In Development
Receive Invite When Available
Receive Invite When Available
In the wake of the controversy over Hillary Clinton's use of private email servers, President Obama voices his concerns about the state of federal government IT security in this edition of the ISMG Security Report.
You'll also hear:
The ISMG Security Report appears on this and other ISMG websites on Tuesdays and Fridays. Be sure to check out our July 5 and July 8 reports, which respectively analyze the latest victim of hackers making fraudulent SWIFT transfers and the fierce battle between endpoint protection product makers. The next ISMG Security Report will be posted Friday, July 15.
Theme music for the ISMG Security Report by Ithaca Audio under Creative Commons license.
Messaging , Risk Management , Technology
Commenters Weigh In on Clinton's Email Practices Interview Creates Lively Debate on Security vs. Convenience
Those commenting on my recent interview with Purdue University Computer Science Professor Eugene Spafford about Hillary Clinton's email server controversy are divided over whether users will devise ways to circumvent systems safeguards to do their jobs more effectively.
See Also: 2016 Enterprise Security Study - the Results
"Where security policy isn't in sync with the way people work, policy workarounds and 'exceptions' become the rule," Scott Petry, CEO and co-founder of Authentic8, a provider of secure browsing, writes in the podcast's comments section.
But a commenter identified as DJL - David J. Lineman, president of information security and data privacy products and services provider Information Shield - writes that convenience "is an extremely weak justification for a major violation of security policy. You can be sure that if the CSO of a Fortune 100 company had a personal server in her basement that stored trade secrets, and there was a known breach, she would be terminated."
 Hillary Clinton checks her email.
Hillary Clinton checks her email.Clinton, the presumptive Democratic Party nominee for president, used private email servers while serving as secretary of state. An FBI investigation found that Clinton, despite her denial, knowingly used the private servers to transmit a few messages marked classified. But the Justice Department declined to prosecute, which dismayed many of her political critics.
Spafford, in the interview, lamented that the debate surrounding the use of private email servers concentrated on politics and failed to focus on why such things happen. "I think this is more politically driven than it's functionally driven because if it were functionally driven, people would say, 'What are the root causes, and how do we fix them?' rather than trying to assign blame."
A commenter identified as Jennifer WhoDat Farwell, agrees, writing that it's irrelevant whether Clinton felt what she did was right or wrong. "Humans have such a high, innate risk tolerance that we will take all sorts of risks for the sake of expediency and achievement," Farwell writes. "That is how we got to the top of the food chain. Instead of debating whether she made a typical human error (which she did), let's have a productive conversation about using technology to help humans be more productive without engaging in risky behaviors we are not programmed to avoid."
 Eugene 'Spaf' Spafford
Eugene 'Spaf' SpaffordSpafford contends that security professionals should do more to create secure systems that can help individuals perform their jobs efficiently. It's a point picked up by Wendy M. Grossman, a journalist who previously blogged about this matter. "HRC had requested a secure Blackberry and been refused," Grossman writes in response to my interview. "I know security is important, but it's incredible to me that the security people apparently thought their ideas about technology should take precedence over what the U.S. secretary of state was telling them about her working needs. Collaboration with people who need to do their jobs needs to be a top priority in doing good security."
"Baloney," responds another commenter using the handle voice-of-experience. "Convenience nor ignorance had nothing to do with why this private server was setup. HRC did not want her emails to be discovered as they would expose her corrupt activities."
Commenter Ms NoWay Jose contends "we are heading down a slippery slope of failures" if we allow convenience to trump security. "Security is security; it's not like hundreds of millions of identities haven't been stolen worldwide. It's not like we don't have to worry about intelligence leaking because both of these are happening far too much from incompetence and security ignorance. Sorry, but the security of our national intelligence is far more important than the convenience of someone who doesn't want to follow the laws. If you can't handle the job, then get out."
One question that seems unanswered is why the higher-ups responsible for State Department IT security didn't put a stop to Clinton's use of private email servers if they posed a security risk. "Didn't her private email server have a different domain suffix than the usual State Department ones?" asks Patrice Boivin, CEO of Orion Software, a provider of software to the rental industry. "Why in the world didn't anyone notice this or do something about it is my question. Bureaucracies are full of organizational chart boxes where the people in the boxes are either incompetent, running amok, or not allowed to make the decisions that go with their job descriptions. Someone must have noticed; question is, why wasn't this nipped in the bud?"
Commenting on the blog's premise focusing on developing secure systems that also facilitate the work habits of users, Jay Wack writes: "The situation is all the more frustrating because there are solutions and standards available that satisfy all concerned from an ease of use perspective and from the security perspective. ANSI, a national peer review process, has published several standards directly applicable. X9.69 and X9.73 specifically. Designed for secure information sharing. A problem for all of us."
These are just a sampling of the many comments we received on my Spafford interview. It's not too late for you to join this discussion. Post your comments below.
Cloud Computing , Legislation , Technology
Backers Portray Cloud as a More Secure Alternative to Legacy Systems Rep. Will Hurd, R-Texas, a co-sponsor of the Move IT Act.
Rep. Will Hurd, R-Texas, a co-sponsor of the Move IT Act.A bipartisan group of lawmakers has introduced identical bills in the House and Senate to encourage agencies to use secure cloud computing services as an alternative to continued reliance on legacy systems, which some government officials and IT security practitioners say puts data at risk.
See Also: Achieving Advanced Threat Resilience: Best Practices for Protection, Detection and Correction
The Modernizing Outdated and Vulnerable Equipment and Information Technology Act - known as the Move IT Act - aims to enhance cybersecurity while reducing wasteful spending by hastening the federal government's transition to cloud computing.
"Using these old systems makes data housed by federal agencies more vulnerable to digital attacks, and it's a gigantic waste of taxpayers' money," says one of the bill's sponsors, Rep. Will Hurd, R-Texas. "There is a better way to do this. This legislation is an outside-the-box, innovative solution and is another step forward in modernizing our digital infrastructure."
About three-quarters of the federal government's annual $80 billion IT budget is devoted to operating and maintaining existing systems, and the amount earmarked for investments in new systems has plunged by $7.3 billion since 2010, according to a Government Accountability Office audit published earlier this year (see ISMG Security Report: To Whom Should CISO Report?).
David Powner, GAO director of information management issues, questions whether the government gets value from investing so much money in legacy systems. "Not only are they old and they're difficult and complex to maintain, but you also have security issues because you've got hardware and software that are no longer supported, and there are significant security vulnerabilities associated with these systems," he says.
In April, the Obama administration unveiled a program to spend $3.1 billion next year to seed a fund to improve cybersecurity by modernizing federal information systems (see White House Proposes $3 Billion Fund to Modernize Federal IT).
The Move IT Act instead would require each agency to establish an IT modernization and working capital fund, which could be financed through redirecting funds intended for the operation and maintenance of legacy systems.
Some IT security experts see cloud services as offering a more secure computing environment. "If you use modern, advanced technologies instead of trying to drag forward your old concepts into the new world, you can save money and lower your risks at the same time," says Tom Patterson, chief trust officer at systems integrator Unisys.
Robert Bigman, an independent IT security consultant who served for 15 years as CISO at the Central Intelligence Agency, contends that "for a few more dollars" federal agencies and other enterprises using cloud services would receive "better configuration security, better auditing, better identification and authentication and better encryption" than what legacy systems furnish.
Cloud services are not fundamentally more or less secure than in-house systems. If organizations "maintain their software and their hardware in an up-to-date manner, and they have good security around their data center, then the cloud is no more secure than they are," says Mac McMillian, CEO of the security consultancy CynergisTek. "But if they're having trouble doing that, or if they're not able to do that, then the cloud may present a better option, and a more secure option."
David McClure, who once led the federal government cloud-vetting program known as FedRAMP - the Federal Risk and Authorization Management Program - stresses that it's critical for enterprises to have an understanding of services, applications, interfaces and networks of any IT architecture, especially those hosted by third parties, such as cloud service providers, to grasp their security weaknesses and vulnerabilities.
And employing cloud services could present a challenge for enterprises in keeping track of their critical assets.
It's a problem the Defense Department faces. "Without accurate and complete inventories of cloud computing systems, [DoD] agencies did not know the extent to which their data resided outside their information system boundaries and were, therefore, subject to the inherent risks of cloud systems," Carol Gorman, DoD assistant inspector general, readiness and cyber operations, said in an audit issued in December (see Tracking Cloud Services: An Essential Security Step).
The Move IT Act aims to bolster FedRAMP, which facilitates the certification of cloud service providers that qualify to be used by federal agencies. The legislation would require the Office of Management and Budget and the General Services Administration, which administers FedRAMP, to streamline and accelerate the FedRAMP accreditation process for cloud service providers. The bill would establish a public-private liaison group to facilitate information sharing and identify best practices, including security, for cloud service providers and the FedRAMP office.
The legislation also would require OMB and the National Institute of Standards and Technology to establish performance metrics for the FedRAMP process of authorizing cloud service providers to sell cloud services to federal agencies.
The bill also would require agencies' CIOs to assess cloud computing opportunities and issue policies and guidelines for adopting a standardized approach to assess the security of cloud products and services.
One of the bill's sponsors, Democratic Rep. Gerry Connolly of Virginia, sees great potential for cloud services as a replacement for unsecure older systems. "We have not yet fully realized the potential for cloud computing to transform the way the federal government uses IT and to spur the transition away from hard-to-maintain, unsecure legacy systems," she says.
Breach Preparedness , Cybersecurity , Data Breach
Arbor's Sam Curry on Re-Thinking How We Approach CybersecurityAs CSO and CTO of Arbor Networks, Sam Curry is in a rare position: He can set security strategy and then go out and find the tools to execute it.
See Also: Detecting Insider Threats Through Machine Learning
"It's an unusual situation," Curry says. "There's no hypocrisy here. I can say I need something, and then I have to deliver it, and I only have myself to hold accountable."
Part of Curry's ongoing challenge is to find the right tools to fight cybercrime. But a big part of it is also to ensure that the right people are focused appropriately on the task.
"The first problem we have is: How do we free up more discretionary budget to invest in new technologies that can actually stop the bad guys?" Curry says. The second issue then becomes: How do we get people to use these technologies? "How do we help them catch faster and with higher reliability the bad guys before information is affected or lost?"
In an interview at the Boston Fraud and Breach Prevention Summit, Curry discusses:
His unique CSO/CTO role; How to account for the human factor in cyber conflict; New ways to envision a cybersecurity strategy.Curry has spent his career focused on the intersection of deep technology and solving customer problems. As Arbor's chief technology and security officer, he leads the development and implementation of the company's product strategy and innovation roadmap. Previously, he held the roles of senior vice president of research and development and CISO at MicroStrategy. Prior to that, Curry held a number of roles at RSA, including general manager, CTO and senior vice president of product management. He has also held a number of leadership roles at McAfee and Computer Associates, among others, and has founded two companies. A frequent speaker and widely quoted subject matter expert in technical and industry forums during the course of his career, Curry has more than 20 patents and is on the board of several companies and organizations.
Anti-Malware , Data Loss , Encryption
Ransomware Variant Deletes Everything 'Ranscam' Malware Pretends Bitcoin Ransom Will Recover Nuked Files
How low will ransomware go?
See Also: Creating a User-Centric Authentication and Identity Platform for the Healthcare Industry
Security researchers say there's been a flood of new malware variants reaching the market. Cybercriminals are eager to cash in on the profit potential afforded by ransomware - many targets are easy pickings. And the developers who create the malware are eager to turn a profit by selling their attack code to more would-be users.
Greater competition inevitably leads to "innovation," and in this case it almost always comes at the expense of victims' data.
You might think that encrypting a victim's files en masse, deleting the originals and then demanding bitcoins for the decryption key is bad enough. But don't forget cybercriminals targeting not just individuals but also organizations providing critical services, including healthcare facilities and the police. Another wrinkle, of course, is that even the most profit-oriented developer-cum-criminal may fumble their crypto, thus leaving files unrecoverable.
More recently, some ransomware developers have opted for shock value, such as a variant named Jigsaw that takes its inspiration from horror movie "Saw" and begins deleting a user's files while they watch.
What most ransomware victims would find truly evil, however, is malware that simply deleted all of their data, then pretended it was encrypted until victims paid the ransom.
Enter Ranscam, which represents perhaps the most lazy - and crass - type of ransomware built to date, in that it seeks to cash in on ransomware fears while delivering nothing but scorched-earth tactics, according to Edmund Brumaghin and Warren Mercer of Cisco's Talos Security Intelligence and Research Group.
"It lacks complexity and also tries to use various scare tactics to entice the user to paying," such as informing users that their files have been moved to a "hidden, encrypted partition," and then displaying a ransom message that persists even after reboots, the researchers say in a blog post. The message also says that every time they click the payment link on the ransom note but don't pay, some of their files will get deleted, the post notes.
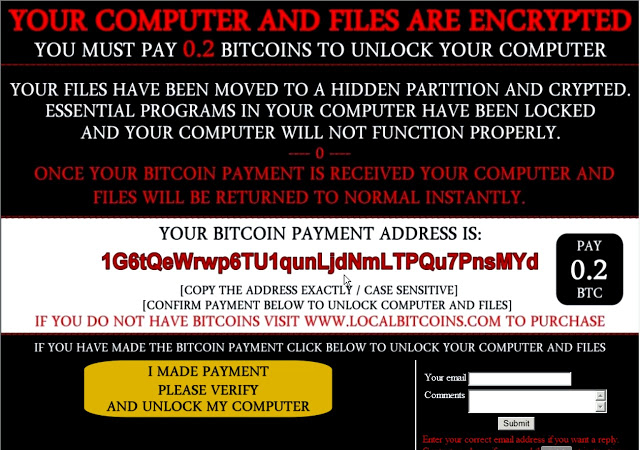 Ranscam promises to decrypt a locked PC in exchange for 0.2 bitcoins (about $135), but the supposedly encrypted files have already been deleted. (Source: Cisco Talos)
Ranscam promises to decrypt a locked PC in exchange for 0.2 bitcoins (about $135), but the supposedly encrypted files have already been deleted. (Source: Cisco Talos)
But that's a lie - the files are already gone, the researchers say, noting that the ransomware doesn't include any encryption or decryption capabilities. Instead, they say, the .NET executable malware is designed to use the Windows Command Processor to run a batch file that deletes the contents of designated folders - largely focused on user-generated content - as well as core Windows files that get used for restoring the system, shadow copies of files and registry keys associated with booting into safe code, among other files.
After that, the malware displays the ransom note, but by then it's too late. "The author is simply relying on 'smoke and mirrors' in an attempt to convince victims that their files can be recovered in hopes that they will choose to pay the ransom," the Talos researchers say. "The lack of any encryption - and decryption - within this malware suggests this adversary is looking to 'make a quick buck' - it is not sophisticated in any way."
It's not clear how widespread Ranscam might be, or how attackers have been sneaking it onto victim's computers. Also, it's not the first virus to outright delete data. But in recent years, such attacks have been relatively rare, aside from a handful of wiper malware attacks that targeted organizations in the Middle East or South Korea, plus the attack launched against Sony Pictures Entertainment in 2014.
The takeaway from threats such as Ranscam - or any other malware that can wipe a hard drive - is simple: Preparation is everything (see No-Brainer Ransomware Defenses).
On that front, the U.S. Computer Emergency Response Team, which is part of the Department of Homeland Security, this week updated its recommendations for battling ransomware. In particular, US-CERT recommends:
Backups: Whitelisting applications: Updated operating systems and software: Anti-virus: Least privilege: Killing email-borne macros: Don't click:Simply keeping good backups would take a big bite out of ransomware attackers' profits. "Not only does having a good backup strategy in place help ensure that systems can be restored, it also ensures that attackers are no longer able to collect revenue that they can then reinvest into the future development of their criminal enterprise," the Cisco Talos researchers note (see Please Don't Pay Ransoms, FBI Urges).

The theft of $2.2 million from dozens of ATMs in Taiwan, executed using malicious software, defies a years-long effort by banks and software vendors to strengthen the security controls of ATM fleets.
See Also: Achieving Advanced Threat Resilience: Best Practices for Protection, Detection and Correction
Investigators suspect two Russian nationals may have remotely commanded a specific kind of ATM made by Wincor-Nixdorf to dispense thick wads of cash, Reuters reports. As a precaution, some of the country's biggest banks suspended withdrawals from 1,000 ATMs of the same kind.
Since 2009, researchers have warned that hackers were developing malicious software for ATMs. The malware is designed to cause ATMs to disgorge bills, known as jackpotting, or collect details of payment cards used at a machine.
The most famous jackpotting demonstration came in July 2010 at the Black Hat security conference. The late security expert Barnaby Jack exploited security flaws in two ATMs, causing the machines to spew a flurry of bills onstage.
The ATM thefts come as the banking industry has faced increasingly bold and well-planned attacks. Bangladesh Bank lost $81 million in February after hackers compromised its credentials for the SWIFT interbank payment system (see Bangladesh Bank Attackers Hacked SWIFT Software ).
Then in May, fraudsters in Japan stole $19 million from South Africa's Standard Bank in a quick, coordinated attack using counterfeit cards at ATMs (see Lessons From ATM Cash-Out Scheme in Japan).
Three types of malware were used in the Taiwan thefts, which affected First Bank, Reuters reported, citing Ministry of Justice's Investigation Bureau. The dispensing of the cash could have been triggered by a mobile phone, a laptop or a hacked PC at First Bank, the bureau told the news agency.
The malware wasn't named, but the description could fit ATM malware called Ploutus. Once the malware is installed on an ATM, an attacker can command the machine to dispense cash by sending a text message, according to a May 2014 blog post by Symantec.
ATMs are widely viewed as vulnerable because nearly all run aging software. They're complex, networked devices that have many potential weaknesses if not carefully configured, updated and physically secured.
About 90 percent of the world's ATM machines still run Windows XP, according to Kaspersky Lab. Microsoft stopped providing security updates for XP in April 2014, although extended support was available for some special embedded versions through this year.
Steve Wilson, a principal analyst with Constellation Research, says critical infrastructure - from ATMs to medical devices to internet-connected vehicles - should simply not be built using commercial operating systems that "are barely adequate to run word processors.
"It's just asking for trouble," he says. "It's amazing that this [ATM malware thefts] doesn't happen more often."
When Microsoft ended support for Windows XP, it posed a major problem for ATM vendors. The manufacturers had to ensure their ATMs were compliant with the Payment Card Industry Data Security Standard and were not vulnerable to malware.
Most ATM manufacturers continued to use Windows XP, bolting on other security software while trying to lock down the OS to protect cardholder data. Others migrated to Windows 7.
As the deadline for the end of XP support approached, Wincor-Nixdorf released software called PC/E Terminal Security, which could be layered on top of XP. The security software ensured ATMs were PCI-DSS compliant and hardened the OS against unauthorized access.
Wincor-Nixdorf's product catalog gives insight into the operating systems its ATMs currently support. The ProCash 280, for example, lists its compatible software as Windows XP Professional SP3, Windows POSReady 2009 and Windows 7.
The model of the ATM breached by the hackers in Taiwan has not been identified, and Wincor-Nixdorf officials couldn't immediately be reached for comment.
There are a variety of ways to attack an ATM. Installing malware would require either physical or remote access to the ATM's computer. ATMs generally have two cabinets: one that contains the cash, which is heavily secured, and the other that contains the electronics.
Access to the cabinet containing the ATM's computer is often protected by a single lock. It's not uncommon for the same key to open an entire fleet of ATMs to make it easier to access the devices for servicing. If that key is obtained, an attacker could open up the ATM and install malware by slipping a USB key into an open port or by using a CD-drive.
Some manufacturers guard against this type of attack. Triton Systems, which makes stand-alone ATMs, only allows trusted executables to run, a process known as whitelisting, says Henry Schwarz, the company's software projects director. The digital signatures of any updates for the ATM's software are verified as well. If an attacker breached the ATM's door, it means that unauthorized code should not run.
ATMs need a network connection in order to communicate with banks, so remote attacks are also a possibility. A network configuration mistake could be all that a hacker needs to get in. Some ATMs have wireless modems or Wi-Fi enabled and communicate over the public internet. Others have dedicated connections.
"There's all sorts of options, and some are more secure than others," Schwarz says. "In the trade-off between convenience and security, a small sacrifice in security can be all that an attacker needs to get their foot in the ATM's door."
In just two years' time, RSA analysts have seen a 170 percent rise in incidents of fraud via the mobile channel. What's behind the spike, and what can security leaders do to help their organizations and customers curb fraud losses?
See Also: 2016 Enterprise Security Study - the Results
Angel Grant, a principal manager at RSA, discusses the surge and how to respond to it in this video interview.
To put the 170 percent increase in some context, Grant offers color commentary: "170 percent is pretty dramatic, and when you break it down today, the amount of fraud transactions we see ... 60 percent of all the fraud transactions we see come from the mobile channel."
And within that 60 percent, she adds, the latest trend is to see more fraudulent transactions via mobile apps rather than mobile browser.
Beyond the rise in mobile fraud, Grant also is concerned about recent ransomware incidents, as well as the growing trend of fraudsters targeting specific individuals. "A lot of times, individuals are being targeted in their personal lives, so they can be [pursued] in their professional lives, too, so we're seeing those types of blended attacks," she says.
In an interview at the Boston Fraud and Breach Prevention Summit, Grant discusses:
The latest fraud trends; Four best practices to fight fraud; How to empower users and customers to fight back against fraudsters.Grant is a principal manager in RSA, The Security Division of EMC's Identity Protection and Verification group. She has more than 15 years of experience in the security and financial services industries and is responsible for a variety of initiatives which protect organizations against fraud and identity theft. Prior to joining RSA, she was an online banking senior product manager at P&H Solutions, where she helped launch one of the industry's first online corporate cash management applications. Previously, she managed a mortgage division inside sales and service team for a large financial institution.