Breach Notification , Breach Response , Data Breach
The Breach That Supposedly Isn't a Breach California Company's Bungled Response Risks the 'Streisand Effect'
Most companies don't ever want to be contacted by Troy Hunt, the Australian data breach researcher who created Have I Been Pwned, a popular service for figuring out if your data has been leaked. Hunt, an amiable guy, often brings bad news.
See Also: API vs. Proxy: Understanding How to Get the Best Protection from Your CASB
He works closely with some journalists, including me, to navigate the choppy waters that can come with notifying companies. It's not an easy game: You don't want to publish a story that wrongly identifies a company as being a victim of a breach. But at the same time, people should be notified as soon as possible if their data has gone walkabout.
The handling of a recent data breach - the details of which are still unfolding - by Oakland, Calif.-based web services company Regpack provides a look into how the discovery and disclosure of a breach can turn into a real train wreck.
Tweet Leak
In mid-July, Hunt came across a now-deleted tweet from a known trader of leaked data with a link to a 1.6GB file. The file contained more than 100,000 names, email and postal addresses, last four digits of payment card numbers, three-digit card verification values, expiration dates and amounts paid for services. The tweet claimed the data came from BlueSnap, a payment services provider founded in Israel.
But Hunt says a close analysis of the data showed that Regpack might be responsible. Regpack develops web-based registration forms that can be integrated into websites. The forms also accommodate credit card data, which Regpack passes on to BlueSnap for payment processing. It initially looked like BlueSnap was breached. But information in the leaked files, as well as full invoices available online, showed strong indications Regpack may be the source, according to Hunt.
In late August, I queried both companies, and neither said they were breached. Meanwhile, Hunt had reached out to verified subscribers of Have I Been Pwned whose email addresses appeared in the leaked file. Verified subscribers are those who have confirmed their email addresses and are good sources that Hunt uses to try to confirm the veracity of a breach. It's a sensitive query, but many people confirmed their details to Hunt, including CVV2s and elements of the last four digits of their payment cards. Clearly, this was a breach.
But the situation then stalled. I was reluctant to write a story without firm confirmation from either company, but Hunt was concerned that the victims were never going to be contacted. Hunt decided to go public on Sept. 13 with his research on his blog. The tree had been shaken and information trickled out. But rather than clarity, Regpack is making the situation more confusing, and it's not clear when the more than 100,000 victims may be notified.
Exposed, Not Compromised
Regpack has stopped answering my queries, but in a statement supplied to Hunt, the company acknowledges it was the source of the leaked information. Its explanation, though, is lacking - the company says the leak was the result of a developer's error.
Log files revealed that a Regpack employee had decrypted some of its payments data for analysis, a practice that likely clashes with PCI-DSS compliance, the hefty set of security requirements merchants are supposed to follow. The company maintains its servers are secure.
"We identified that a human error caused those decrypted files to be exposed to a public-facing server, and this was the source of the data loss," the statement says.
It also contends there wasn't a breach: "Neither Regpack nor BlueSnap had our systems breached." The phrasing is confusing, and what Regpack probably meant to say is that its systems were not subject to a cyberattack. Even if the cause was an internal error, it's still a breach.
"I think they're doing a lot of damage and missing language that could both inform people properly and mitigate damage to their organization," Hunt says. Regpack is essentially risking the "Streisand effect," the term for trying to obfuscate or hide an issue, inadvertently making it more prominent, he says. (The Streisand effect is named after singer Barbra Streisand, who in 2003 attempted to suppress photographs of her private residence, but only succeeded in attracting additional attention to the matter.)
Regpack has started notifying its customers, and I obtained one of the emails the company is sending out. Similar to its public statement, Regpack says it wasn't breached, arguing that a breach "is a situation where someone gains access to our servers and databases and steals information."
Hmmm. Isn't that what happened? The notification then tries even harder to advance Regpack's argument.
"A good analogy would be that the office containing your data is totally safe and impenetrable and is guarded 24/7 by multiple systems and security guards," writes Edgar Carrasco, vice president of business development. "Unfortunately, while leaving work, someone dropped a file out of their bag and someone passing by took it. Hence, the office (our servers), were not compromised but information was exposed."
Carrasco's notice also contains a suggested email that Regpack customers should send to their customers whose personal data was exposed. Notably, it neglects to spell out all the data elements that were exposed.
"They're still missing really vital elements of the incident in their communication," Hunt says.
One Victim's Tale
One of the victims whose data was exposed is Thomas Bacon, an Austin, Texas-based web designer and developer. He used a Regpack-powered website to register his son for summer camp. Bacon contacted the summer camp to let them know of the breach. He claims that the camp wasn't happy because Regpack initially downplayed the impact of the leak. The camp, however, has now received the email notice from Carrasco.
Bacon, who has an interest in computer security, has already taken action. "I've cancelled my card," he says in a phone interview.
Although the leak doesn't contain full card numbers, Hunt argues that the last four digits are still critical information that could be used by attackers. Companies often ask consumers for the last four digits of their card as part of oral authentication questions over the phone. Another problem is that Regpack should not have been storing the CVV2 numbers, a practice prohibited by PCI-DSS.
"That may get them in a lot of trouble," Hunt says.
Notification could be messy. Regpack will have to let its website customers know which of their clients are affected by the breach, meaning it will have to carefully parse 1.6GB of data to make sure no one is left out. At least 899 services that used Regpack are affected by the breach, Hunt contends.
"The sites that use Regpack really haven't done anything wrong," Hunt says. "Regpack has clearly done multiple things wrong. When you're dealing with payments, the trust in the brand is really paramount. This is inevitably why they're being really cautious in their communications. They don't want to erode trust."
But it may already be gone.
The Regpack data has been in Have I Been Pwned since Sept. 13, so it's easy to figure out if you're affected. If so, it's probably wise to cancel your card.


 Photo:
Photo: 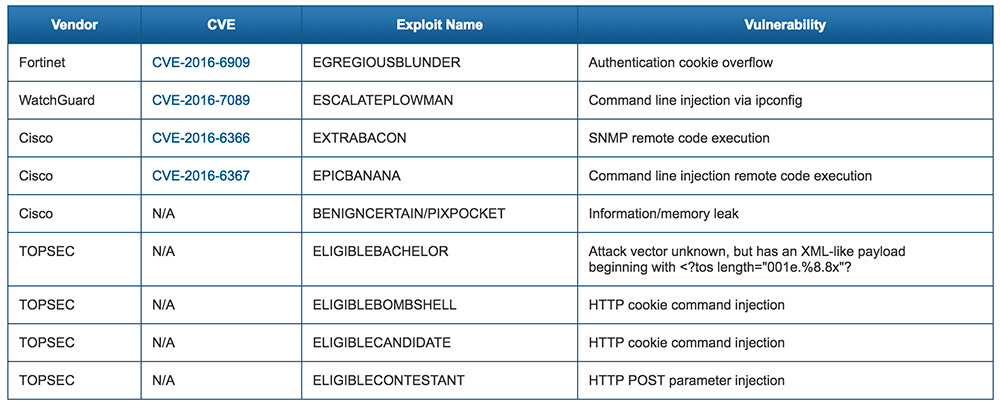 Source: US-CERT6 Network Admin Essentials
Source: US-CERT6 Network Admin Essentials

 Sergei Skorobogatov demonstrates his "chip off" procedure. (Source: Youtube)
Sergei Skorobogatov demonstrates his "chip off" procedure. (Source: Youtube) Photo:
Photo: