, we aren't talking about phishing; these are spoofed emails. I don't know that doing some sort of authentication of the email would help in that case. Verifying the legitimacy of the user would help. And if it is a spoofed email and not coming from the address of the executive or the business, then that is something that you should be able to detect in your email filtering system."
And in terms of reducing phishing, Nelson says most banking institutions and businesses are having more success mitigating their risks through employee education rather than technology.
At the end of the day, Nelson says the best way to reduce risk is to eliminate email approval for wire transfers and requests for PII.
Warning Comes A Little Late
Financial fraud expert Shirley Inscoe, an analyst at consultancy Aite, says there's really nothing new about the attacks the FBI references in its most recent alert.
"I've been hearing about it throughout 2016," she says. "I'm surprised it took the FBI so long to issue an alert, as this really does allow major access to PII data by crime rings. They will add this information to their massive databases, and match it up with payment card information from previous data breaches when possible."
Hackers also use PII data to perpetrate tax fraud, Jevans and Nelson say, which also is nothing new.
"Stealing of PII is so that scammers can file fake tax returns before the actual person does, and they can claim a refund," Jevans says. And if criminals file the fake tax returns through a tax preparation company or service, then they can have their refunds issued on debit cards - which means instant cash, he adds.
"They are using that PII for tax return fraud," Nelson agrees. "We heard about it last year, and most states are getting hit hard; they already sent a tax refund to someone that is clearly fraudulent. Now they have to clean it up."
But Inscoe says the industry should be worried about more than just tax fraud, especially since hackers are increasingly targeting PII through a number of different methods. "Access to this data will also make it simpler to commit identity theft and to impersonate customers when calling into contact centers. When they can do so successfully, they can get online credentials reset, order additional cards on accounts or obtain some other access device to commit financial fraud. Money is always the ultimate goal, whether it is to fund terrorism or just the product of greed."
Inscoe says businesses that fall victim to these types of BEC attacks must contact their banking institutions immediately, to ensure that employee bank accounts can be monitored for suspicious activity. "While most FIs [financial institutions] won't issue new cards due to the breach of PII, they can monitor the accounts of the employees whose data was breached more closely, place alerts on the accounts and take more care when asked to reset credentials or issue new cards," she says.
Not Technically Sophisticated
The schemes have stung countless companies. Attackers impersonate key executives or financial personal in companies and send emails to others in the organization ordering large wire transfers. (see Business Email Compromise: How Big Is the Problem?).
The scam is not technically sophisticated, but rather relies on social engineering. The hackers collect email account credentials through phishing schemes and then begin monitoring how employees communicate. In other cases, emails are spoofed to appear to come from an organization.
"Most victims report using wire transfers as a common method of transferring funds for business purposes; however, some victims report using checks as a common method of payment," the FBI says. "The fraudsters will use the method most commonly associated with their victim's normal business practices."
In addition to email authentication, the FBI also suggests businesses invest in intrusion detection systems that are tuned to catch emails coming from spoofed domain names that closely resemble the businesses' legitimate domains.
The FBI also advises businesses to register domain names that are close to the actual company domain name.
And, as a final precaution, the FBI says significant transactions should always be verified over the phone, not over email alone.




 An alleged DNC background document dumped by Guccifer 2.0 (source: Gawker)
An alleged DNC background document dumped by Guccifer 2.0 (source: Gawker) Apple CEO Tim Cook addresses WWDC 2016. (Source: Apple)
Apple CEO Tim Cook addresses WWDC 2016. (Source: Apple)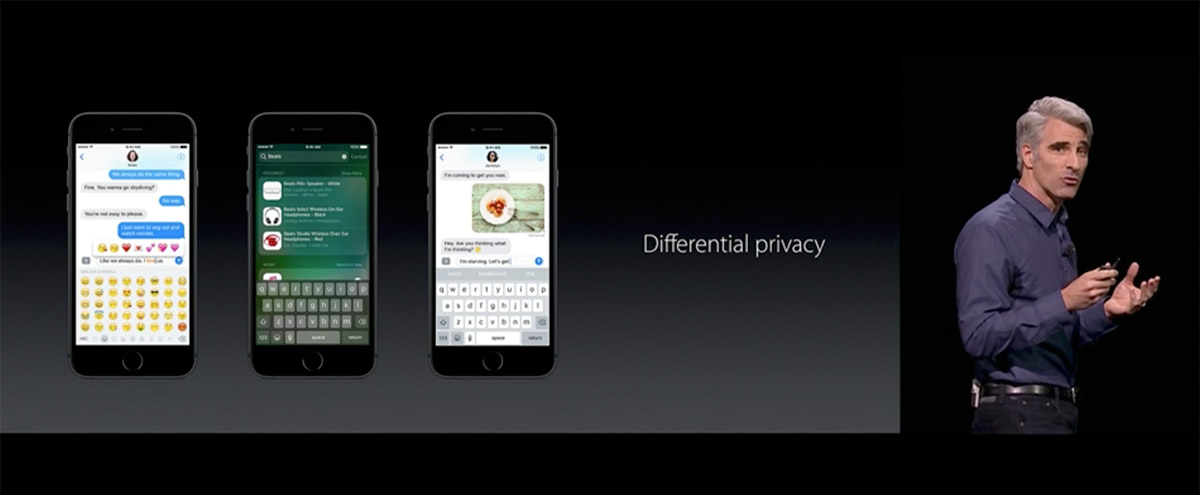 Craig Federighi, Apple's senior vice president of software engineering, talks differential privacy at WWDC 2016.
Craig Federighi, Apple's senior vice president of software engineering, talks differential privacy at WWDC 2016. London's Olympia exhibition center hosted this year's conference.
London's Olympia exhibition center hosted this year's conference. Opened as the National Agricultural Hall in 1886 - three years before the Eiffel Tower - the Olympia, located in London's Kensington district, features a wrought iron and glass shell.
Opened as the National Agricultural Hall in 1886 - three years before the Eiffel Tower - the Olympia, located in London's Kensington district, features a wrought iron and glass shell. The Olympia spans two levels, with the upper level hosting more than 100 exhibitors as well as the keynote presentations.
The Olympia spans two levels, with the upper level hosting more than 100 exhibitors as well as the keynote presentations. Mikko Hypponen, chief research officer of F-Secure, delivered an opening keynote presentation on
Mikko Hypponen, chief research officer of F-Secure, delivered an opening keynote presentation on  Nearly 350 organizations - from security vendors and consultancies to governmental organizations and professional associations - exhibited at this year's conference.
Nearly 350 organizations - from security vendors and consultancies to governmental organizations and professional associations - exhibited at this year's conference. Hot topics at this year's conference ranged from
Hot topics at this year's conference ranged from  The conference drew what organizers estimated to be more than 15,000 attendees, offering ample opportunities for not just free swag, but also networking.
The conference drew what organizers estimated to be more than 15,000 attendees, offering ample opportunities for not just free swag, but also networking. Vendors deployed the usual array of booth enticements to attract visitors, ranging from free lightsabers and notepads to the chance to win a drone or beat an opponent at a modified form of whack-a-mole (pictured).
Vendors deployed the usual array of booth enticements to attract visitors, ranging from free lightsabers and notepads to the chance to win a drone or beat an opponent at a modified form of whack-a-mole (pictured). With outside temperatures soaring in London, and the glass-roofed Olympia not offering state-of-the-art air conditioning, attendees snapped up cool freebies, ranging from beer at daily happy hours to ice cream and sorbet.
With outside temperatures soaring in London, and the glass-roofed Olympia not offering state-of-the-art air conditioning, attendees snapped up cool freebies, ranging from beer at daily happy hours to ice cream and sorbet. More than 260 speakers presented this year in keynote presentations, panel discussions as well as smaller technology talks.
More than 260 speakers presented this year in keynote presentations, panel discussions as well as smaller technology talks. Keynote presentations occasionally turned personal, for example, when Hypponen revealed that he too had been pwned in the
Keynote presentations occasionally turned personal, for example, when Hypponen revealed that he too had been pwned in the  Familiar symbology - as in this demonstration of an attack/defense training program offered by U.K. security firm Satisnet - featured heavily, if at times unsubtly, at the the conference.
Familiar symbology - as in this demonstration of an attack/defense training program offered by U.K. security firm Satisnet - featured heavily, if at times unsubtly, at the the conference. Only a handful of
Only a handful of  GAO's Greg Wilshusen calls on U.S. agencies to toughen access controls.
GAO's Greg Wilshusen calls on U.S. agencies to toughen access controls.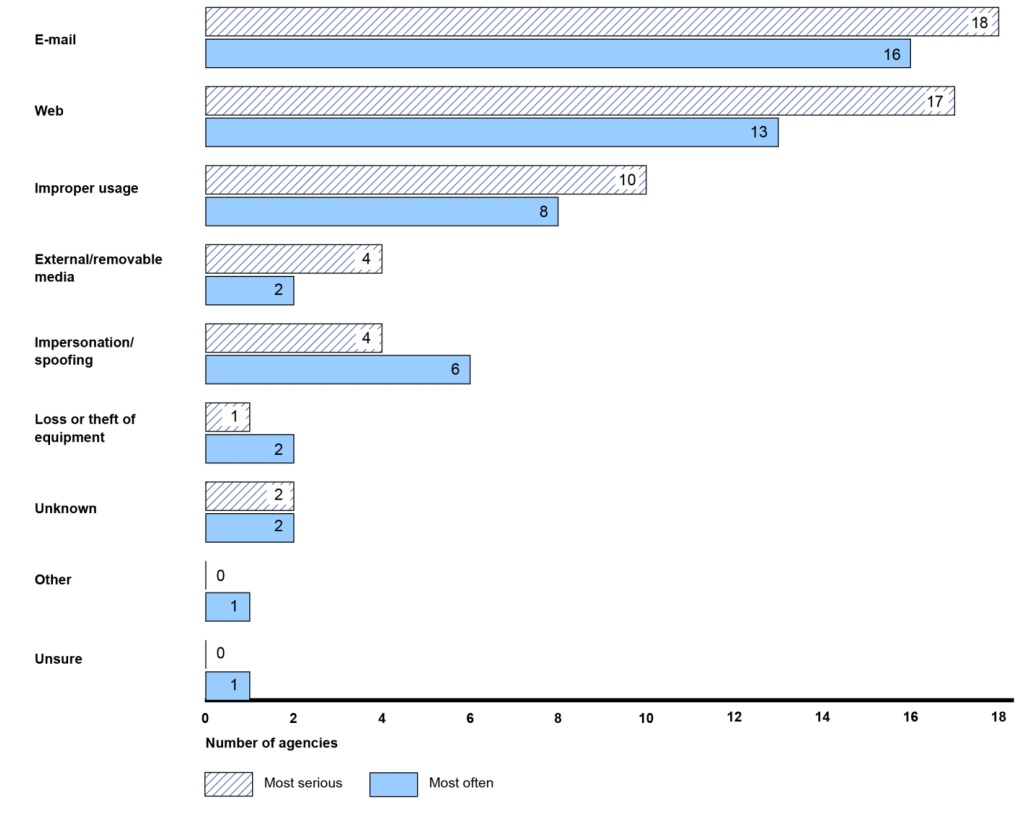 Source: GAO
Source: GAO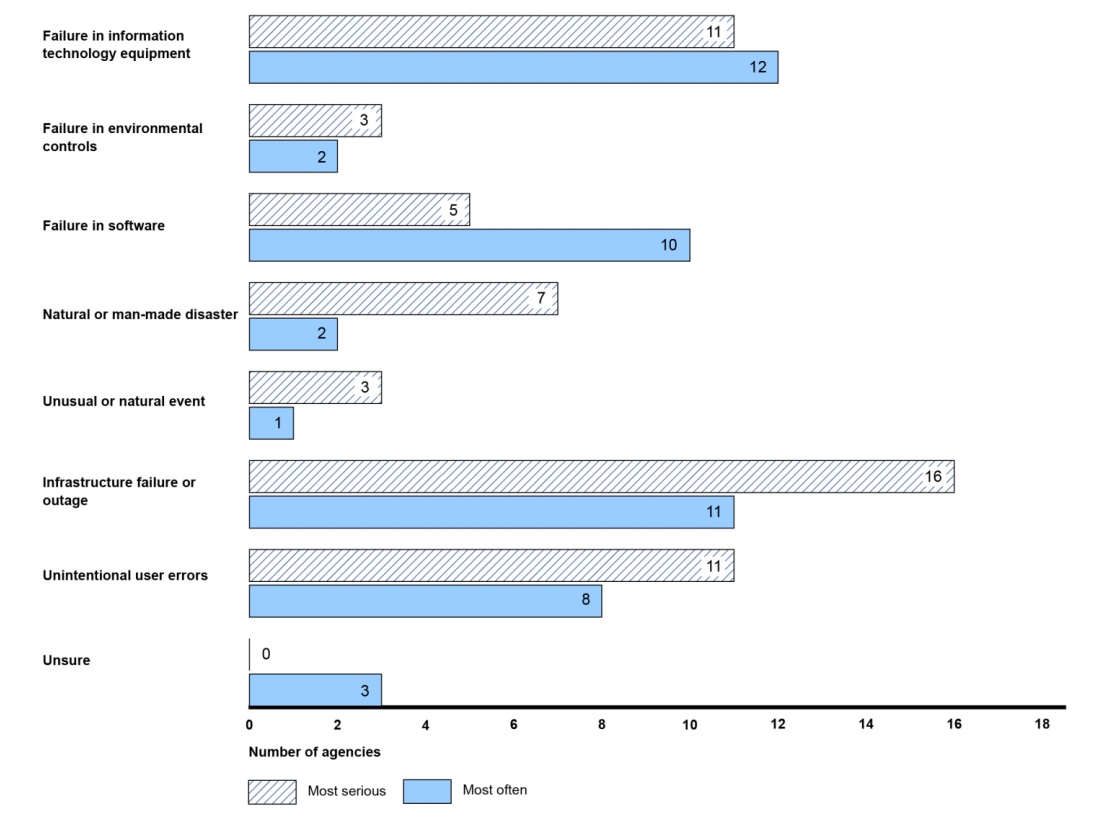 Source: GAO
Source: GAO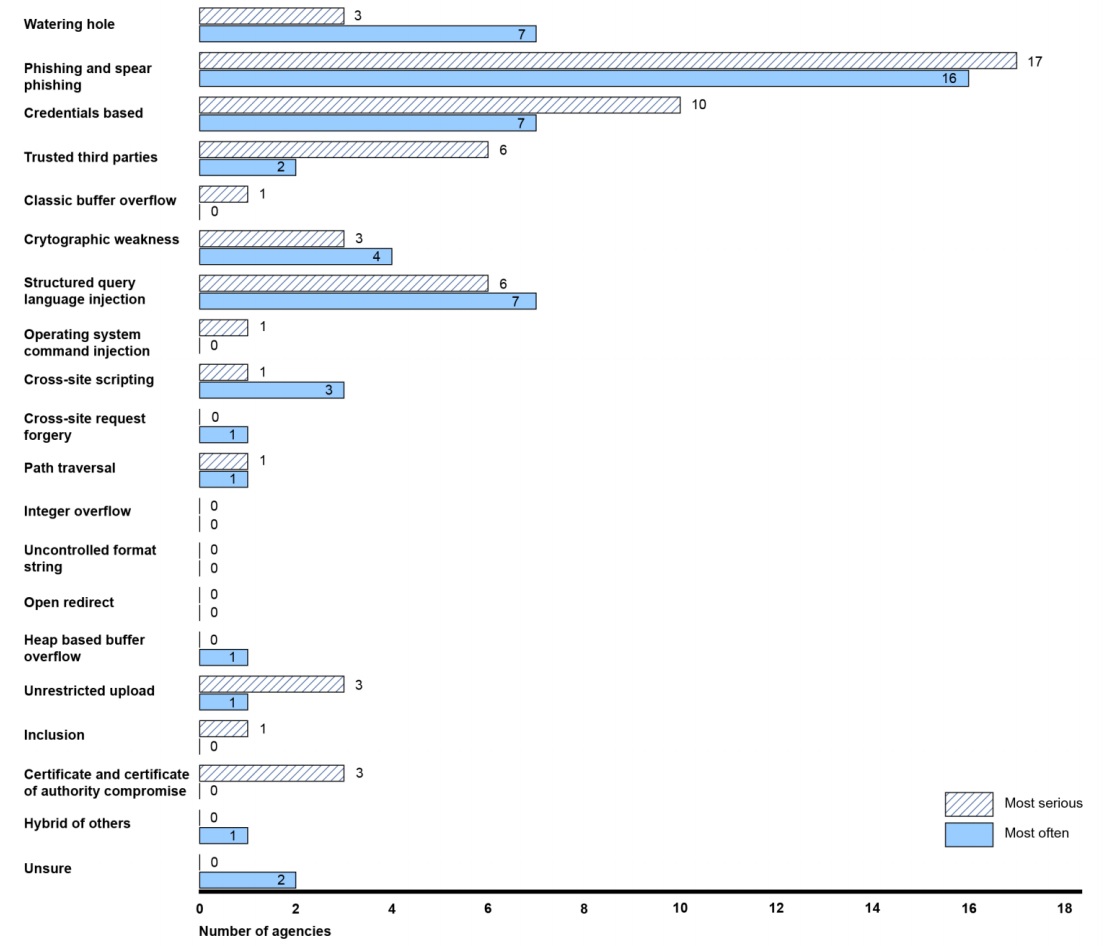 Source: GAO
Source: GAO