Anti-Malware , Encryption , Technology
Ransomware Attackers Unleash Feline-Themed Assault New Hitler-Themed Malware Deletes Files, While Android Victims See Cats Photo: Kishjar (via Flickr/CC)
Photo: Kishjar (via Flickr/CC)Without a doubt, ransomware attackers have no scruples.
See Also: How to Illuminate Data Risk to Avoid Financial Shocks
That should have already been obvious from gangs of cybercriminals who show no remorse when it comes to encrypting everything from electronic health records at hospitals, to PCs used by law enforcement agencies, to consumers' precious digital snaps. Gangs have even been creating customer-service teams in an attempt to maximize their illicit profits.
But the latest ransomware attacks go to even further extremes, channeling everything from kittens to Hitler.
New self-described Hitler-themed "ransonware" (sic) was discovered by Jakub Kroustek, a malware analyst at security firm AVG Technologies. The Hitler ransomware's lock screen demands that victims buy a €25 ($28) virtual Vodafone gift card and send attackers the redemption code.
The ransomware appears to be a test version that's not yet ready for primetime, Kroustek says via Twitter. "I guess it is still under 'development,' and this one has leaked," he says.
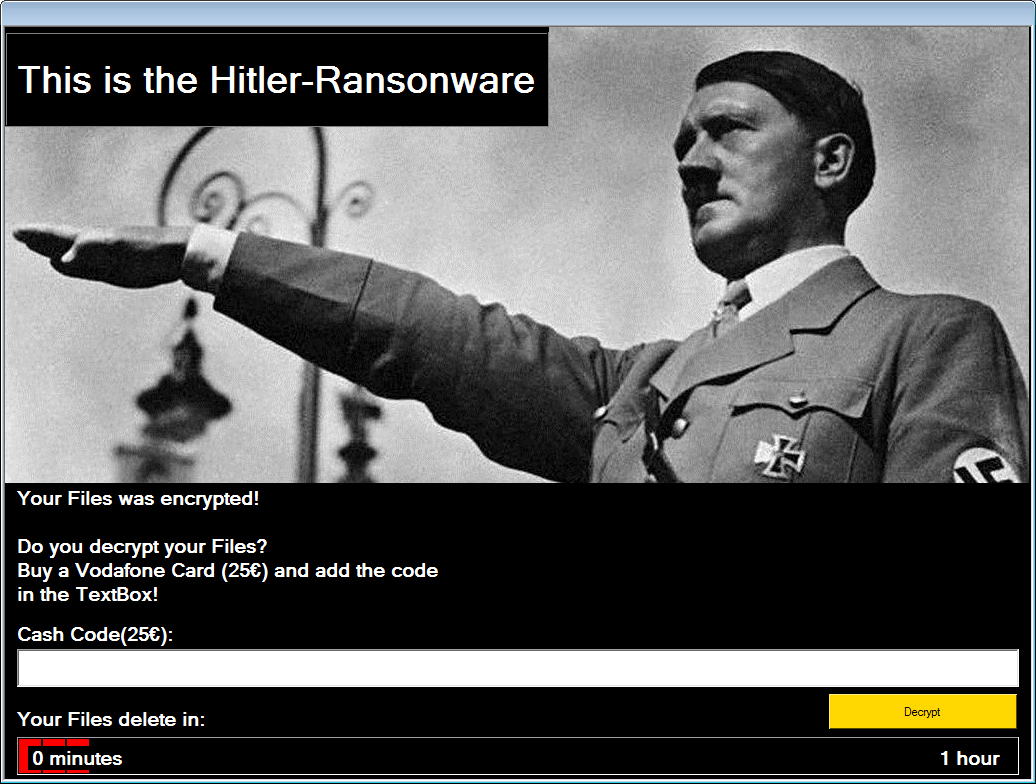 Hitler ransomware lock screen. Source: Bleeping Computer
Hitler ransomware lock screen. Source: Bleeping Computer
So far at least, the ransomware doesn't appear to have been designed to encrypt files. Instead it runs a batch file, which includes German-language comments from the apparent developer, that removes the extensions for certain file types stored in 11 different directories - ranging from a user's pictures and documents folders to their music and desktop directories - and then displays a lock screen with a one-hour countdown timer, according to a technical teardown published by anti-ransomware site Bleeping Computer. After the hour is up, it reports, the ransomware reboots the PC and runs an executable called "firefox32.exe" that deletes all of the files with excised filenames, while also terminating any processes - taskmgr, utilman, sethc, cmd - that a user might invoke to attempt to shut down the malicious file.
Such delete-everything behavior was seen earlier this year via a ransomware variant called Ranscam.
One potential defense against Hitler ransomware attacks, Bleeping Computer says, is to disable Windows automatically restarting after it crashes, which would give victims a chance to scrub their hard drive before the deletion routine starts.
Leave No Meme Behind
To date, ransomware attackers haven't paid too much attention to Android. That's no surprise: Cybercriminals often seem to prioritize attacks that generate maximum revenue for minimum effort, and thus most developers focus on coding Windows malware. With 10 percent of all PCs still running the outdated, insecure and often easy to hack Windows XP operating system, according to market researcher NetMarketShare, why bother creating cutting-edge malware designed to target the relatively small number of people - by comparison - who use Mac OS X, Linux, Android or iOS?
But some developers have been making forays into Android ransomware. One variant that first appeared last year, called FLocker - short for "frantic locker" - is now able to lock Android-powered mobile phones, tablets and smart TVs, demanding $200 worth of iTunes gift cards from victims to unlock infected devices, according to security firm Trend Micro.
Recently, another type of Android ransomware called "El Gato" - Spanish for cat - also debuted, Fernando Ruiz of Intel Security's McAfee Labs Mobile Malware Research Team says in a blog post.
El Gato packs typical malware tricks: it communicates with a command-and-control server to receive instructions, can disable any app that's running on the device as well as forward and delete any SMS messages stored on the device. But the malware can also send SMS messages to the victim, encrypt - or decrypt - all files stored on the device or on any inserted SD cards, as well as display a lock screen with a ransom demand that features a picture of a cat.
As with the Hitler ransomware, however, El Gato appears to be a work in progress, Ruiz says. For starters, the AES algorithm it uses to encrypt files features a hardcoded password, meaning that security researchers can use the app to decode anything that it's encrypted. More advanced forms of ransomware, by contrast, use a unique password for every different ransomware-infected system, making it much more difficult - if not impossible - for victims to decrypt files without paying the ransom (see Ransom Smackdown: Group Promises Decryption Tools).
Ruiz says the ransomware is likely under development and will likely be included in future exploit kits. Also known as cybercrime toolkits, developers sell these to cybercriminals, allowing them to automatically infect large numbers of PCs and - in this case - not only steal data but also attempt to extort victims into paying a ransom.
"This ransomware variant looks like a demo version," Ruiz says.
Lured by the promise of easy pickings, ransomware attacks are booming. As El Gato and the Hitler ransomware demonstrate, developers appear to be testing new ways to meet this ever-increasing demand.



 Northeastern University Professor Engin Kirda
Northeastern University Professor Engin Kirda

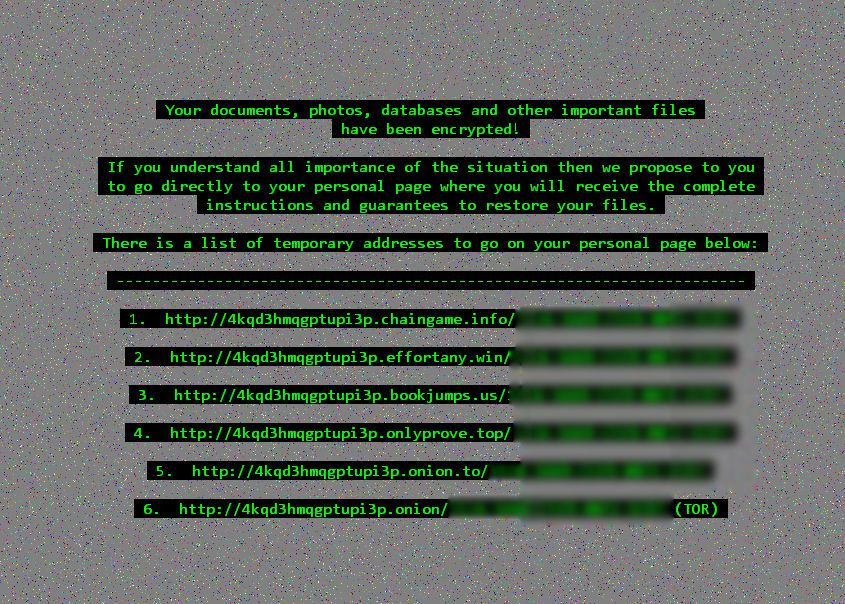 The ransom notice displayed by Cerber 2. Source: Bleeping Computer
The ransom notice displayed by Cerber 2. Source: Bleeping Computer