Data Loss
,
Network & Perimeter
,
Risk Management
Security Experts Outline Enterprise Defense Essentials
Mathew J. Schwartz (euroinfosec) •
August 24, 2016

The recent dump of attack tools linked to the Equation Group, which is widely believed to be tied to the U.S. National Security Agency and its Tailored Access Operations team, has triggered despair in technology circles (see NSA Pwned Cisco VPNs for 11 Years).
See Also: Top Trends in Cybercrime; 411 Million Attacks Detected in Just 3 Months
The thinking goes: If the NSA - and by extension any other top-flight intelligence agency - can develop attack tools to seemingly hack into almost any technology to gain access to networks, decrypt encrypted traffic and monitor targets, what hope do any organizations or individuals have that they can secure their data or systems?
As Jeff Pollard, a principal analyst focused on IT security at Forrester Research, told The Washington Post: "What is a company supposed to do when the very technology that they bought to protect them makes them vulnerable?"
Here are five takeaways from the Equation Group attack tool dump:
1. Intelligence Agencies Crave Exploits
The leak of Equation Group attack tools designed to exploit flaws in widely used software and hardware has once again prompted some information security researchers to demand that intelligence agencies such as the NSA and its sister British intelligence agency, GCHQ, promptly disclose such flaws to affected vendors. That's because the same flaw could have already been discovered by other intelligence agencies or cybercriminals.
"The question it really opens up is, 'Should NSA/GCHQ disclose the vulnerability so that manufacturers can close the hole?'" says Alan Woodward, a computer science professor at the University of Surrey. "In the past, GCHQ has done that. But it shows that these agencies have two roles: one is to gather intelligence via electronic means, and one is to keep us safe - a balance I don't envy them."
Many intelligence agencies, furthermore, actively search out these flaws, with the NSA reportedly sometimes hiring former employees from U.S. technology firms to help it reverse-engineer software and hardware.
That's why government vulnerability-sharing programs are "an exercise in optics," a.k.a. smoke and mirrors, says Michael Tanji, CSO of cybersecurity firm Kyrus - and a former U.S. Army signals intelligence analyst - in a blog post. "'Of course we'll cooperate with your vulnerability release program,' says every inter-agency representative. 'As long as it doesn't interfere with our mission,' they whisper."
But many related exploits aren't necessarily useful outside of intelligence circles. "One thing that is notable about many of these exploits is that they assume you are already inside the enterprise or have had access to the kit somewhere to taint it," says Woodward, who's also a cybersecurity adviser to the EU's law enforcement intelligence agency, Europol. "That is not the sort of thing a private hacker would do - they tend to attack from outside."
2. Ditch Outdated Devices
One target of an Equation Group attack tool - named BENIGNCERTAIN - are Cisco PIX devices. But intelligence agencies are not the only ones targeting
vulnerable equipment. Botnet-building cybercriminals have also been exploiting known vulnerabilities in PIX devices located in a number of countries, including Russia and Pakistan, according to U.K.-based security researcher Kevin Beaumont.
That's despite Cisco having stopped selling PIX devices in 2009 and ceased supporting PIX devices altogether in 2013.
As of Aug. 19, however, British security researcher Mustafa Al-Bassam counted at least 15,000 PIX devices still being used, including 9,000 in Russia and nearly 3,000 in the United States.
There's actually over 15,000 Cisco PIX firewalls online today vulnerable to BENIGNCERTAIN, most of them in Russia. pic.twitter.com/rmwHBEyGW9
Clearly, organizations are not heeding vendors' advice to discard older, unsupported IT equipment. Culprits include the recent global recession, as well as information security - and IT - still being viewed by many organizations as being a cost center, says Brian Honan, who heads Dublin-based cybersecurity consultancy BH Consulting. And that leads to an "if it ain't broke, don't fix it" mentality around replacing software and hardware.
"CISOs need to get their senior management to focus on the benefits of a mature cybersecurity program and not on the costs," says Honan, who also advises Europol on cybersecurity matters.
"There are other areas in the business where costs cannot be ignored, such as health and safety and fire prevention, where legally companies have to replace outdated or end of life equipment," he adds. "However, we do not yet have that type of mature environment within cybersecurity that results in CISOs having to make a strong business case for more investment in security."
Security experts say that most products, once they lose support, can no longer be trusted to be secure. "The point when older kit should be jettisoned is simple - when it is no longer supported 'properly,'" University of Surrey's Woodward says. "I would also say that if some fundamental flaw is found in the software or hardware then it should also be binned. It is very easy for people to forget equipment that is performing a vital security task and at that point you are the weakest link."
That doesn't mean vendors should have carte blanche to stop supporting older products just because they're trying to sell customers new ones. "You should expect equipment to last for a decent amount of time, and it is part of due diligence to ask vendors expected life of the equipment and software," Woodward says.
3. Enterprises Must Defend Themselves
The Equation Group leak is a reminder that intelligence agencies' missions are not to report flaws to technology vendors. As Tanji writes in a blog post, "Intelligence agencies are not here to defend your enterprise."
Tanji says intelligence agencies "exist to gather information, analyze it, and deliver their findings to policymakers so that they can make decisions about how to deal with threats to the nation. Period."
So don't expect intelligence agencies to take responsibility for vendors selling secure products with bug-free code. For that, enterprises must hold their vendors directly accountable.
It absolutely blows my mind that a handful of people on Twitter had to drive the research on #BENIGNCERTAIN, push for vendor acknowledgement
4. Treat All Vendors With Caution
The Equation Group toolset dump - as well as exploitable flaws in firewall vendors' products - are reminders that no piece of hardware or software can be treated as 100 percent secure. So organizations should subject all vendors and products to a risk assessment to help them pick the best and most secure tool for the job, Honan says.
"Companies should consider a layered defense approach to their security whereby they use security solutions from different vendors in order to continue to provide some level of security in the event one layer fails or is compromised," he adds.
5. Continuously Monitor Your Networks
Clearly, any component of IT infrastructure - especially firewalls and VPN appliances - is a target for enterprising attackers, be they foreign intelligence agencies, cybercrime gangs or teenagers with too much time on their hands. "If you run a firewall installation at a large organization, now would be a good time to start logging incoming traffic for oddities," British researcher Al-Bassam says via Twitter.
Honan, who founded Ireland's first computer emergency response team, says monitoring is a must. "CISOs must implement continuous monitoring of all systems to know what normal operations look like on their network, so that any unusual usage patterns can be examined further to indicate if there is a compromise," he says.





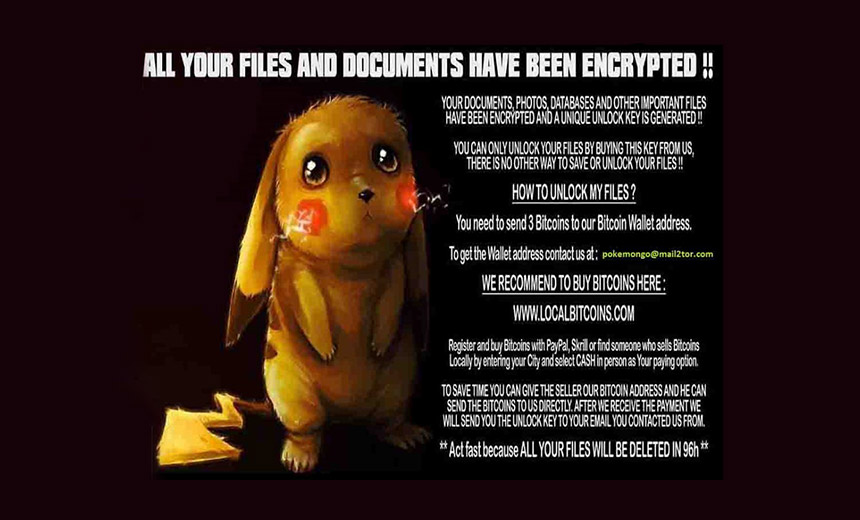 DetoxCrypto PokemonGo variant's ransomware lock screen. Source: MalwareHunterTeam
DetoxCrypto PokemonGo variant's ransomware lock screen. Source: MalwareHunterTeam