
SentinelOne, one of a batch of vendors using machine learning to conquer malware, says it will not integrate its malware detection engine into VirusTotal service. CEO and co-founder Tomer Weingarten claims the investment wouldn't provide a worthwhile return right now, although the company is open to working with Google, which runs VirusTotal.
See Also: Avoid 75% of all Data Breaches by Keeping Privileged Credentials Secure
Security companies use VirusTotal to get a heads-up on new malware samples via a threat feed. Malware can also be uploaded to get a quick idea of how more than 50 vendors might be detecting a new sample. A subscription package also lets companies see why a vendor decided if something was malware, via its so-called "ratings" feature.
In a controversial move, VirusTotal said it would block vendors that have not integrated their anti-virus engines into the scanning service to access the ratings feature. The change came after long-established security vendors alleged that startups were leaning on those ratings to keep their own products up to speed.
Weingarten, meanwhile, claims the way the scanning service is configured doesn't accommodate how SentinelOne actually works.
"The infrastructure needs to change, and once it happens and once we can actually work with that, I would say 'why not?'" Weingarten says. "The investment we need to make in order to kind of try and work with them is not something ... we're willing to afford right now."
By contrast, CrowdStrike and Invincea recently said both would allow their technology to be integrated into VirusTotal. Another much talked-about startup, Cylance, didn't respond to a query about whether it plans to make a similar move (see CrowdStrike, Invincea Integrate With VirusTotal).
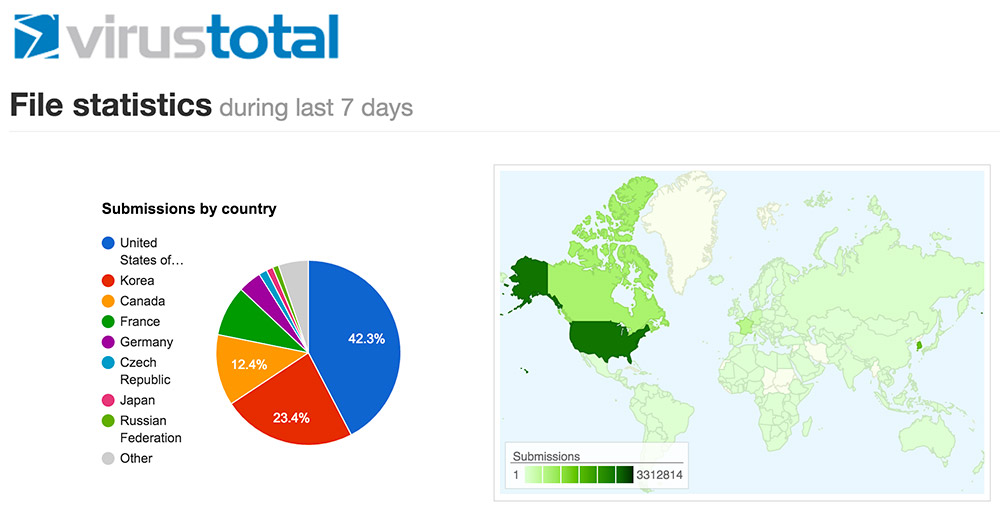 VirusTotal allows anyone to submit a file or URL for scanning, to see if it appears to be malicious.
VirusTotal allows anyone to submit a file or URL for scanning, to see if it appears to be malicious.
Debate: Static vs. Dynamic
SentinelOne's product has several components. Its Dynamic Behavioral Engine uses machine learning - which can also be referred to as statistical analysis - to determine whether something is likely malicious.
The Dynamic Behavioral Engine monitors all processes and applications from the operating system's kernel, including a computer's memory, network connections, input/output traffic, system calls and API calls. It then uses algorithms to classify every kind of behavior by processes to determine if those processes might be malicious. The decision by those algorithms is made on an endpoint, so the computer could be offline and the detection capabilities wouldn't be affected.
SentinelOne's Windows and Mac products are a bit different. As a backstop on Macs, the product also uses data from the cloud, flagging suspicious binaries before they run based on factors that have been seen in the past. Weingarten says, however, that no signatures are used in that process.
Startup security vendors have waged aggressive marketing campaigns criticizing older companies for relying too heavily on signatures - descriptions of known malware files - for deciding whether a file should be immediately quarantined. Signatures are faulty in the sense they're created after something has already attacked a computer. Malware authors often re-compress the same attack code to make it look different while leaving it functionally intact and enabling it to evade vendors' lists of known malware signatures.
But old-guard companies such as Symantec and Trend Micro have for years also employed behavioral analysis techniques to identify malware. It's part of why those companies have been irritated by some of the newer startups' marketing techniques and have suspected unfair play when it comes to utilizing VirusTotal's data. Trend Micro made some of its most pointed accusations just after VirusTotal announced its changes.
No Problem for CrowdStrike
Explaining why SentinelOne is currently opting to not integrate with VirusTotal, Weingarten says that VirusTotal would need to be able to accommodate executable code for his product to work effectively with it. He suspects that some newer security vendors do not have their entire anti-virus engine integrated with VirusTotal, but rather a command-line static analysis engine, which would meet the service's new requirements.
CrowdStrike, though, doesn't appear to have the same problem, or else has worked around it. The company explained in an Aug. 25 blog post how its Falcon Host scanner has been integrated. Although it's not present just yet on VirusTotal, Falcon Host will give a "confidence score" related to whether something is malware or not. The score is calculated after analyzing thousands of aspects of a file or executable.
"If we detect a file, we return a confidence score - there is no coarse yes/no decision as with traditional, signature-based AV," wrote Sven Krasser, CrowdStrike's chief scientist. "Presently, the score ranges from 60 to 100. The higher the score, the more certain we are that the file is indeed malware."
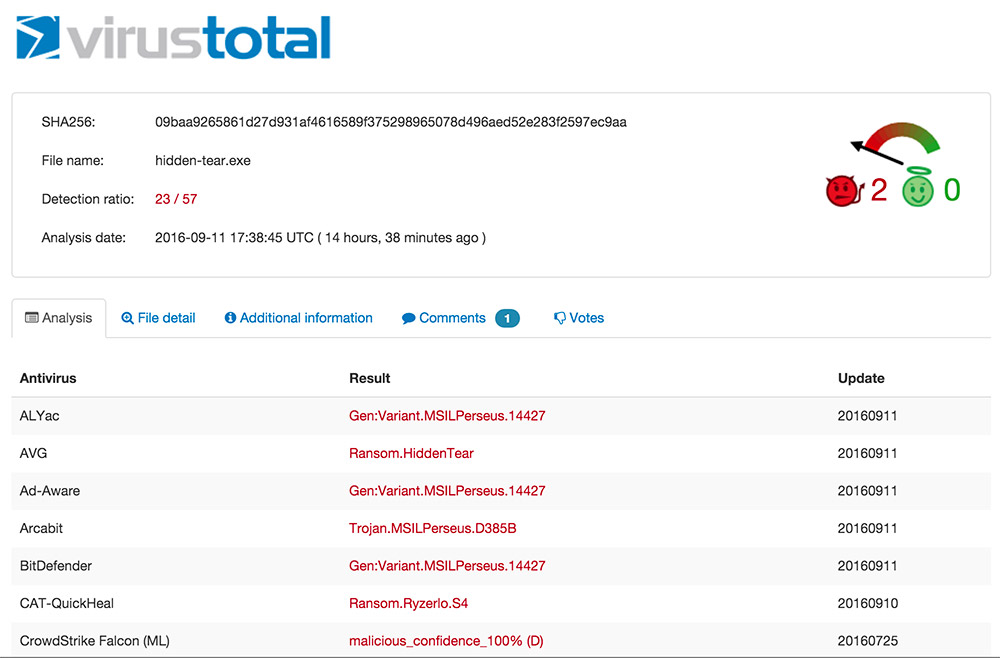 VirusTotal says its service "checks suspicious samples with several anti-virus solutions and helps anti-virus labs by forwarding them the malware they fail to detect," but should not be used to compare anti-virus products, which often include complementary defenses that it doesn't take into account.
VirusTotal says its service "checks suspicious samples with several anti-virus solutions and helps anti-virus labs by forwarding them the malware they fail to detect," but should not be used to compare anti-virus products, which often include complementary defenses that it doesn't take into account.
Machine Learning
Weingarten says that despite SentinelOne's decision, it's still on friendly terms with VirusTotal. SentinelOne also still pays for a subscription to the malware feed.
Not having access to the ratings doesn't matter since the company didn't depend on that information, he says. VirusTotal's malware feed goes to SentinelOne's machine learning clusters, which analyzes malware, malicious documents, suspicious scripts and exploit code. The company then updates its algorithms on endpoints once or twice a month via a slim, 100K file.
"We profile hundreds of thousands of files and attack code samples on a daily basis," Weingarten says.



 Photo:
Photo: 
 U.S. gymnast Simone Biles at Olympic Games Rio 2016. Photo:
U.S. gymnast Simone Biles at Olympic Games Rio 2016. Photo: 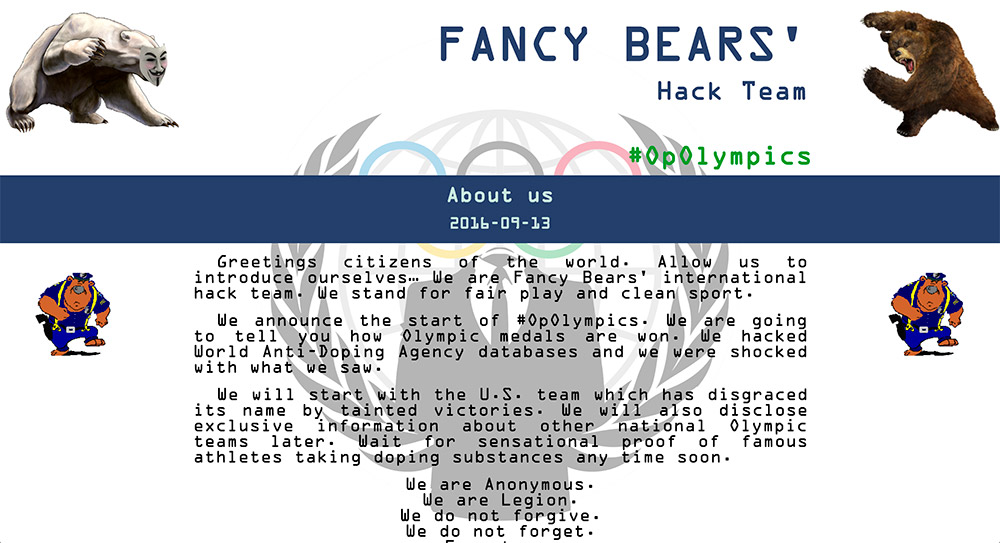 A group calling itself Fancy Bears' Hack Team says the leaks are the start of what it's calling #OpOlympics.
A group calling itself Fancy Bears' Hack Team says the leaks are the start of what it's calling #OpOlympics.